WhatsApp's 8-Month-Old Flaw Allows Interception Of Encrypted Messages
WhatsApp conversations are supposed to be impenetrable. But a vulnerability discovered by security researcher Tobias Boelter could allow the company, or anyone compelling it, to intercept communications that were supposed to be encrypted from end to end. Facebook--which owns WhatsApp--said this is expected behavior and doesn't seem to be planning a change to its setup any time soon.
WhatsApp’s Signal-based E2E Encryption
In April 2016, WhatsApp announced support for “full” end-to-end encryption for messages and voice calls on all platforms. Much like the Incognito Mode on Google’s Allo and the Secret Conversations in Facebook Messenger that followed it, WhatsApp's encryption relied on the Signal protocol, which was developed by cryptography experts and privacy activists at the Open Whisper Systems non-profit organization.
WhatsApp seems to have added a little extra something in to the mix. Instead of telling users a message couldn't be delivered, like OWS' Signal app, the service will instead makes sure a message arrives on a recipient's device using a new encryption key generated by WhatsApp. End-to-end encryption is only supposed to use private keys stored on client devices; this setup undermines the whole purpose of building the Signal protocol into WhatsApp.
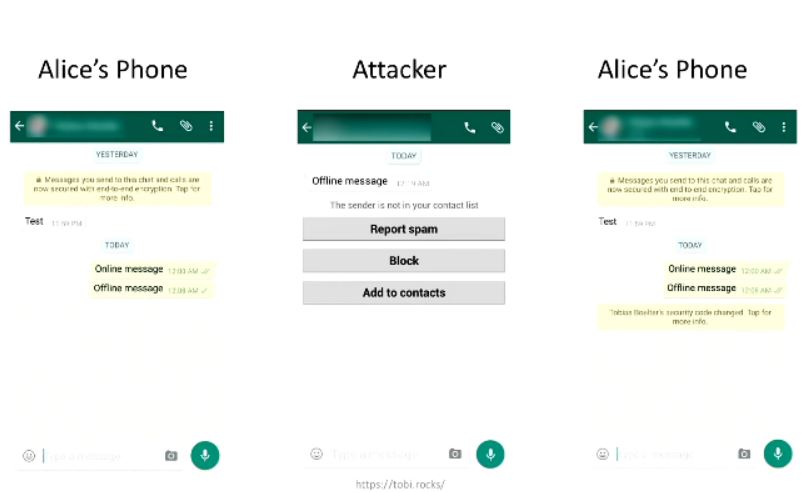
Uncovering WhatsApp’s E2E Encryption Flaw
Boelter said this vulnerability could allow entire conversations to be intercepted. The flaw has existed since WhatsApp announced support for end-to-end encryption in April, and Facebook was notified about it then. Yet the company hasn't fixed--or expressed any desire to fix--the issue since its disclosure. Here's what a Facebook spokesperson said in response to a request for comment:
Over 1 billion people use WhatsApp today because it is simple, fast, reliable, and secure. [...] At WhatsApp, we’ve always believed that people’s conversations should be secure and private. Last year, we gave all our users a better level of security by making every message, photo, video, file and call end-to-end encrypted by default. As we introduce features like end-to-end encryption, we focus on keeping the product simple and take into consideration how it's used every day around the world.In WhatsApp's implementation of the Signal Protocol, we have a “Show Security Notifications” setting (option under Settings > Account > Security) that notifies you when a contact's security code has changed. We know the most common reasons this happens are because someone has switched phones or reinstalled WhatsApp. This is because in many parts of the world, people frequently change devices and SIM cards. In these situations, we want to make sure people's messages are delivered, not lost in transit.
Facebook seems to say this so-called feature is necessary because people often change their SIM cards in other parts of the world, and they would therefore not receive messages after their cards are changed. Senders could still be warned if a message couldn't be sent, however, so they could just find their intended recipient's most recent contact information and re-send the message that way. That would be less convenient but more secure.
Keep in mind that this is only an issue between the time you change your SIM card and you turn on the phone again with the new SIM card. Once you’re in WhatsApp again, you will continue to receive the messages, even with the new SIM card and even if the security keys are not verified again. Also, dual-SIM smartphones are already popular in many of the countries WhatsApp talks about, so changing SIM cards may not be as bothersome as before.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Mitigating The Issue
Facebook’s representative said that if users are concerned about this issue they should enable the Show Security Notifications feature in their WhatsApp settings. This would tell users when WhatsApp changed the previously “trusted” key of the sender.
However, in the same way WhatsApp interfered with end-to-end encryption to generate its own keys, it could probably also hide those notifications. Therefore it’s recommended that you authenticate someone's identity with the security codes found on their WhatsApp contact pages. It’s preferable to scan a QR code when you meet someone in person, but failing that, you could also share the QR code over WhatsApp or another secure chat application.
