Researchers reveal chips that commit 'circuit suicide' — self-destruction and counterfeit protection in one
"This CPU will self-destruct in five seconds. Good luck, Jim"
As part of IEEE Spectrum's coverage of security advances made at their International Solid-State Circuits Conference (ISSCC) held last week, a team from the University of Vermont showed off a way to manufacture chips (like CPUs) that self-destruct when compromised. This doubles as both a security measure and an anti-counterfeiting measure, which is useful for vendors who wish to protect their designs.
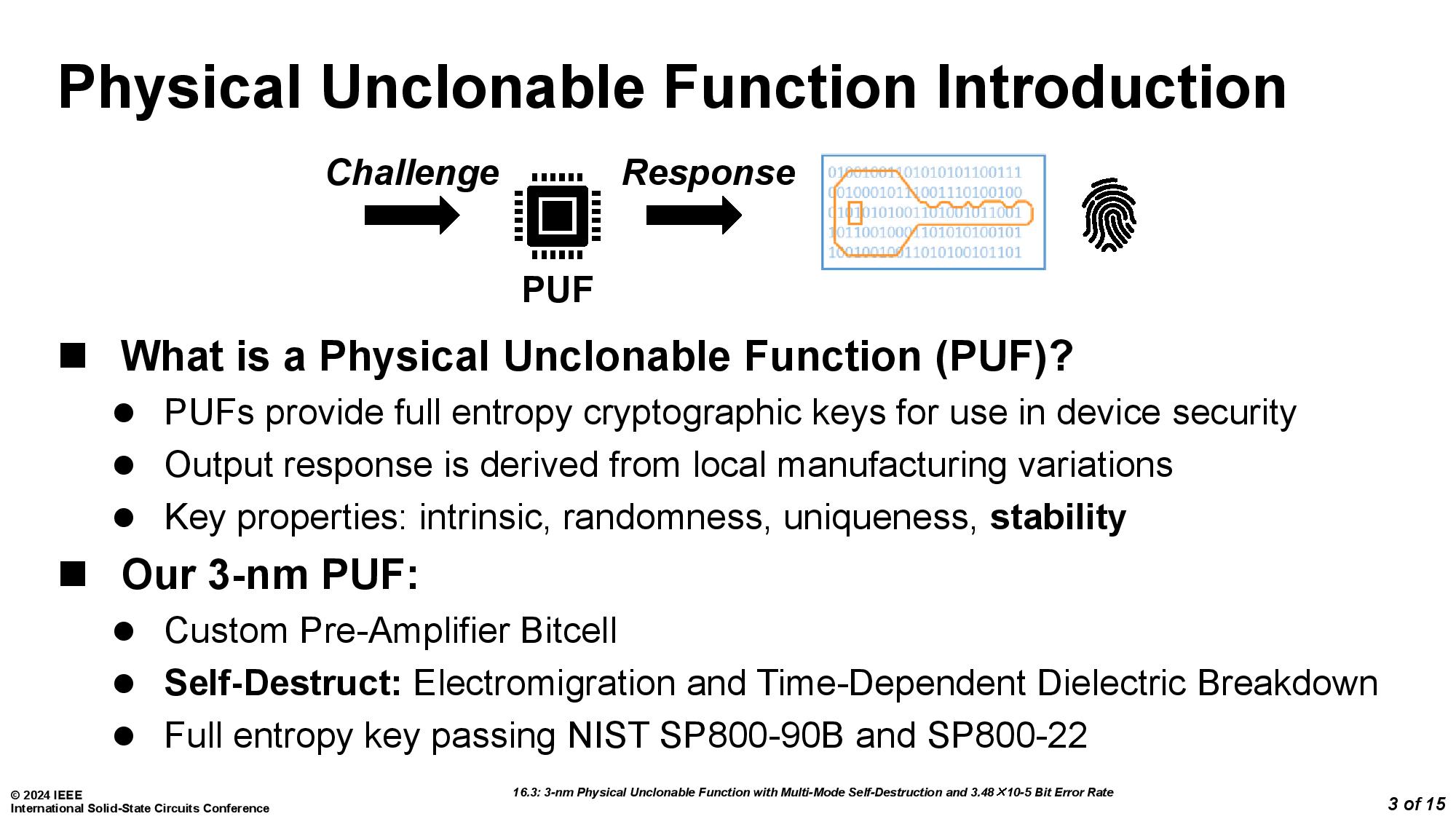
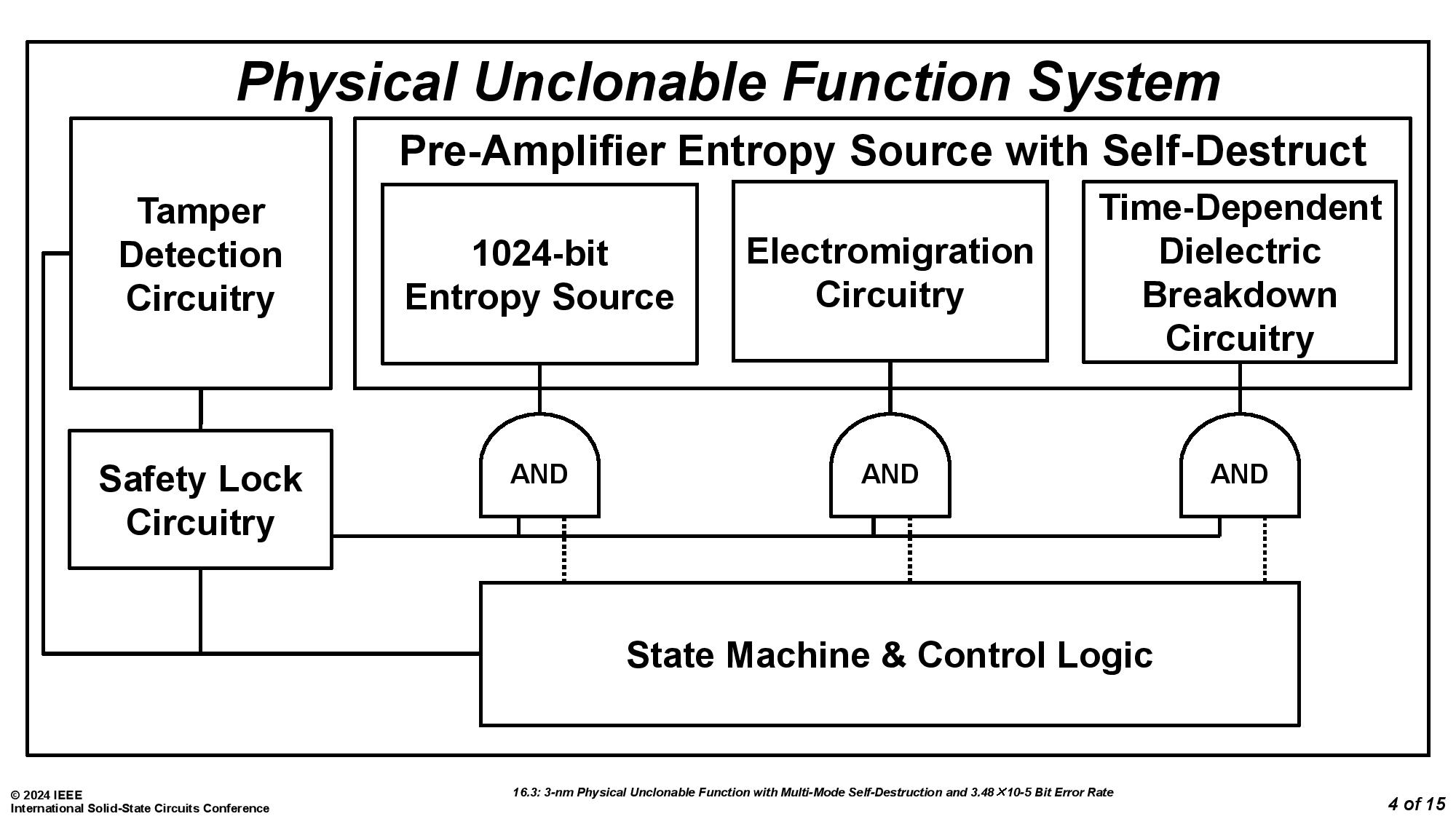
The mechanism works by using physically unclonable functions (PUFs), which can create unique fingerprints for every chip. The PUF, as implemented by the University of Vermont team debuting this self-destruct mechanism, also comes with an extra bonus of two built-in methods of "circuit suicide."
Both methods used pumped up voltages to the lines connecting to the encryption key. In the first method, this causes electromigration, a phenomenon where electricity blows metal