Ubuntu 24.04 Beta delayed due to malicious code in xz-utils, other Linux distros are also affected
It's only a week away!

According to a Discourse post, the beta for Ubuntu 24.04 (codename: Noble Numbat) , which was due to be released tomorrow has been delayed and now we should expect it on April 11. The reason for the delay is said to be CVE-2024-3094 — otherwise known as the XZ compression tools, which were compromised with malicious code.
This delay also leads to speculation that the upcoming 24.04 launch — slated for April 25 — could possibly be delayed.
In the Discourse post, Łukasz 'sil2100' Zemczak announced that Canonical, the company behind Ubuntu, has "made the decision to remove and rebuild all binary packages that had been built for Noble Numbat after the CVE-2024-3094 code was committed to xz-utils (February 26th), on newly provisioned build environments."
This means that any binaries built for the latest Ubuntu release will not be impacted by the recent threat introduced via xz-utils.
The threat, which also triggered Red Hat to release an urgent security alert, sees malicious code being introduced to versions 5.6.0 and 5.6.1 of xz-utils. This code appears to introduce a backdoor into systems. According to an Openwall mailing list post by Andres Freund:
"After observing a few odd symptoms around liblzma (part of the xz package) on Debian sid installations over the last weeks (logins with ssh taking a lot of CPU, valgrind errors) I figured out the answer:
The upstream xz repository and the xz tarballs have been backdoored."
The xz-utils package is used to compress files / directories using the XZ compression format, commonly used on Linux and Unix machines. At the time of writing, Ubuntu 24.04 (Noble Numbat) is using version 5.6.1 of xz-utils, which was one of the two affected versions. By rebuilding the packages with known good code build environments, Canonical claims that it "provides us with confidence that no binary in our builds could have been affected by this emerging threat."
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The impact on the beta is that we will now have to wait an extra week before we can get a hands-on with something approaching the final release (there is generally a release just before launch, which is considered a release candidate). Of course there are daily builds that we can try out, but we can't guarantee they are free of the malicious code.
Does this mean the April 25 release date will be pushed back? Ex-Canonical employee and well known Linux podcaster Alan "Popey" Pope ran a poll on Mastodon asking if Ubuntu 24.04 might be delayed. At the time of writing, 58% believe that it will be released on time, while 42% fear that it may be delayed.
The last time that an Ubuntu release was delayed was back in 2006: Ubuntu 6.06 "Dapper Drake" was delayed by two months to give the team more time to implement extra features for what was to become a pivotal Linux distro. Ubuntu 6.06 saw the merging of a live and install CD, along with a graphical installer and a means to install the OS to a USB drive.
Are other Linux distros affected?
According to a list compiled by helpnetsecurity.com, it is a bit of a mixed bag:
- Ubuntu 24.04 has been impacted, but previous releases are not.
- Red Hat, Fedora Rawhide (current Fedora Linux development build) and Fedora 40 are affected. No Red Hat Enterprise Linux (RHEL) versions are impacted.
- Debian, no stable releases are impacted, but users who use packages from the Debian testing, unstable and experimental repositories are urged to update the xz-utils package.
- Kali Linux users who updated their systems between March 26 and 29 are impacted.
- Some Arch Linux installation media, containers and virtual machines are impacted.
- Linux Mint, Gentoo Linux, Alpine Linux and Amazon Linux are not affected.
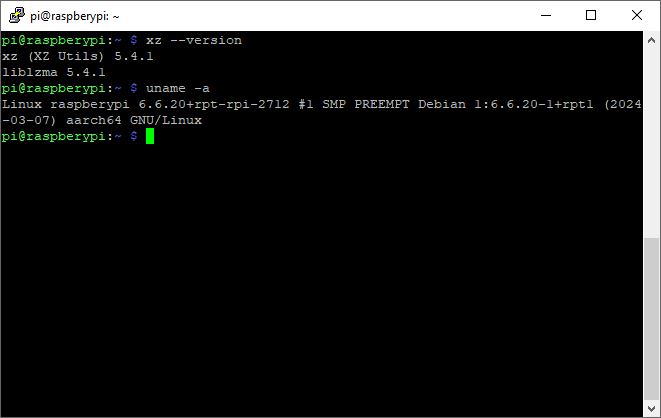
We did check our Raspberry Pi 5 running the latest Raspberry Pi OS (Kernel 6.6.20 from March 7 2024), and checking the version number for xz returned version 5.4.1. So, all appears well for our favorite single board computer.

