Intel Says it Doubled Down on Fixing Security Bugs in 2019
Intel says it's upped its security game, but we've yet to see major design changes against speculative execution attacks.
Intel published a security report today that claims it doubled down on investments in the security of its products in 2019, following all the revelations of side-channel speculative execution attacks that its chips have suffered over the past two years.
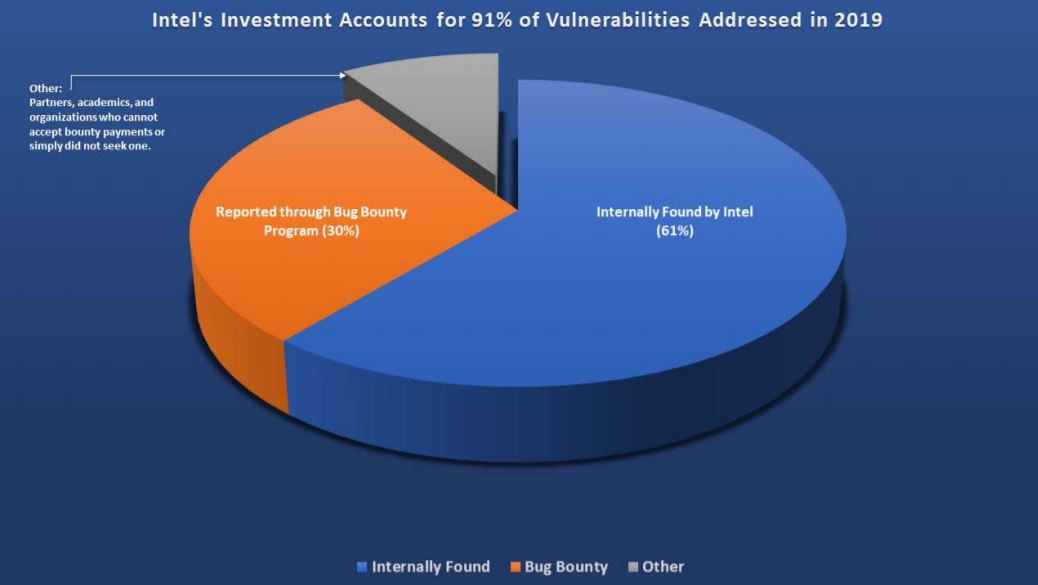
Following the Spectre flaws scandal, Intel promised it would put security first. Its new report shows that in 2019, the company’s own security team found 144 of the 236 (61%) of the Common Vulnerability and Exposures (CVEs) for its own products, with the rest uncovered by external researchers.
- We break down the best gaming CPUs available now
- Our ranking of the best CPUs for productivity
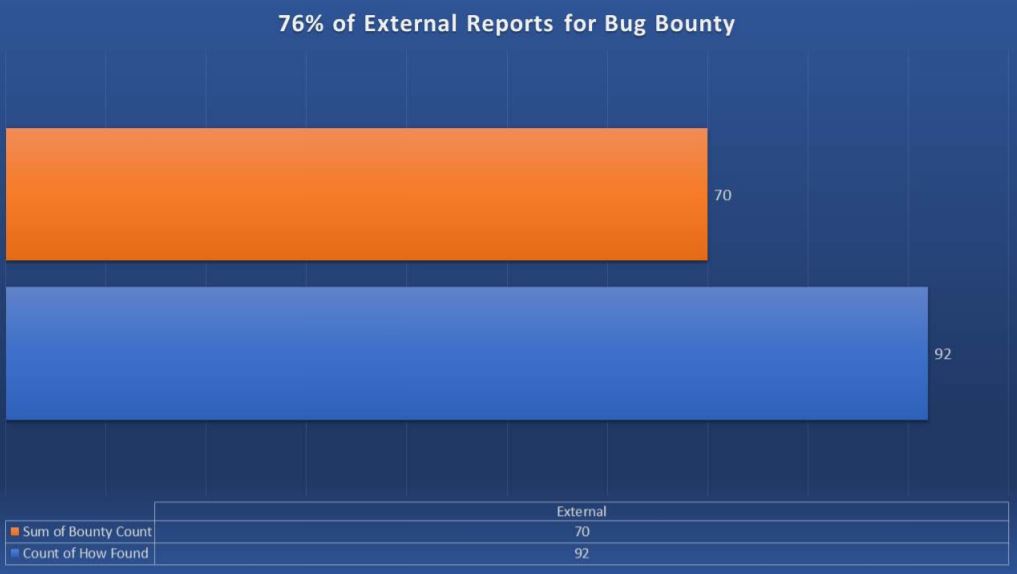
Of the 92 uncovered by external researchers, 70 (76%) came through Intel’s bug bounty program, showing that both of Intel’s bug discovery strategies are working quite well.
Intel said that 91% of the reported bugs in 2019 were due to its investment in product assurance. It also noted that none of the 236 vulnerabilities uncovered in 2019 were known to be used in attacks at the time of public disclosure.
According to the report, a little more than half of the public disclosures were part of Intel’s Platform Update (IPU) process through which security and functional updates are bundled by platform. The bundles can include microcode and firmware updates that are provided to Intel’s partners, such as motherboard and laptop makers.
However, many of these vendors don’t often update several-years-old devices. This leaves a large portion of their customers still vulnerable to certain bugs, even if Intel itself released the patches for them. Some software patches can be delivered to Windows users via a monthly security update.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
digitalgriffin Now the question is:Why can't intel release a tool which generically disables AMT and performs CPU microcode updates?Reply
Why does it have to be the motherboard vendors responsibility to update the CPU microcode?
Is it that hard for Intel to create a boot loader which updates CPU microcode? Or invalidates the UEFI area for AMT? -
bit_user ReplyIntel said that 91% of the reported bugs in 2019 were due to its investment in product assurance.
It's quite some PR spin for Intel to take credit for all of the bugs reported through their Bug Bounty program. I expect a majority of those were from researchers who would've disclosed the bugs, anyhow, but are quite willing to take any payment on offer.
Much respect to those who declined payment (although some might've been government agencies or big customers, who wouldn't be allowed to take what are effectively vendor kickbacks).
It also noted that none of the 236 vulnerabilities uncovered in 2019 were known to be used in attacks at the time of public disclosure.
Probably because these exploits are more difficult to find & utilize, leaving them as targets for governments & their contractors, who are more secretive and selective about their targets. -
bit_user Reply
My guess is that Intel wants to allow platform vendors to qualify the microcode updates against their solution. The last thing Intel wants is to break some set of end users and be in the legal hot seat with the platform vendor. And, the way Intel's supplier agreements are probably worded, it's the latter who's ultimately liable to their customers for Intel's vulnerabilities. So, they're the ones who will have to get the patches into customers' hands.digitalgriffin said:Why can't intel release a tool which ... performs CPU microcode updates?
Why does it have to be the motherboard vendors responsibility to update the CPU microcode?
In practical terms, Intel could do what you said, and it would be fine in the vast majority of cases. However, it doesn't take a lot of corner cases to create a very expensive legal headache.