atoms out of place, which causes voids and open circuits. The second method instead causes short-circuiting by subjecting transistors meant to operate at under 1V to 2.5V, which causes such rapid time-dependent dielectric breakdown (transistor aging) that the device is killed.
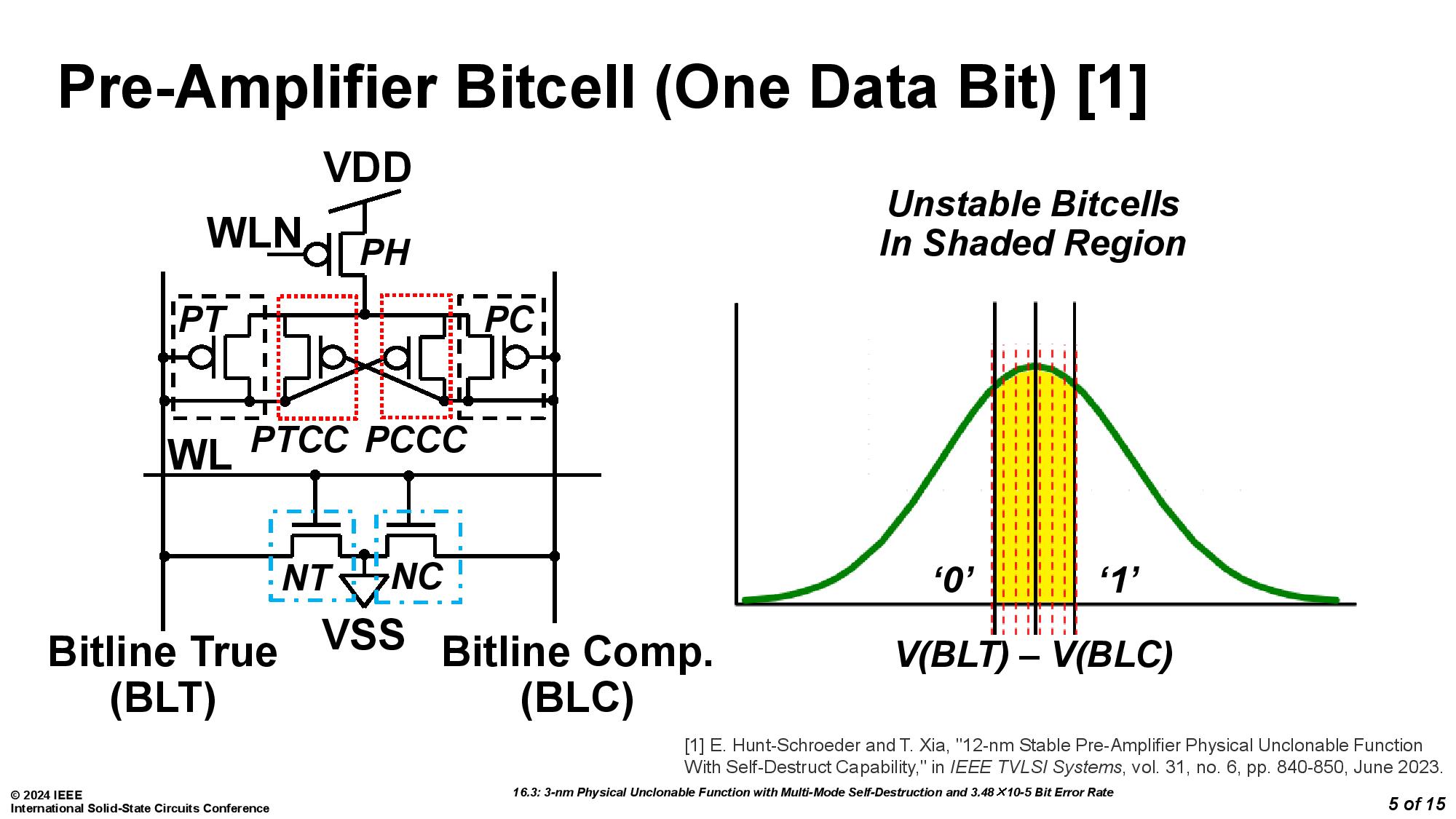
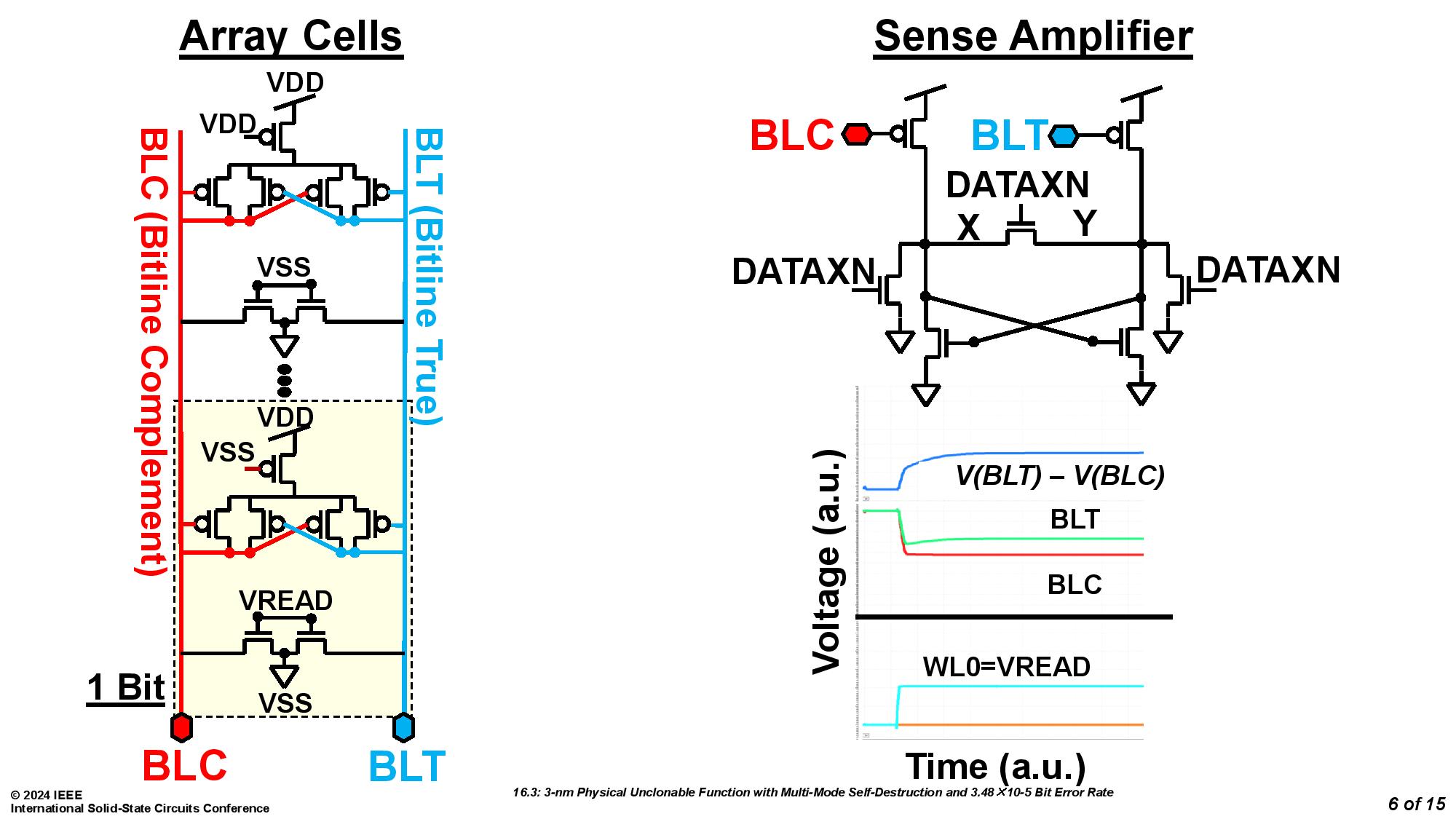

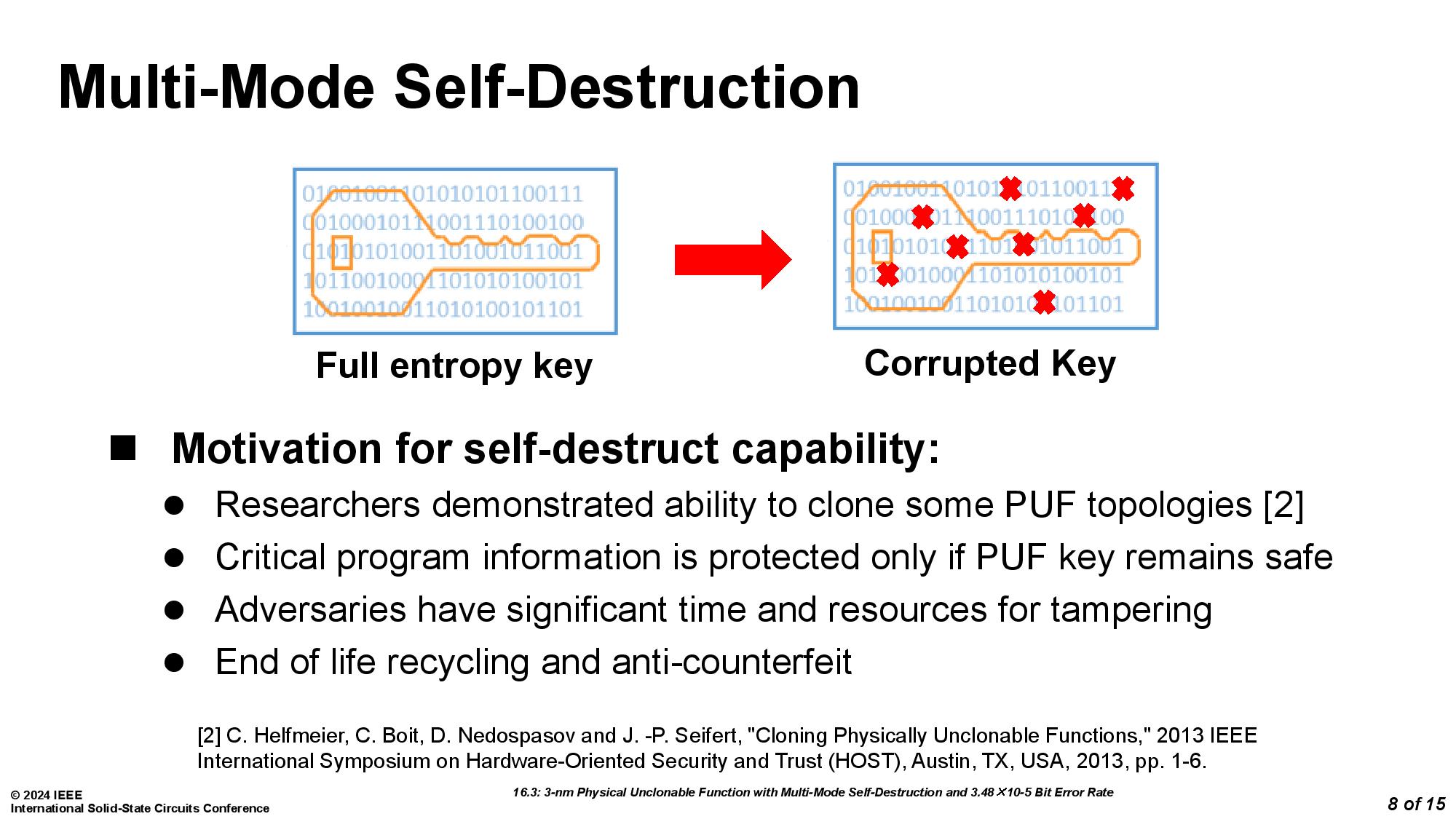
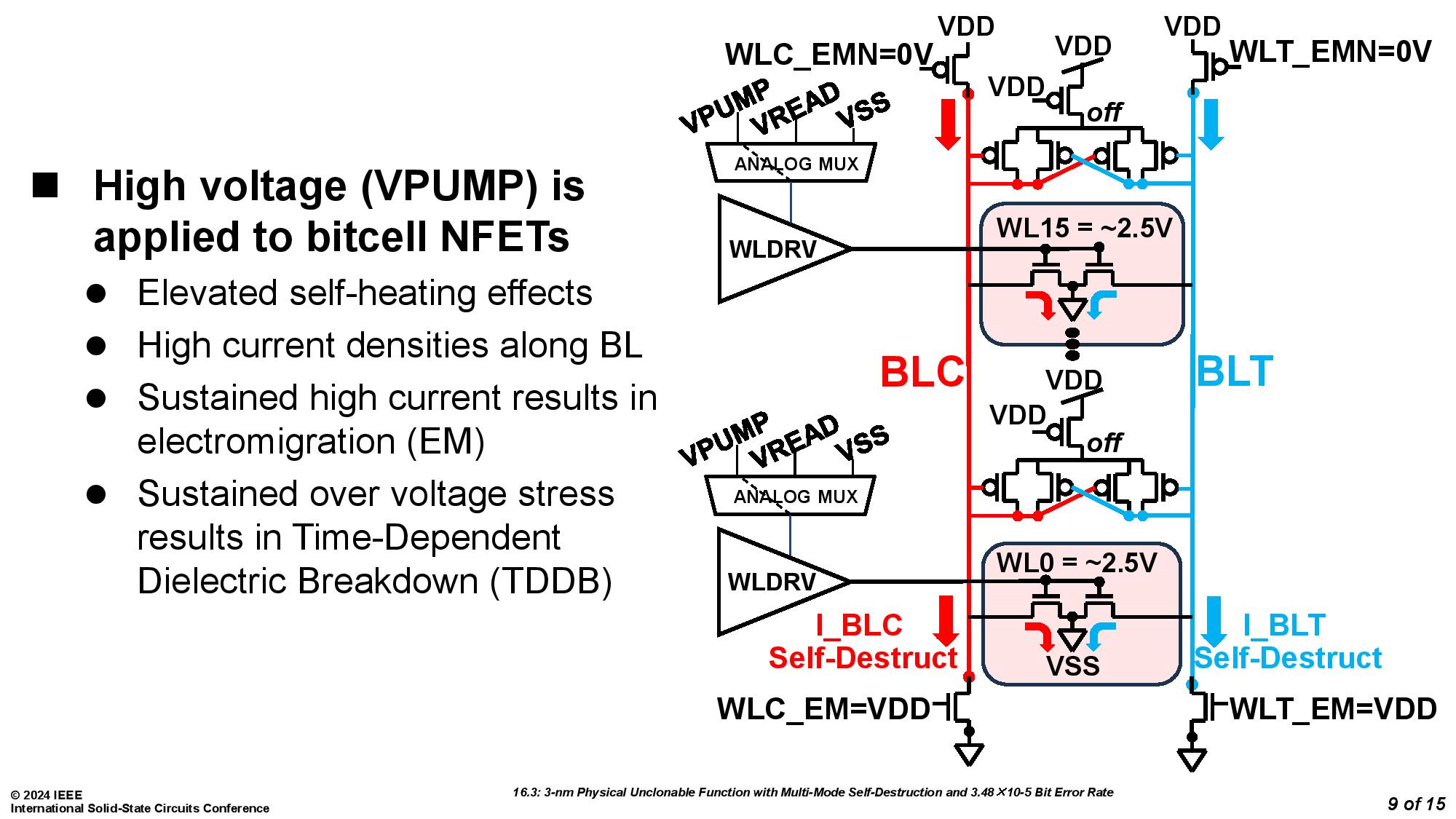
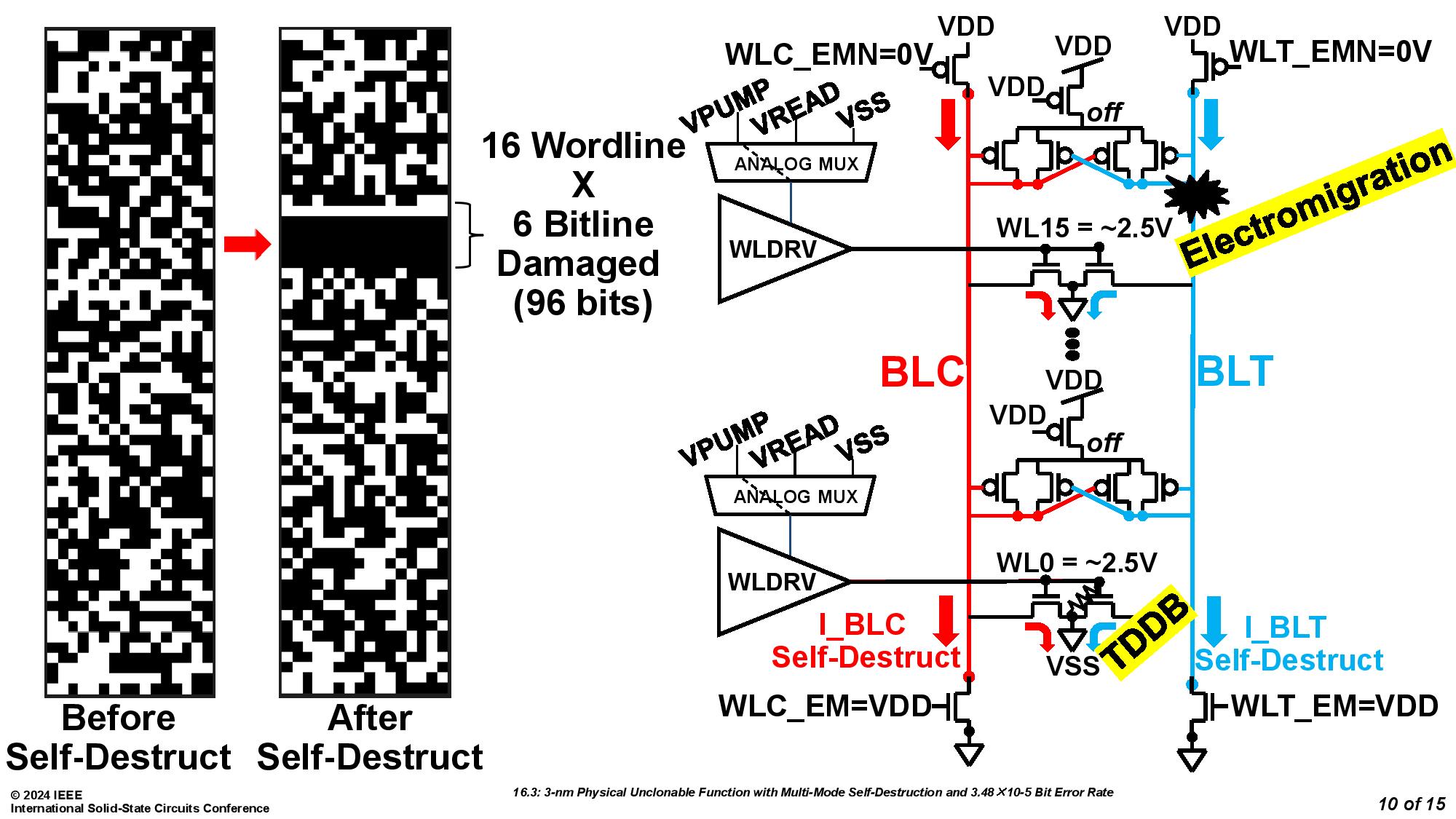
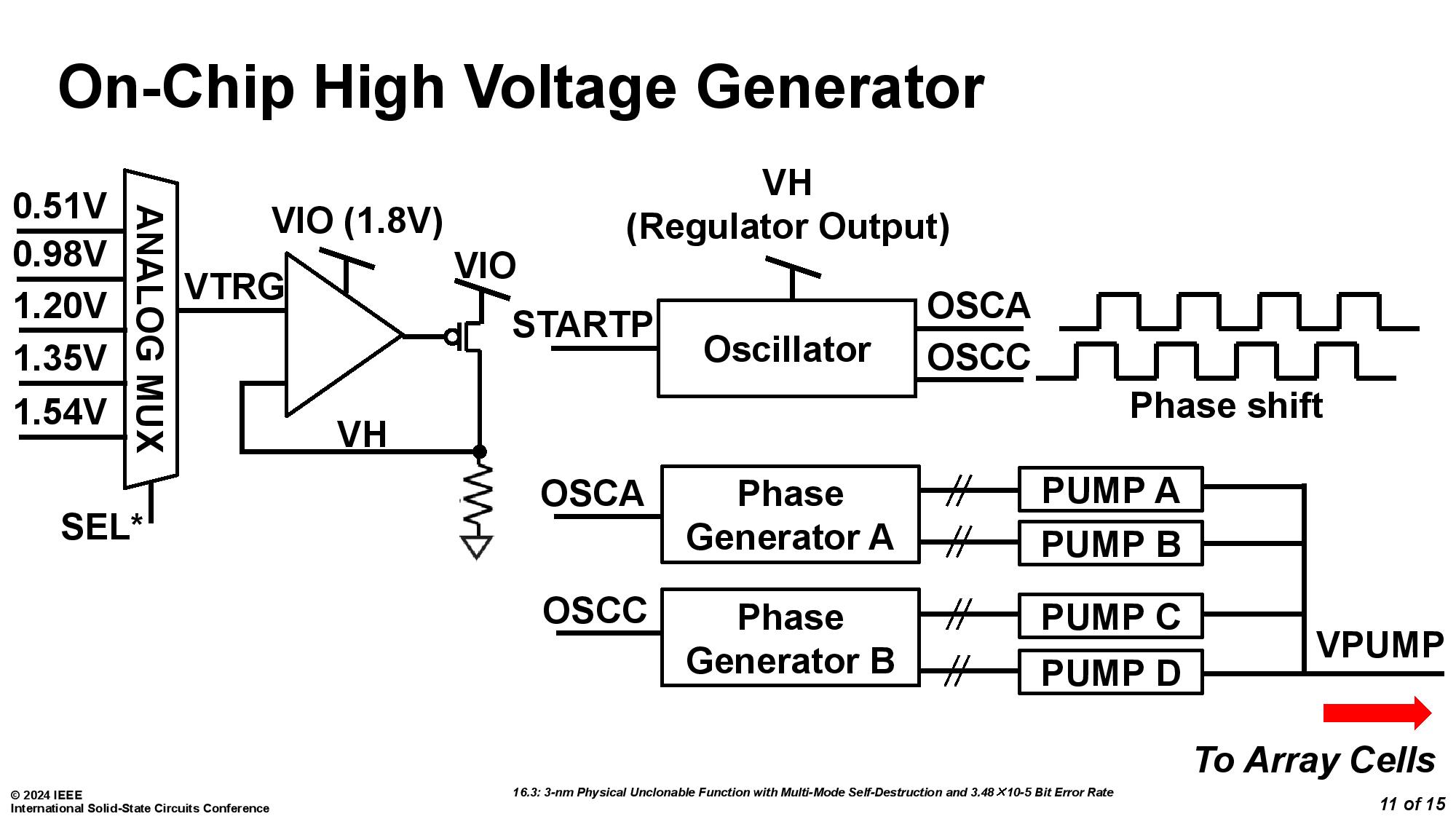
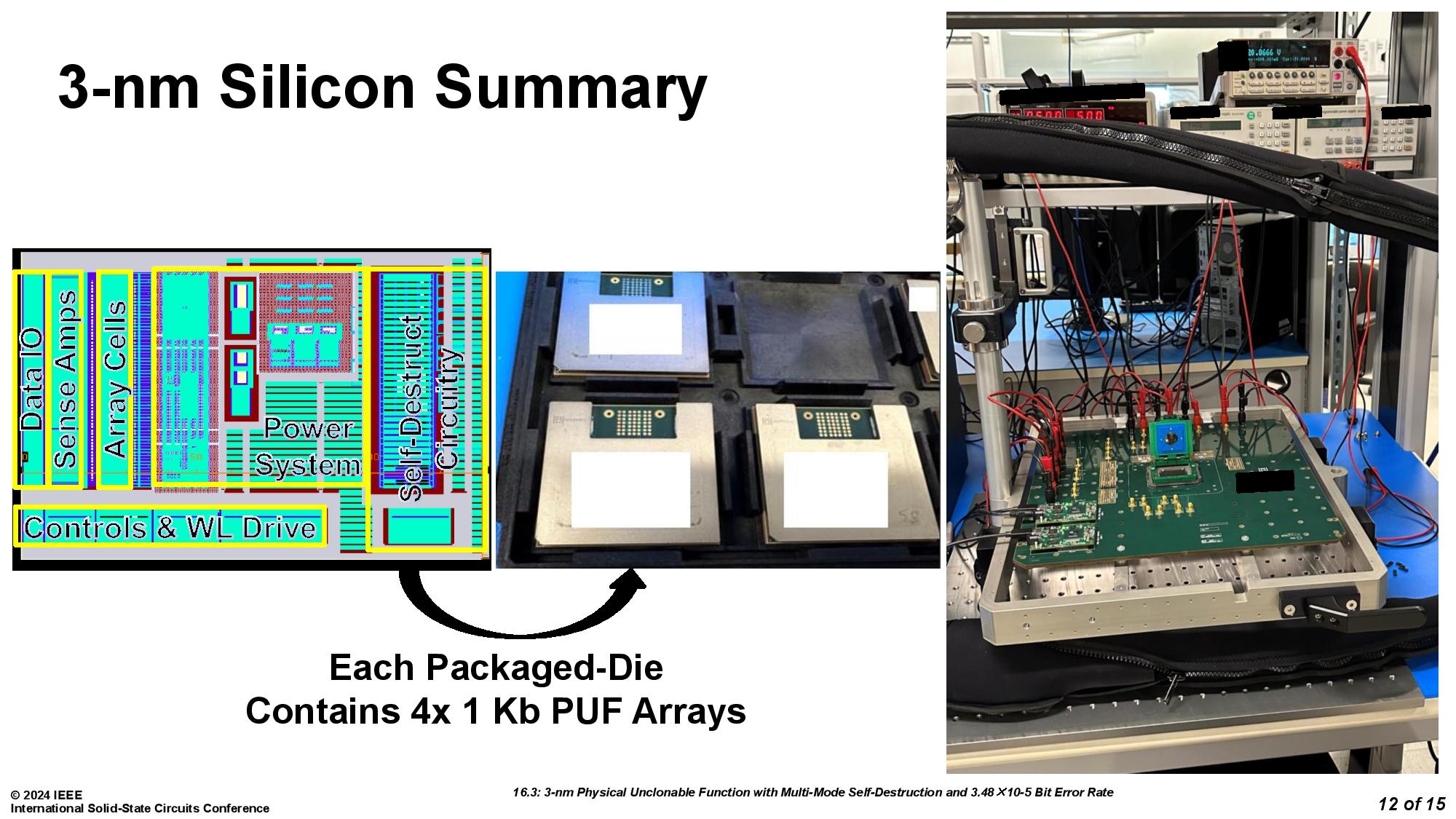
