Intel CPUs Suffer Performance Hit From New Spectre-v2 Mitigations
Branch History Injection (BHI), a new flavor of the Spectre-v2 vulnerability that affects both new and old Intel processors and specific Arm models, recently came to light. Linux publication Phoronix conducted testing that shows the new BHI mitigations could produce severe performance penalties up to 35%.
Intel will release a software update for its processors to mitigate BHI, but it may take a while since processors starting from Haswell going forward are vulnerable to the exploit. However, the Linux community was quick to act, and mitigations for BHI already formed a part of the Linux kernel in a matter of minutes after BHI's announcement.
VUSec, the Systems and Network Security Group at Vrije Universiteit Amsterdam who discovered BHI, recommended enabling Repotlines (return and trampoline) to mitigate BHI. The recommendation still stands for modern processors that already carry the necessary hardware mitigations for Spectre V2. In Intel's case, that would be eIBRS, but as the VUSec researchers highlighted, it isn't enough to fight off BHI, which is the reason to have eIBRS and Retpolines working in tandem.
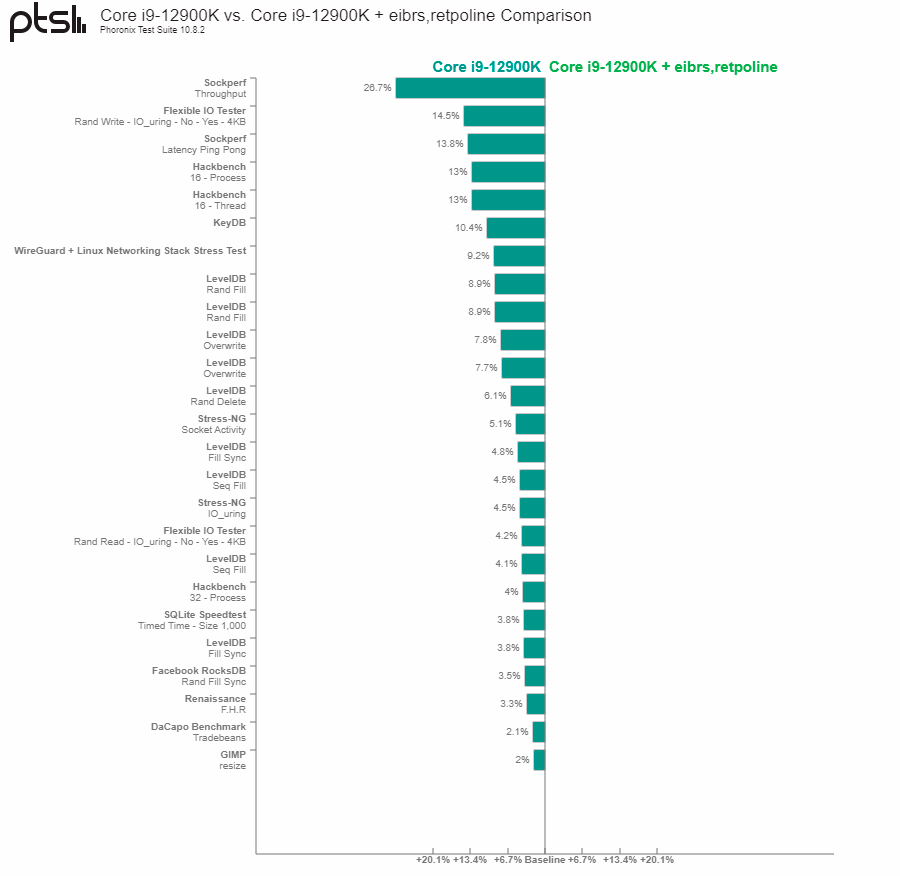
According to Phoronix's Core i9-12900K (Alder Lake) results, networking and storage performance went down the toilet after enabling Retpolines. The publication recorded a 26.7% performance loss on the former and 14.5% on the latter. That's the hallmark of these mitigations: Any external I/O from the chip takes a hard hit. Workloads like web browsing or image manipulation in GIMP didn't show a huge impact.
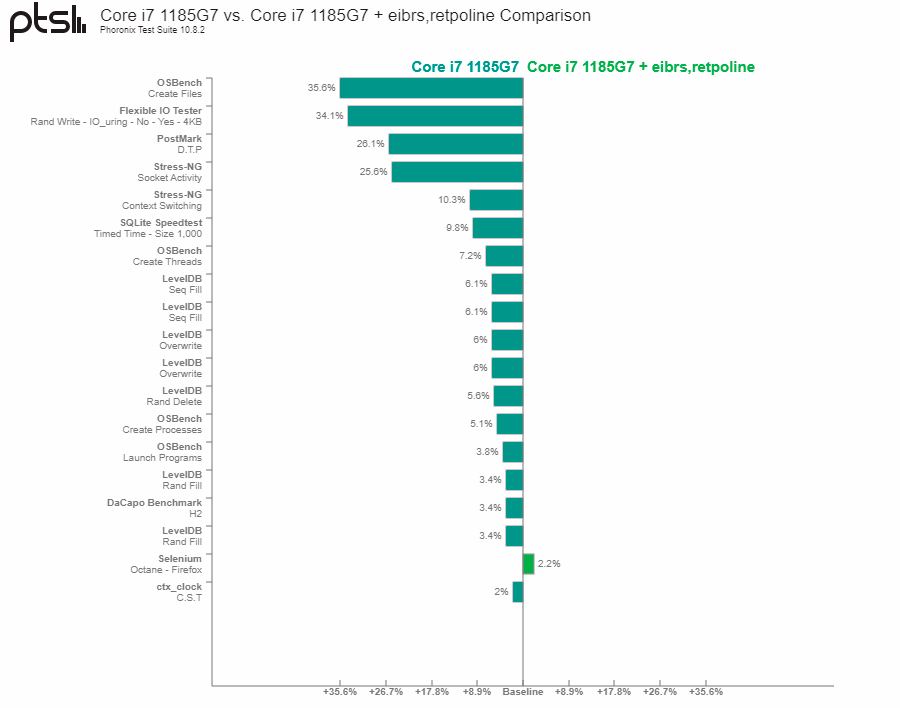
The Core i7-1185G7 (Tiger Lake) took an even more detrimental hit to storage performance. The results showed 35.6% and 34.1% lower performance in OSBench and Flexible IO Tester, respectively. But again, workloads that don't rely on I/O or networking didn't show significant performance loss. These include gaming, web browsing, and other daily tasks.
