Windows Defender Sandbox Remains Disabled If You Shut Down Your PC
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Last week, Microsoft announced that Windows Defender would become the first antivirus to be sandboxed. However, security researcher Didier Stevens learned that, due to a bug, the feature couldn’t be properly enabled if he shut the PC down instead of restarting it.
Windows Defender Sandbox Off to a Bad Start
Right now, to enable the sandbox feature for Windows Defender in the latest Windows Insiders preview build, you would have to create a system environment variable called "MP_FORCE_USE_SANDBOX" and set its value to 1. Then, to activate it, you would have to restart the PC, too. However, Didier found that if you shut down the PC instead, the feature would no longer activate.
Didier recounted how he found the bug in a handler diary on the SANS Institute website:
“I encountered an issue to activate the sandbox: after creating the system environment variable, I shutdown my machine and then powered it on. This did not enable the sandbox. I had to perform a restart (Start Menu / Power / Restart) for the sandbox to be activated. The same thing happened when I tried to deactivate the sandbox: make sure you perform a restart (literally). This issue was reported to Microsoft, and should be fixed in an upcoming release.”
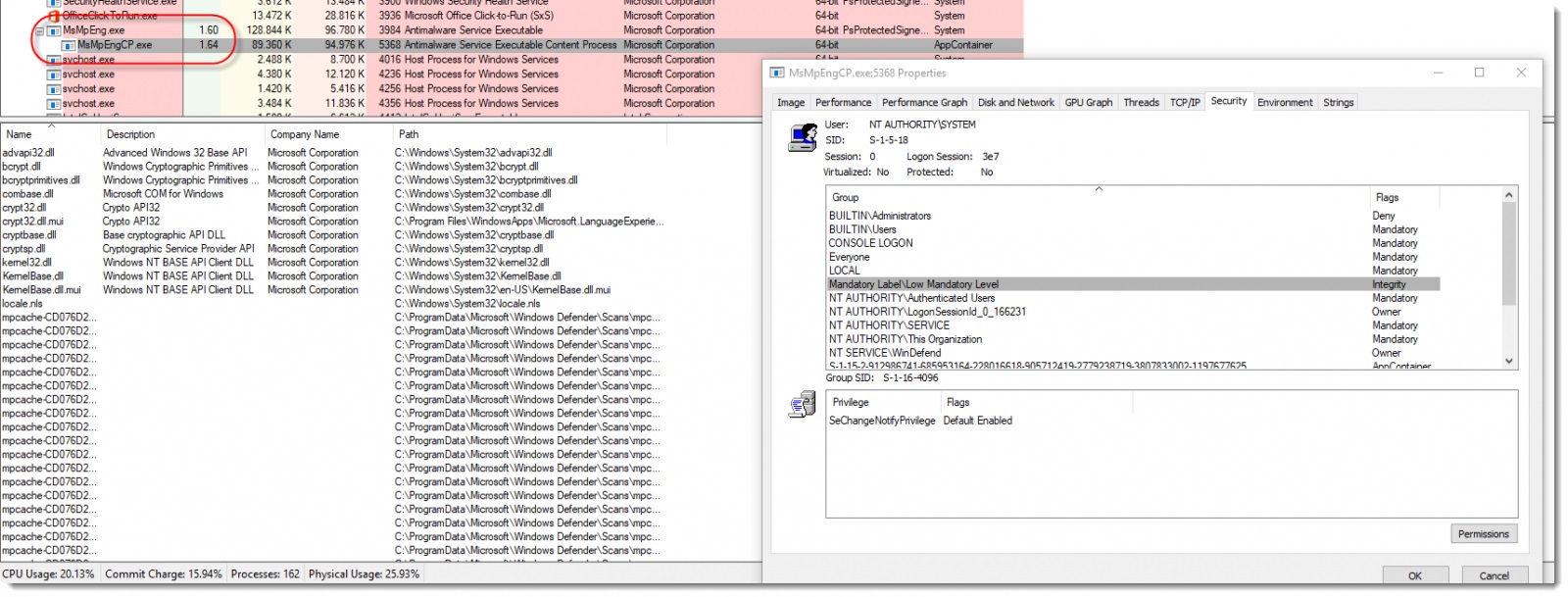
Didier also noted that to be sure that the sandbox is activated, you could use a program such as Process Explorer and check if the Windows Defender process “MsMpEng.exe” comes with a child process called “MsMpEngCP.exe.”
If that child process doesn’t show, then make sure that the MP_FORCE_USE_SANDBOX variable is created and set to 1 and then restart your PC.
Consequences of a Default Antivirus Solution
When Microsoft launched Windows 8, the company also shipped it with the Windows Defender antivirus (previously called Microsoft Security Essentials) by default. This meant users wouldn’t need third-party antiviruses anymore (in theory), which inevitably brought its own set of issues.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
One of the issues was that other antivirus companies didn’t like that Microsoft was making them obsolete, because before long, most users may learn that they don't need another antivirus to protect their PCs.
Making Windows Defender the default antivirus also meant that it became the malicious actors’ primary antivirus target. To make their malware run on Windows machines, attackers would have to first learn how to bypass the Defender protections, otherwise their malware would always be blocked as soon as it landed on users' PCs.
Microsoft would eventually learn about those new attacks and protect against them, as other antivirus companies typically do when they learn about new attacks about which their antivirus wasn't previously aware. However, it could still take many months or years before the attack and specific Defender bypass would be discovered.
New Windows Defender Sandbox Feature
Yet another issue created by Windows Defender being the default antivirus solution on hundreds of millions of PCs was that more sophisticated attackers would also be encouraged to find ways to turn Defender against its own users.
Like most security solutions, to be effective, Windows Defender also needed high privileges to access and scan all sorts of files on a Windows machine without user assistance. However, this also means that if an attacker could exploit Windows Defender, they could also take over the users’ systems. A similar flaw was already found in Windows Defender last year, which may have prompted Microsoft to develop the sandbox feature in the first place.
The sandbox feature restricts part of Windows Defender’s privileges to minimize the potential damage that an attacker taking over Windows Defender could create. Only the components of the antivirus that absolutely need the full privileges will not be sandboxed, while most of the other components will run in a sandbox.
This Windows Defender sandboxing feature will ship in stable builds of Windows 10 in the future after Microsoft has done more testing and has received more feedback from users and security researchers alike.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
alextheblue Armasu non-article... ACTIVATE!Reply
Right now, to enable the sandbox feature for Windows Defender in the latest Windows Insiders preview build, you would have to create a system environment variable called "MP_FORCE_USE_SANDBOX" and set its value to 1.
It's a new feature that is not even on by default yet, even on the bleeding edge releases. You think... you think it might have bugs? Why not go snag some alpha builds of other software and see if you can't find bugs? Oh man, think of all the "news" articles you could write! -
gasaraki Reply21459817 said:This article is just clickbait...
I agree. This is just a bug related to someone trying to force the sandbox feature on and the fast startup function. I bet if you disable the fast startup function, it would work fine.
-
eye4bear I hope that MS gives this better testing than they did with their last slow-track update and actually read the posts insiders post to the feedback log, which they seem to do only part of the time...( coming from someone who lost files with the recent update bug ).Reply