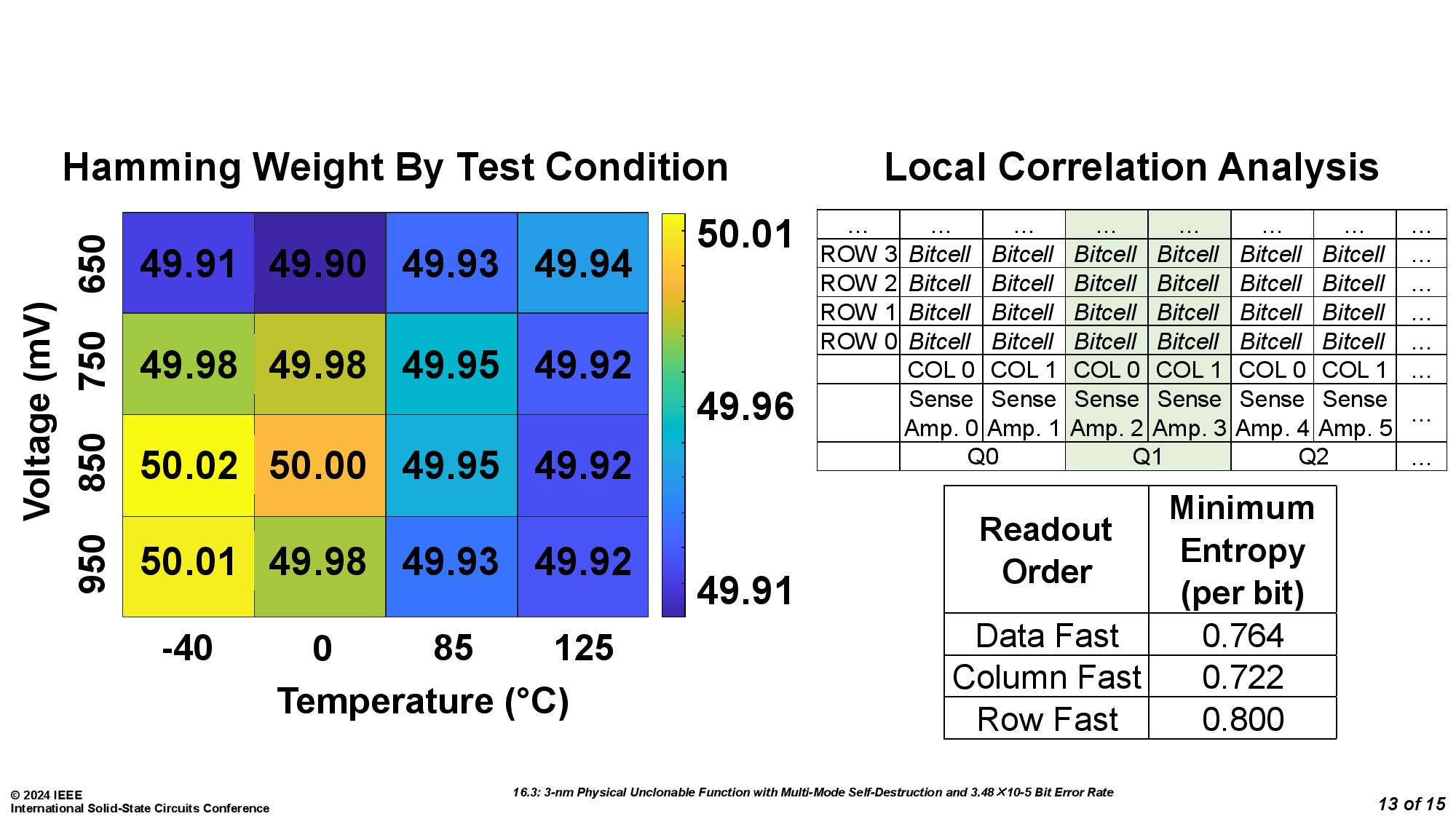
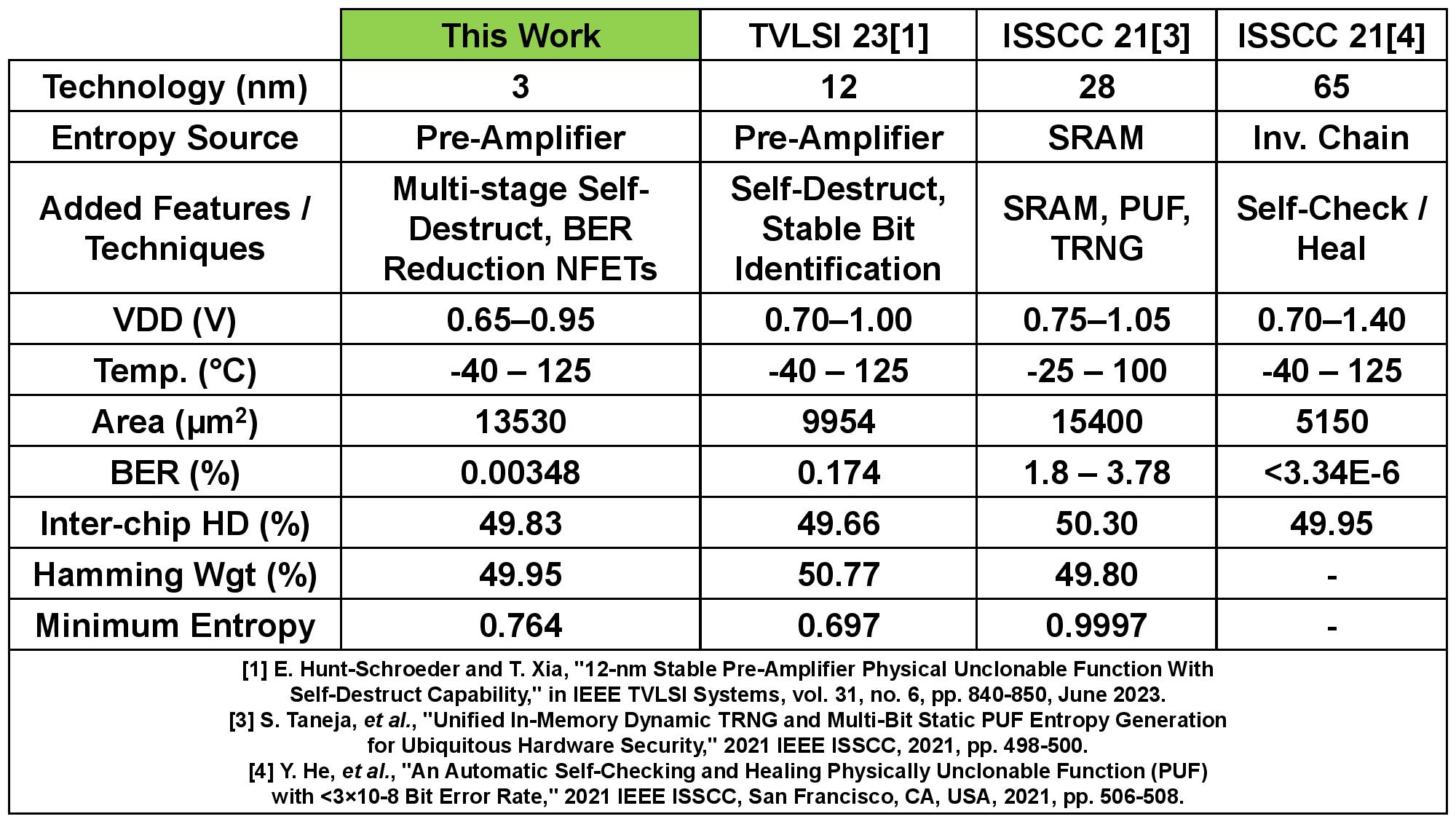

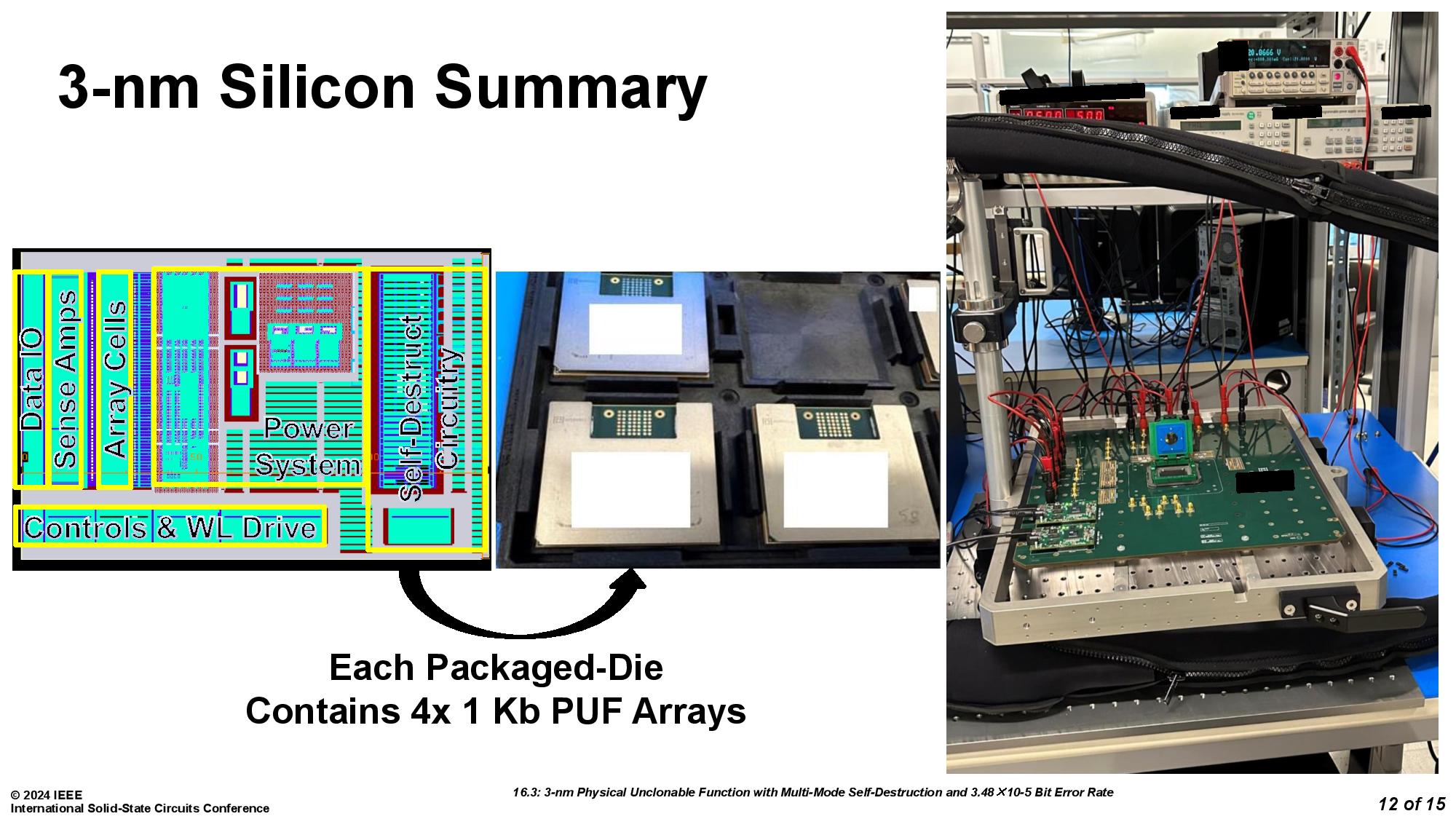
The team from the University of Vermont was assisted by Marvell Technology and led by Eric Hunt-Schroeder, who works at both. The inspiration for this stems from reports that researchers were able to clone PUFs based on SRAM by using an electron microscope. According to Hunt-Schroeder, this method ensures that "When you're done with a part, it's destroyed in a way that renders it useless." The demonstration was conducted with a 3nm test chip.
