Autorooting Malware 'LevelDropper' Silently Installs Apps On Android Devices
Lookout security researchers found a piece of malware on the Google Play Store that can autoroot devices and then install malicious applications on them.
The new malware, called "LevelDropper," is part of a class of “autorooting” malware that can silently install on a user’s device and perform actions that are possible only with higher privileges, essentially bypassing many of Android’s security protections.
Google is able to stop the vast majority of malware from doing harm to Android users thanks to anti-malware scanning solutions such as the server-side "Bouncer" and the client-side "Verify Apps" solution, as well as sandboxing solutions that isolate various components of the Android system.
However, sophisticated attackers can find ways around these solutions, and then it could take some time before Google discovers the new malicious applications. In the meantime, those applications will be able to steal information from the Android users that happen to have installed those apps from the Play Store or elsewhere. It’s up to Google itself or some other third-party, such as Lookout in this case, to find the new malware as early as possible before it impacts too many users.
How LevelDropper Works
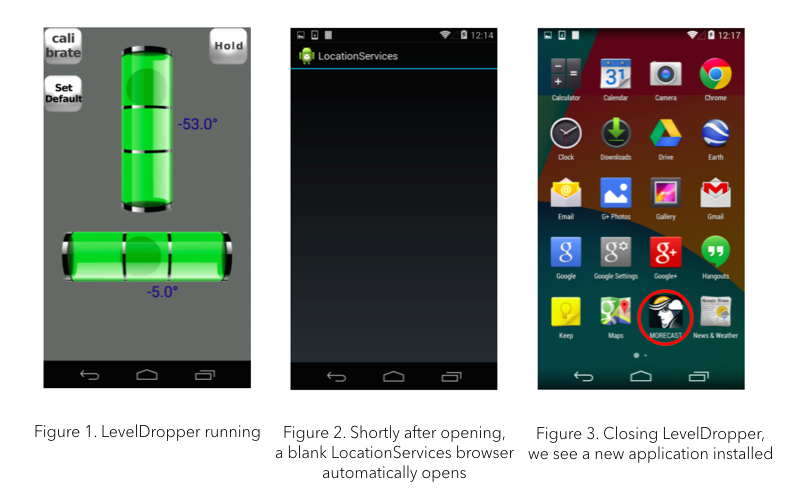
Lookout researchers noticed that after installing the LevelDropper malware, the LocationServices window appeared to be blank. That's usually a sign that it crashed, which could be used to gain an escalation in privilege.
Soon after that, the researchers saw that new applications started to appear on the test smartphone. The apps installed silently in the background without any installation prompt. Lookout said that this is an indication that the apps had root access, which is the only way apps can install without user interaction.
Lookout’s security researchers found that in a time period of 30 minutes, a set of 14 applications were downloaded and installed on the device, none of which required user interaction.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The researchers also discovered no typical signs of a device being rooted, such as a superuser binary or a rewritten “install-system-directory” script, used to ensure that the root capability survives upgrades. The only evidence they found is a writable system partition, which is normally mounted in read-only mode to avoid modifications by malicious applications.
Inside that LevelDropper package, there were two privilege escalation exploits, as well as SuperSU, busybox and supolicy tools, which are typically used for rooting a device. The package also contained additional Android APK files that would use root privileges to display obtrusive ads that couldn’t be easily blocked.
The Rise Of Autorooting Malware
As with the rise of ransomware on PCs (as well as on Android), the main goal of this new family of autorooting Android malware seems to be to generate revenue for the malware authors. Usually this type of malware is used to push ads on the user’s device, or to install applications, which are likely paid by the apps’ developers through affiliate programs based on the number of installs. Some autorooting malware is also used to write fake positive reviews of other malicious applications on the Play Store.
The only way to remove the LevelDropper malware from your device is to do a factory reset. Lookout discovered the malware last week and worked with Google to ban LevelDropper from the Play Store, so it shouldn’t be possible for other devices to be infected with it. However, the threat of other autorooting malware will likely persist, at least until Android gains new protections that make it even harder to root devices.
That would also have the downside of making it less likely for users to install custom ROMs on their devices, unless Google and Android OEMs specifically build mechanisms into their Android devices to allow users to replace the stock operating system in a secure way.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
velocityg4 Luckily your smartphone maker may have a patched version of Android out in a year or so. Assuming the phone isn't already a year old or a cheaper model in which case you are SOL.Reply -
Darkk I didn't bother to root my Note 4 for these reasons. While it was cool to load custom ROMS on my Note 2 but just not worth it to me anymore.Reply
They should let the users decide if they want access to root to be blocked permanently to keep their phone secure. This question should be asked during the initial setup of the phone. Once it's set it can't be changed until you do a factory reset. -
sh4dow83 Maybe all of this isn't a bad thing. All that insecurity around the internet has me spending less and less time on my computer and more outside of my apartment...Reply