More Car Hacks From DefCon 23
After Charlie Miller's and Chris Valasek's talk on how they hacked Charlie's Jeep, it seems every speaker paid homage to them, even on topics as disparate as a talk hacking chemical plants for blackmail, or Cory Doctorow's brilliant, impassioned screed against DMCA provision 1201.
Samy Kamkar, in his talk on mostly wireless attacks against cars and garages, also praised Charlie and Chris. In his introduction, Samy alluded to his prior mischievous self as author of the Samy MySpace worm, joking that he would never release another worm under his name. He told us that he would be speaking tomorrow at the kids-only forum, r00tz Asylum, on Combo Breaker, which could crack any combination lock within 30 seconds. In a summary slide, Samy reminded us that he has done other creative hacks: Ding Dong Ditch (hijacking a friend's blue tooth door bell) and controlling one drone from another drone.
Samy described a current technique used to hijack modern cars that starts with a keyfob: the thief uses an amplifier surreptitiously carried near someone's keyfob who is no longer within the requisite short range (5-10') necessary to start the car without a key. An improvement has an accomplice with a receiving amplifier that communicates directly with the first amplifier. Now the range could be much longer, as much as several hundreds of meters away.
Garage D'Or
The next series of attacks he described were about wireless attacks on garage door openers; he extended those attacks via similar mechanisms to unlocking key fobs. He released an opening garages toolkit, based on the old Mattel child's toy, IM-me, which will open any fixed code garage door in seconds. Note that most garage door openers available now use a rolling code, or hopping code, which is impervious to this attack. Very old garage doors are likely vulnerable to this attack, though.
Samy described his thought process and experimentation process in approaching this hack. Though this attack has been performed by others, Samy's attack is quicker and arguably more elegant. By looking at the garage remote, one may discern information about frequency of the device and type: he took the FCC ID and Googled it, coming up with a description of the device.
Next, he used Ossmann's Hack RFOne, a ("dope as s***") $340 or so Software Defined Radio (SDR) with a frequency range from 1 to 6 GHz, to capture the signal he was seeking to understand. He then described using software to break the encoding scheme (it wasn't encrypted), and then trying multiple overlapping codes at the same time to mimic the authentic signal.
The last part was simple: He used common techniques with Travis Goodspeed's GoodFet to program this onto an IM-me, which included a favorite chip, the TI CC1110, and is pink, Samy guffawed, his favorite color. As a partial consequence, IM-me has become popular, so that it is no longer as cheap as previously on eBay ($20-$30).
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Gone In 60 Seconds
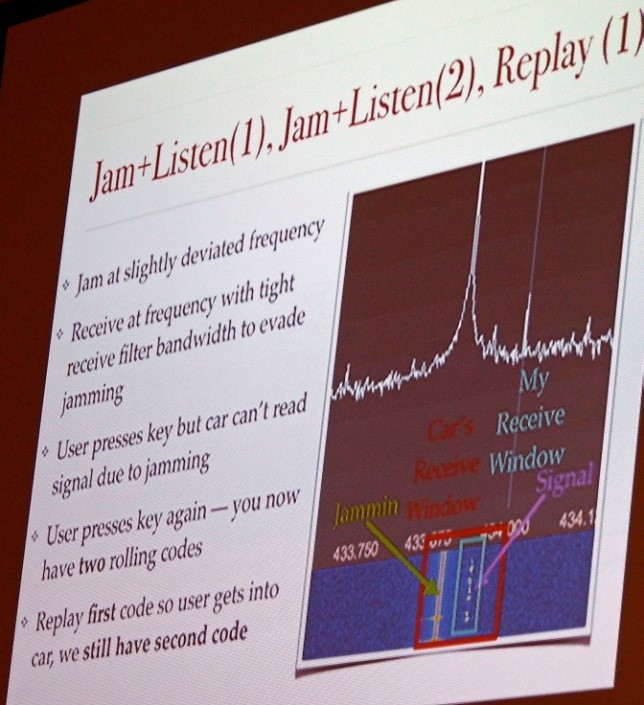
The next attack is more insidious, and is effective against rolling codes used by car key fobs as well as garage door openers. Rolling codes prevent a replay attack, where the signal is recorded for playback by the attacker. Samy jammed that signal, but he was able to listen with a far better radio that had a narrow, more finely-tuned notch filter, to avoid his own jam. So the attacker jams, listens and replays. But the code would be invalidated as soon as the receiver sees a future code. Thus, Samy's device, based on two TI CC1110s, went one step further: It jams the signal twice, replays the first code, and stores the second code for later use or replay.