Les Pounder is an associate editor at Tom's Hardware. He is a creative technologist and for seven years has created projects to educate and inspire minds both young and old. He has worked with the Raspberry Pi Foundation to write and deliver their teacher training program "Picademy".
-
artk2219 Reply
I wonder who injected that code into XZ-Utils, I mean there are plenty of candidates, but I wonder who figured it was worth a go this time around.Admin said:The Ubuntu 24.04 beta has been delayed for a week due to malicious code in the xz-utils package. Updates and fixes are being worked on.
Ubuntu 24.04 Beta delayed due to malicious code in xz-utils, other Linux distros are also affected : Read more -
ezst036 Replyartk2219 said:I wonder who injected that code into XZ-Utils, I mean there are plenty of candidates, but I wonder who figured it was worth a go this time around.
Some of what I have been reading (and of course its all speculative anyways) is that these were state actors, that is, someone like Russia, China, or Iran.
As Linux continues to become more popular this sort of thing is bound to become more common.
For the security-through-obscurity enthusiast, a *BSD is quickly becoming the only option left. Unless its a resource such as XZ, which the BSDs also rely on. -
Dingledooda Is this just a linux problem . . . . what about all the modems and routers that run linux which you know won't get updated (least the older ones)?Reply
Can they get into the router and then into anyone's computer connected to it now regardless of what OS it is running? -
CelicaGT Reply
https://arstechnica.com/security/2024/04/what-we-know-about-the-xz-utils-backdoor-that-almost-infected-the-world/artk2219 said:I wonder who injected that code into XZ-Utils, I mean there are plenty of candidates, but I wonder who figured it was worth a go this time around.
This is worth a read. Quite the story, came down to ONE PERSON who noticed something funny and blew the whole operation wide open. This one should put chills down the spine of anyone working in IT security. -
Notton Replyezst036 said:that is, someone like Russia, China, or Iran.
I think there is too little info to point fingers, but I do agree this is nation state level of malware.
What we do know is who would have been most affected.
Seeing as this was targeted towards Debian and Red Hat users...
States with largest Debian share: Cuba, Czech Republic, Germany, Belarus, Russia
States with largest Red Hat share: Bangladesh, Nepal, Sri Lanka, India, Cuba
https://www.pingdom.com/blog/linux-popularity-across-the-globe/ -
35below0 Reply
Don't leave out North Korea.ezst036 said:Some of what I have been reading (and of course its all speculative anyways) is that these were state actors, that is, someone like Russia, China, or Iran.
But yeah, speculation only at this point. -
TJ Hooker Reply
The malicious code was only introduced in a very new release of xz utils. Highly unlikely the affected package version made it into any router FW releases.Dingledooda said:Is this just a linux problem . . . . what about all the modems and routers that run linux which you know won't get updated (least the older ones)?
Can they get into the router and then into anyone's computer connected to it now regardless of what OS it is running? -
TJ Hooker Reply
The malicious code was introduced in the upstream xz utils source, it affects (or would have affected) any Linux distro that uses that package (so essentially all of them). Debian and Red Hat just happened to be among the first to add the new, compromised versions to their repos (just the development/beta repos though).Notton said:Seeing as this was targeted towards Debian and Red Hat users... -
artk2219 Reply
That was a pretty fascinating read, it seems like we just got really lucky that someone was paying attention with this one.CelicaGT said:https://arstechnica.com/security/2024/04/what-we-know-about-the-xz-utils-backdoor-that-almost-infected-the-world/
This is worth a read. Quite the story, came down to ONE PERSON who noticed something funny and blew the whole operation wide open. This one should put chills down the spine of anyone working in IT security. -
bit_user Reply
North Korea is becoming surprisingly adept at hacking. I wouldn't rule them out. Here's an awesome (free) podcast series from the BBC about the DPRK's hacking exploits:ezst036 said:Some of what I have been reading (and of course its all speculative anyways) is that these were state actors, that is, someone like Russia, China, or Iran.
https://www.bbc.co.uk/programmes/w13xtvg9
Given it's already far and away the dominant cloud OS, as well as being used for scientific and DoE (i.e. military) supercomputing, it's already a plenty juicy target. I'm actually surprised this sort of thing hasn't been happening a lot more!ezst036 said:As Linux continues to become more popular this sort of thing is bound to become more common.
🤔ezst036 said:For the security-through-obscurity enthusiast, a *BSD is quickly becoming the only option left. Unless its a resource such as XZ, which the BSDs also rely on.