China's Largest Bank Forced to Settle Trades by USB Stick After Ransomware Attack
Messengers physically carried USB thumbsticks around Manhattan with financial details to settle traded securities.

Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Industrial & Commercial Bank of China Ltd., which is listed as the world's largest bank, was recently affected by a crippling ransomware attack. Specifically, the cyberattack targeted its U.S. division, ICBC Financial Services (ICBC FS), based in New York.
It has been reported that the incident, which disrupted several of the company's systems responsible for settling financial transactions, impacted the trading of U.S. Treasury securities earlier this week. Instead of settling transactions electronically via secure systems, ICBC FS was forced to rely on messengers carrying USB thumb drives around Manhattan, NY loaded with the settlement details.
"Immediately upon discovering the incident, ICBC FS disconnected and isolated impacted systems," said ISBC FS in a notice on its website. "ICBC FS has been conducting a thorough investigation and is progressing its recovery efforts with the support of its professional team of information security experts. ICBC FS has also reported this incident to law enforcement."
With China becoming more tightly interwoven in the U.S. financial sector, disruptions like these are certain to draw a lot of scrutiny. In fact, ICBC is the only Chinese broker with the necessary clearance as a securities broker in the U.S.
"ICBC has been closely monitoring the matter and has done its best in emergency response and supervisory communication," added Chinese foreign ministry spokesperson Wang Wenbin in response to the ransomware attack.
For its part, the U.S. Treasury is monitoring the situation. "We are aware of the cybersecurity issue and are in regular contact with key financial sector participants, in addition to federal regulators. We continue to monitor the situation," said a spokesman who gave a statement to Bloomberg.
ICBC has not publicly indicated who may have been behind the ransomware attack, but security researchers believe that LockBit is responsible. LockBit has attacked high-profile companies across the globe, including Boeing and the Royal Mail of the U.K. LockBit 3.0 malware was allegedly used in the attack, which is difficult to detect and harden defenses against because, "each instance of the malware requires a unique password to run without which analysis is extremely difficult or impossible," according to VMWare.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
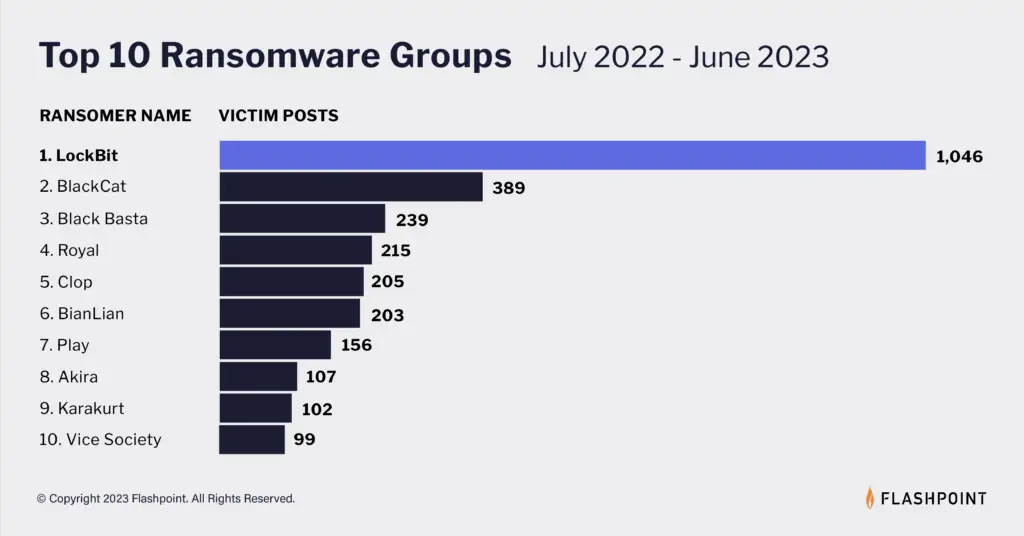
Cyber cyber intelligence firm Flashpoint reported in July that LockBit is by far the most prolific purveyor of ransomware globally.

Brandon Hill is a senior editor at Tom's Hardware. He has written about PC and Mac tech since the late 1990s with bylines at AnandTech, DailyTech, and Hot Hardware. When he is not consuming copious amounts of tech news, he can be found enjoying the NC mountains or the beach with his wife and two sons.
-
bit_user Wondering where LockBit is based, because who would dare... ? Can being located in North Korea or Russia possibly protect you, if the Chinese government really decides to come after you. I would not assume so.Reply -
The Historical Fidelity “Cyber cyber intelligence firm Flashpoint reported in July that LockBit is by far the most prolific purveyor of ransomware globally”Reply
Dang, cyber^2 is like next level stuff. Here I thought cyber threats were dangerous enough, but now we have to worry about cyber cyber threats lol. Just kidding, I thought it was a funny typo. Thanks