Intel Alder Lake, ARM CPUs Affected by New Spectre Vulnerability
Branch History Injection
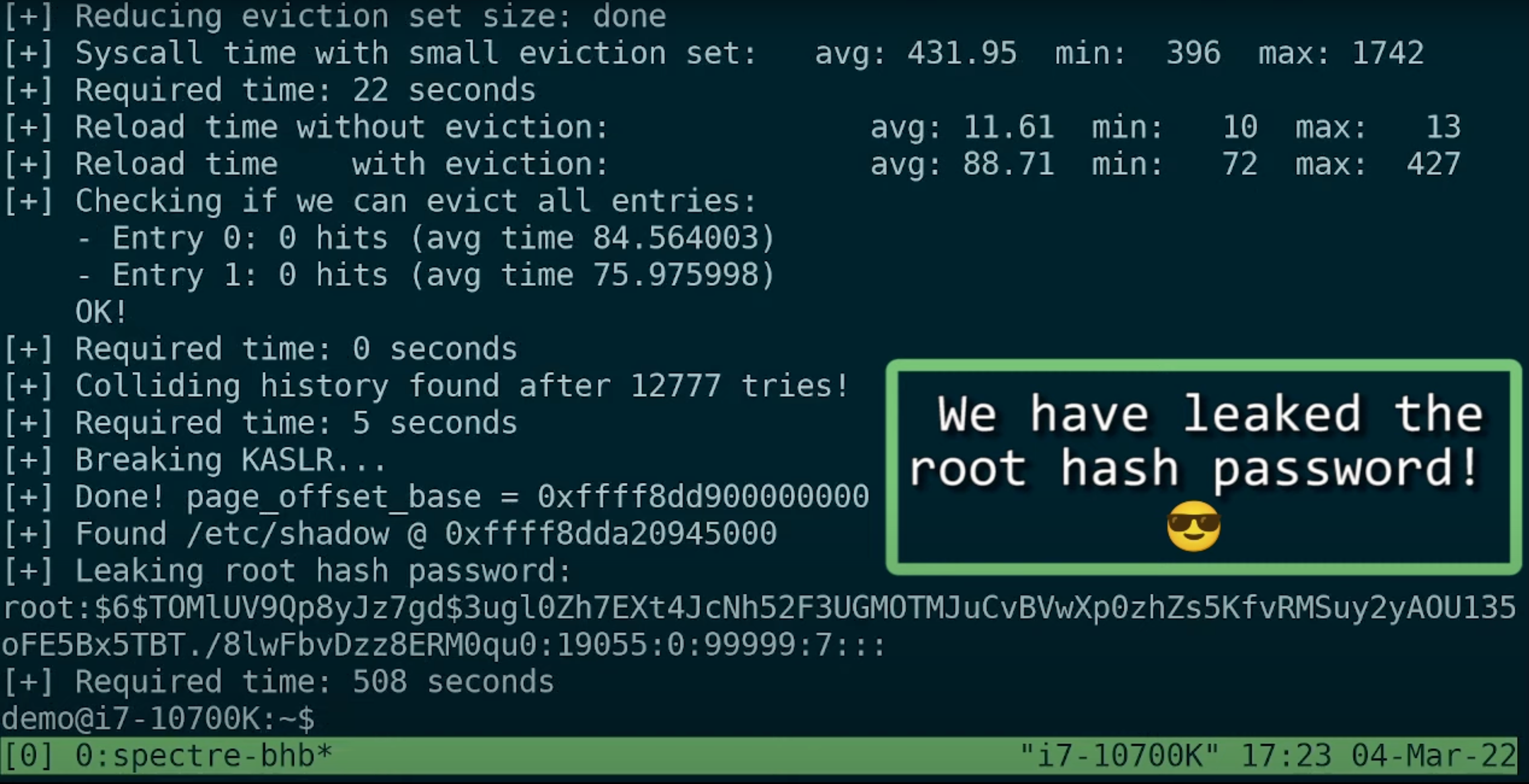
VUSec security research group and Intel on Tuesday disclosed a yet another Spectre-class speculative execution vulnerability called branch history injection (BHI). The new exploit affects all of Intel processors released in the recent years, including the latest Alder Lake CPUs, and select Arm cores. By contrast, AMD's chips are believed to be unaffected.
BHI is a proof-of-concept attack that affects CPUs already vulnerable to Spectre V2 exploits, but with all kinds of mitigations already in place. The new exploit bypasses Intel's eIBRS and Arm's CSV2 mitigations, reports Phoronix. BHI re-enables cross-privilege Spectre-v2 exploits, allows kernel-to-kernel (so-called intra-mode BTI) exploits, and allows perpetrators to inject predictor entries into the global branch prediction history to make kernel leak data, reports VUSec. As a result, arbitrary kernel memory on select CPUs can be leaked and potentially reveal confidential information, including passwords. An example of how such a leak can happen was published here.
All of Intel's processors beginning with Haswell (launched in 2013) and extending to the latest Ice Lake-SP and Alder Lake are affected by the vulnerability, but Intel is about to release a software patch that will mitigate the issue.
Numerous cores from Arm, including Cortex A15, A57, A72 as well as Neoverse V1, N1, and N2 are also affected. Arm is expected to release software mitigations for its cores. What is unclear is whether custom versions of these cores (e.g., select cores from Qualcomm) are also affected and when the potential security holes will be covered.
Since this is a proof-of-concept vulnerability and it is being mitigated by Intel and Arm, it should not be able to be used to attack a client or server machine — as long as all the latest patches are installed. There's no indication how much the mitigations will impact performance.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Anton Shilov is a contributing writer at Tom’s Hardware. Over the past couple of decades, he has covered everything from CPUs and GPUs to supercomputers and from modern process technologies and latest fab tools to high-tech industry trends.
-
hotaru251 I mean.....you think after the last time this was big they'd of been a lot more careful ;o...Reply
so we taking bets on how much performance you lose from their 1st patch? i'm gonna say 10%. -
watzupken Reply
I was thinking the same thing. Here we go again! Almost feels like this is an annual problem.-Fran- said:Here we go again? LOL
Regards. -
Well with all the back doors that they build in they are intentionally making their processors hackable. This is not surprising and this is why we have no privacyReply
They just love to spy on you and they want to retain complete control over your CPU. It’s not your CPU you see, it’s theirs and they can control it and watch whatever you do And allow the governments to watch what you do as well