Backdoor Or Vulnerability?
The researcher who discovered the flaw initially has a hard time figuring out whether this was an honest mistake, something that was actually intended to be a feature, or whether it was an intentional backdoor for law enforcement. As we’ve seen recently with the passage of the Investigatory Powers Act, it may now be possible for the UK government to force communications providers to backdoor encryption where it’s "technically feasible."
It’s hard to say one way or another. Even if it was meant to be a backdoor, it would probably be masked as a feature. The best backdoors are those that can be plausibly denied if discovered.
As Echoworx senior director Jacob Ginsberg said in a statement, WhatsApp has played a big role in making end-to-end encryption a mainstream feature people want in their chat applications, and it deserves some credit for that. (Open Whisper Systems still deserves the most credit for inventing a strong E2E encryption protocol that would even have a chance of being adopting by all of these apps in the first place.) Ginsberg said:
The fact that Facebook has known about this vulnerability since April is doubly damning. Not only could this be seen by many as supporting on-going government data collection interventions, it means their talk of encryption and privacy has been nothing more than lip service. The company needs to actively address its security measures. [...] These revelations add to the severe lack of clarity around encryption backdoors, most recently brought about by the IP Bill. While we know consumers are willing to trade their personal information for access to seemingly free services such as WhatsApp, now is the time to ask the question ‘at what cost to personal privacy?’ and start taking privacy more seriously.
If WhatsApp values end-to-end encryption, then it needs to stand by it, and it can’t compromise it to enable niche “features”. This issue casts doubt on how much users can trust WhatsApp and Facebook, especially after the companies went against their initial promise not to share user data. Now people may also have to wonder if WhatsApp is starting to backtrack on uncompromised end-to-end encryption, too. How WhatsApp addresses a known, eight-month-old vulnerability in its end-to-end encryption system could help answer that question.
Boelter presented the vulnerability in a short talk at the recent Chaos Computer Club (CCC) conference (minute 48:05):
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
rantoc They knew about it and didn't care because it allowed them and their best buddies in the 3 letter agencies to snoop on the messages.Reply
I believe this snoop on everything attitude will be the death of US tech companies once the general public in large enough numbers starts to see how rotten their true privacy side is. -
hotroderx I agree something like this should be released to the public so they can decided if they want to use or not use this program, but to be honest with you if they don't want to encrypt it ok!Reply
People need to start taking a realistic view of things. One the government most likely could careless. There only some many resources at any governments disposal. Just because they can or could do something doesn't mean they well. This narcissistic view by people about everything is getting as bad as the PC.
Most people most likely use a chat like this to send nudes of them selfs are talk about dirty things to each other. Both I highly doubt is a priority for the government! They might also use it to talk about there date or what they had for dinner are there ear infection! Once more no one cares other then the other person on the end of the chat... they most likely dont care either! There just saying they do as not to be rude
Most corporations and just people in general dealing with serious information are most likely going to use there own secure systems. There sure not going to rely on a app created or owned by facebook for such communications.
That said cause i know already getting voted down but what ever I really don't care. Instead of focusing on privacy for what I would call simply stupid things! I want privacy for important things like wireless encryption inside homes and business and laws on how information obtained could be used.
I want strengthen encryption and privacy where it counts! IOT devices! and hardware. Routers, tvs, computers, etc. These are devices that should be truly secure not from someone collecting data about XYZ to show you do YZX on your computer. Real security that stops a hacker from gaining access to your pc or device to install some type program to cause it to become corrupt are be used to attack another system. -
Olle P This isn't much of an vulnerability. Signal is using asymmetric encryption, and it's a new public key that is being sent to the sender of the message.Reply
Just as with any other type of encrypted traffic the sender needs to trust that the key belongs to the intended receiver of the message and not to some middle agent. This can be verified in many ways using other means of communication.
The "vulnerability" here is that the exchange of keys by default is done without notification, but since notifications can be activated a middle-man can't know whether or not the attempted intercept will be noticed before the message is being sent. -
Andrei M It's really annoying to see to see such poor reporting on Tomshardware. It's not a backdoor, it's not a vulnerability, it's by design and it's carefully engineered with the user's privacy in mind. Saying "Boelter said this vulnerability could allow entire conversations to be intercepted" without explaining how that claim is false ("entire conversations" CANNOT be intercepted) really hints at the author not understanding what he's talking about and not having the curiosity to research it at all.Reply
Here's Moxie's (the creator of the Signal protocol) explanation clarifying everything: https://whispersystems.org/blog/there-is-no-whatsapp-backdoor/
It's not the first time I notice shallow reporting by this particular author (although in this case it's not just shallow, it's utterly misleading and mostly false). Please, take a bit more care. -
dE_logics Too bad the general public didn't know about 'closed source protocol' and it's implications before adopting the app.Reply