If self-destruction tech sounds familiar to you, it could be because we've recently covered two different self-destructing USB drives: one from Russian high-tech conglomerate Rostec, and an indie "Ovrdrive" with a unique unlock mechanism that needs modification to enable the self-destruct function.
Other security advances discussed during IEEE Spectrum's blog post include a probe-attack alarm and a built-in electromagnetic signal obfuscation method that prevents EM scanners from cracking keys even after 40 million attempts. Without this protection, the same scanner managed it in 500 tries.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Christopher Harper has been a successful freelance tech writer specializing in PC hardware and gaming since 2015, and ghostwrote for various B2B clients in High School before that. Outside of work, Christopher is best known to friends and rivals as an active competitive player in various eSports (particularly fighting games and arena shooters) and a purveyor of music ranging from Jimi Hendrix to Killer Mike to the Sonic Adventure 2 soundtrack.
-
k8la The CCFB (Crash, Catch Fire, and Burn) undocumented instruction that all 1970's CPUs contained. Actually used in one custom tester where a self-distruct was desired under a specific condition.Reply
Those were very fun times! -
checksinthemail I thought it was specific to the 6809 chip, called "HALT and CATCH FIRE" (HCF). It wouldn't kill it, it would just be the last thing it did before infinitely looping (internally) under a power-cycleReply
https://x86.fr/investigating-the-halt-and-catch-fire-instruction-on-motorola-6800/ -
Steve Nord_ Reply
For general purpose processors, not just a TPU or network credential that lies close to the cipher, these aren't peace loving people. Send 'em to take the shards out of the fields...Admin said:As part of several anti-hacking measures introduced at ISSCC this year, a University of Vermont team created a self-destructing fingerprinting mechanism for different circuits.
Researchers reveal chips that commit 'circuit suicide' — self-destruction and counterfeit protection in one : Read more -
williamcll I can assume this will appear in a lot of phones and gaming consoles when someone tries to jailbreak it.Reply