Phoronix noted that AMD processors aren't safe from BHI even though modern Zen chips already leverage Retpolines. The problem is that AMD's LFENCE/JMP-based implementation of Retpolines isn't good enough to fend off BHI, so the chipmaker is shifting to general Retpolines. The impact of the transition for AMD processors is unknown, but Phoronix is already conducting new tests to find out.
It's possible Intel and other software developers will be able to reduce the impact of the BHI mitigations with additional time and effort, but for the time being, enabling the patches could prove very painful on servers and other systems that do a lot of I/O intensive work.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Zhiye Liu is a news editor, memory reviewer, and SSD tester at Tom’s Hardware. Although he loves everything that’s hardware, he has a soft spot for CPUs, GPUs, and RAM.
-
TerryLaze Reply
Only that the 11th gen is also going to be up-to™ ~35% slower, in fact the article says down to haswell.hotaru251 said:ROFL
up to 35%?
at that much lost wouldnt that put it back to 11th gen performance?
Also:
"Phoronix noted that AMD processors aren't safe from BHI even though modern Zen chips already leverage Retpolines. The problem is that AMD's LFENCE/JMP-based implementation of Retpolines isn't good enough to fend off BHI, so the chipmaker is shifting to general Retpolines. The impact of the transition for AMD processors is unknown, but Phoronix is already conducting new tests to find out. " -
digitalgriffin Does this mean we can ask for 35% of our money back since we bought it for a certain performance tier?Reply
Installing intentional security flaws could be a great excuse to downgrade your processor over time. "So sorry we have to downgrade your processor to last gen's speeds to avoid this security issue. But if you want the latest and greatest plus fastest, you can fork over $700 for a next gen processor with a 2% speed improvement over the pre-fix processor you have."
Sooner or later there will be another class action lawsuit for designing defective products. -
digitalgriffin ReplyTerryLaze said:Only that the 11th gen is also going to be up-to™ ~35% slower, in fact the article says down to haswell.
Also:
"Phoronix noted that AMD processors aren't safe from BHI even though modern Zen chips already leverage Retpolines. The problem is that AMD's LFENCE/JMP-based implementation of Retpolines isn't good enough to fend off BHI, so the chipmaker is shifting to general Retpolines. The impact of the transition for AMD processors is unknown, but Phoronix is already conducting new tests to find out. "
Yet the exploit has been only demo'd on Intel. Wonderful spin as always Terry. -
TerryLaze Reply
What spin?digitalgriffin said:Yet the exploit has been only demo'd on Intel. Wonderful spin as always Terry.
The article says that they are still in the process of benchmarking AMD cpus. -
bigdragon I care about this vulnerability at work and don't mind the performance hit. Proprietary business data needs to stay safe. NDAs need to be respected and enforced. The workplace is a hacking target.Reply
I don't care about this vulnerability at home. I don't want the performance hit. The risk is so low. The data attackers can get is not of significant value. I don't want my computer hardware sliding back a generation or more in terms of performance.
Intel has so many CPUs out there. Maybe it's time for them to start having "S" variants too where Spectre is not mitigated and full performance is provided. -
Specter0420 Replybigdragon said:I care about this vulnerability at work and don't mind the performance hit. Proprietary business data needs to stay safe. NDAs need to be respected and enforced. The workplace is a hacking target.
I don't care about this vulnerability at home. I don't want the performance hit. The risk is so low. The data attackers can get is not of significant value. I don't want my computer hardware sliding back a generation or more in terms of performance.
Intel has so many CPUs out there. Maybe it's time for them to start having "S" variants too where Spectre is not mitigated and full performance is provided.
I agree. I fly VR flight sims, one of the few cases where the best possible single-core performance available today isn't even close to enough. I have more than five working laptops and a modern smartphone for banking, investment accounts, and private messages... Give me the option for 90, 120, or 144Hz VR at the cost of security, that's acceptable to me. 60 FPS just isn't good enough. -
hannibal Do I remember wrong that these needs to get physical access to the computer, so yeah... More work related. But if these work via internet... Then it is problem also at home usage!Reply -
boju Don't want nor concerned. Hopefully this patch is not forced from Ms, that's the only way it'll be compulsory. If it is then I'd like to know which kb update is it so i can block.Reply -
STbob Nice article, keep up the work on this. I have some older Dell servers and the spectre and meltdown on hyperV is so slow I have to turn the patches off and risk the low percentage chance of something getting in the server core OS. (low) the slowdown is real and annoying.Reply
I'm looking at newer servers but they cost $$$ and are actually slower with patches on vs my older gen servers without patches. This is not right, paying for 2023 servers that perform like 2010 unpatched. Big step backwards.