NSA Vulnerabilities Trove Reveals 'Mini-Heartbleed' For Cisco PIX Firewalls
The Shadow Brokers group, which seems to have hacked one of NSA’s own hacking teams called the “Equation Group,” published a set of exploits that the NSA was using to hack technology companies. One of the vulnerabilities looks to be a “mini-Heartbleed,” which allows attackers to extract RSA private keys from Cisco PIX security appliances.
Two years ago, security researchers uncovered the so called “Heartbleed” bug in the OpenSSL software library for the TLS encryption protocol that’s used by most companies to secure their communications. The vulnerability could allow attackers to steal private keys and other sensitive information from a server’s memory, without its owner even realizing.
NSA’s exploit that the Shadow Brokers published, called BENIGNCERTAIN, also allows the attackers to send an an Internet Key Exchange (IKE) packet to the victim machine, causing it to dump some of its memory. Then, the memory dump can be analyzed, and RSA keys and other sensitive server configuration information can be extracted from it.
The exploit references Cisco devices running the PIX OS versions 5.2(9) to 6.3(4), which was released in 2004. The PIX devices are at the end of their lifecycles, so it’s likely that the exploit may also be at the end of a long and possibly quite fruitful life (for the NSA). However, considering not all companies refresh their hardware when the software is no longer supported, it’s possible that many of them may still be using these vulnerable and still exploitable security appliances.
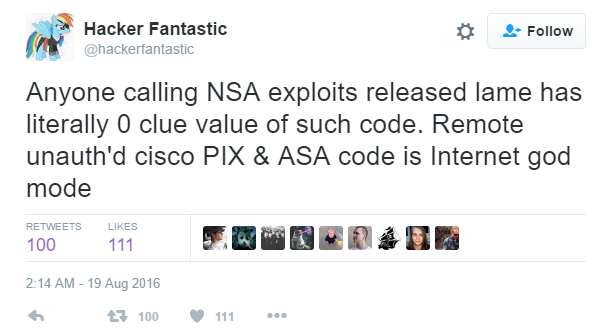
One security researcher even called the exploit the equivalent of an "Internet God Mode," so it likely still has quite some value left, if many companies keep using these security appliances.
Cisco, just like Juniper and other networking equipment makers, are likely high priority targets for the NSA and other hacking groups, state-sponsored or otherwise. They make the networking devices used by large and small organizations, which then provide services to billions of people.
Therefore, one major vulnerability could provide these groups access to all of those people’s communications. That’s why it’s critical that the networking equipment makers are that much more vigilant about the security of their products; they're responsible for everyone else’s security, too.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Kimonajane Bwaaaa hahahaha the fascist hacks at the NSA were to busy bullying MS and other companies to put back doors in for them and too busy hacking grandma Miller instead of worrying about real security for all.Reply -
Hydrotricithline This country isn't worried about public security, hasn't been since pre-snowden. It's worried that it might not beable to easly spy on 'everything' in the country/world whenever they want to. The fact they can keep exploits like this 'to themselves' is ludacris. Hell the fact that they got hacked proves they can't be trusted to keep them private. GJ NSA, want to see the conference on this one and who they're blaming instead of taking responsibility for their actions.. it's like dealing with a 12 year old.. let the finger pointing ensue..Reply -
f-14 KIMONAJANE Aug 20, 2016, 8:35 AMReply
"Bwaaaa hahahaha the fascist hacks at the NSA were to busy bullying MS and other companies to put back doors in for them and too busy hacking grandma HILLARY instead of worrying about real security for all."
there fixed it for you, good job NSA no way hillary can delete your 33,000 copies of her private server emails evidence that she destroyed. -
sykozis Reply18471083 said:KIMONAJANE Aug 20, 2016, 8:35 AM
"Bwaaaa hahahaha the fascist hacks at the NSA were to busy bullying MS and other companies to put back doors in for them and too busy hacking grandma HILLARY instead of worrying about real security for all."
there fixed it for you, good job NSA no way hillary can delete your 33,000 copies of her private server emails evidence that she destroyed.
People keep going on and on about Hillary's private e-mail server....but what about the private e-mail servers used by Senators and Representatives to send "classified" documents to and from Hillary's private server? Maybe people should pay attention to ALL of the news and not just the part that fits their own political agenda.... The FBI stated that they were not filing charges against Hillary Clinton because they could not do a full, proper investigation because they were specifically ordered to ignore evidence of wrongdoing by anyone other than Hillary Clinton. They also informed the Senate that Senators and Representatives were also using private e-mail servers to send and receive "classified" documents. Evidence that the FBI was ILLEGALLY ordered to ignore.