This pattern may repeat for every attempt. In testing, most cars, some garages, and alarms were vulnerable, because they used the Keeloq or similar system. The way the device, called the RollJam, works is that it is secreted under the car; the unsuspecting victim goes to the car, unaware of the reason why he needs two key presses to enter the car. At some later time, the attacker retries the device and drives away with his car contents. There is no forced entry sign.
Samy's purpose in releasing this attack (though not yet described on his website) is to prove to the manufacturers that they have to consider security. This type of vulnerability has been described in the past and is in current use in the underground. RollJam may be defeated by using quickly expiring codes. Some of the latest key chips incorporate such a feature.
OnStar
The attack Samy described that was featured in the popular press is perhaps the least interesting of the three, from a hacking perspective. When looking at OnStar, he realized that there was a potential that personal information was being relayed, and could be exposed, especially so because by design, some of that information was available on his phone for his account through the OnStar GUI.
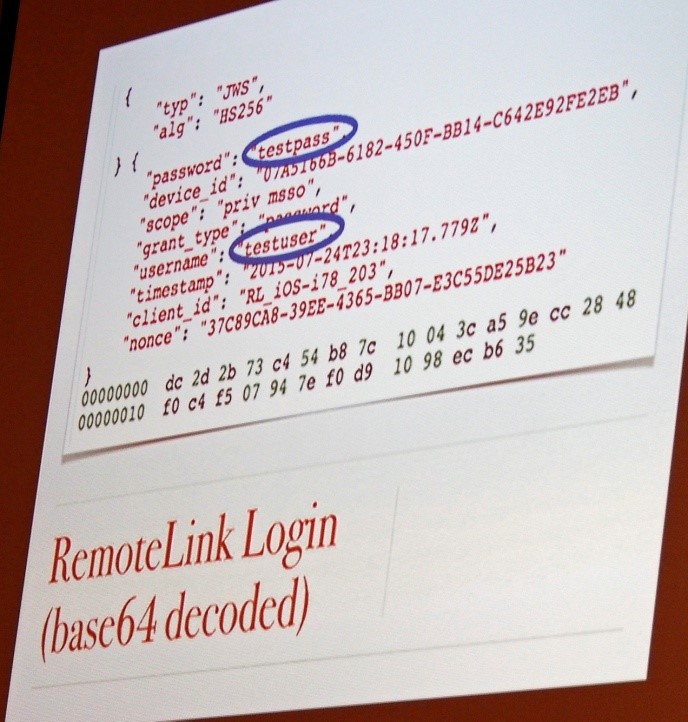
One problem was that the RemoteLink Login was only base 64 encoded, and another issue was that there was no check to see if the certificate on his phone was valid. With a Man in the Middle attack, he would be able to see all the traffic. A Man in the Middle attack is a method of impersonating a legitimate end station, so the sender has no idea that the recipient is in fact the attacker.
Samy would place a device under someone's car, which includes a radio wireless card and a Raspberry Pi, and would see the network they connected to in the past and record that information, and then he would have access to their information.
To GM's credit, it fixed this vulnerability almost immediately when apprised of the problem -- within 1-2 days, which is nothing less than phenomenal. However, in an amusing anecdote, Samy described the process of trying to escalate his call to GM to someone who knew about security. That apparently took two weeks or so.
This type of vulnerability may be eliminated in the future if manufacturers did the following, according to Samy:
- Validated certificates from the CA (Certificate Authority), or used certificate pinning - Hashed the password with a random salt on authentication request (challenge-response) - Engineers should always assume that consumer devices such as these are always on a hostile network
Follow us @tomshardware, on Facebook and on Google+.
-
Darkk Interesting stuff. Just to show that manufactures always took the easy route until somebody figures how to defeat it. Then they are forced to change it.Reply
It's an old routine of "squeaky wheel". Nothing is done until somebody complains about it.