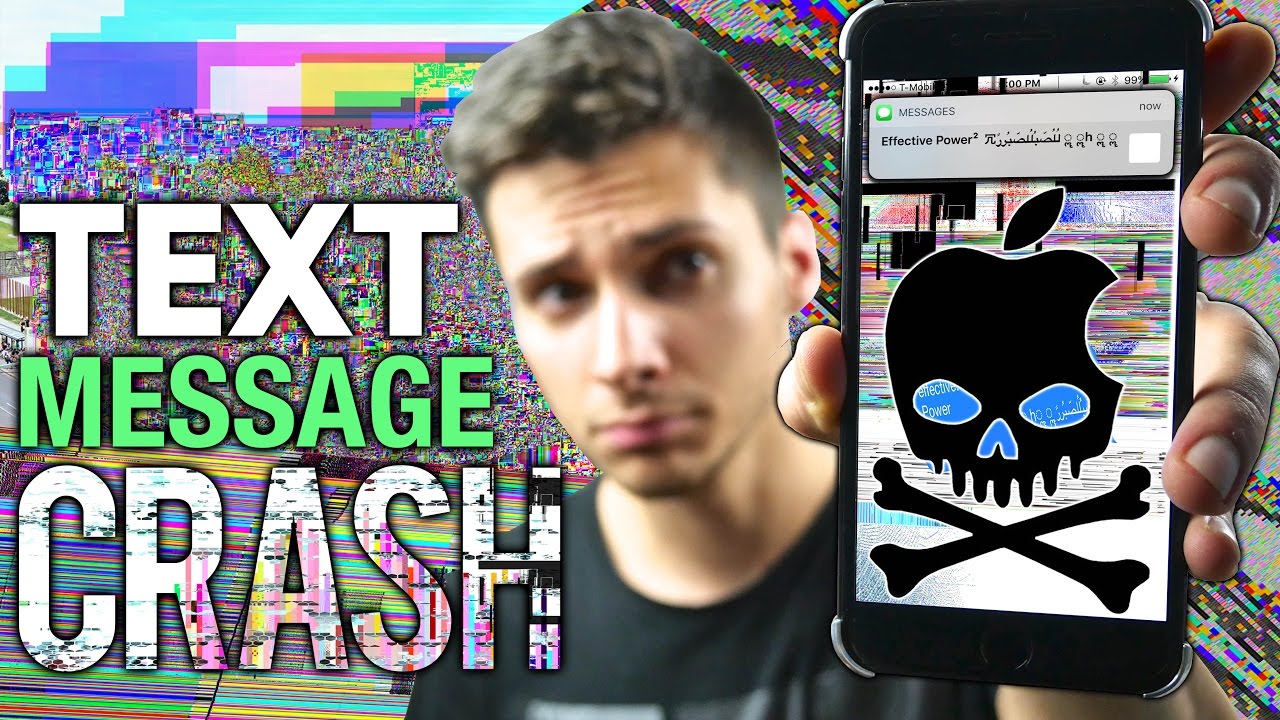
New Exploit Breaks The iPhone's Messaging App With One Text
Yet another way to wreak havoc on someone's life with a single text has been discovered. This time it results from a message containing a large virtual contact file (VCF) crashing the iPhone's built-in messaging app in a vicious loop that ends only if the victim uses a workaround to interrupt the process.
The exploit was discovered by "vincedes3" and popularized by the "EverythingApplePro" YouTube Channel. It works by overwhelming an iOS device's CPU--messages can be opened on iPads or iPods as well as iPhones--in perpetuity. That's because the Messages app helpfully tries to reload the most recent message after it crashes and reboots. If the most recent message is still the one containing the malicious VCF, well, the process repeats itself.
There are a few ways to fix the problem. Perhaps the easiest is to click on this link from "vincedes3" to save a new text message to the device. (With the tongue-in-cheek "I have just saved your iPhone bro ;) twitter.com/vincedes3" as the text.) This will prevent iMessage from trying to reload the message containing the malicious VCF and put an end to the crash cycle--as long as you're using an iPhone. The fix sometimes doesn't work on affected iPads.
So other workarounds had to be found. One involves the affected person using Siri to send a text message to themselves and then clicking the text shown. This should interrupt the crash process. If that still doesn't work, a more complicated workaround has been discovered, but following it will result in the deletion of the last 30 days of messages saved on the device. It involves tinkering with Airplane Mode, date settings, etc., and can be found here.
This exploit comes just a month after the discovery of a similar problem with Messages. That issue relied on a five-second video with a memory leak being sent to an unsuspecting iPhone owner. Watching the video would make the entire phone freeze up; the only way to address the problem is to restart the device by pressing multiple buttons at once. Both revelations make it clear that Apple has to fix a few things with its messaging software.
Still, at least these problems are being revealed to the public alongside their fixes. It would be far worse if criminal hackers or intelligence agencies secretly exploited these issues, which has probably happened already, or if the attacks were revealed but their workarounds remained secret. Crashing someone's communications app or their smartphone is no laughing matter; better to know these things can happen than remain ignorant to the risk.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
bigpinkdragon286 Perhaps the form over function policy can be relaxed a little so Apple can design software from a security standpoint first.Reply -
jkhoward Have a friend send you a text message, hit the notifcation and it will open your friends text instead of the last opened text..... i found an exploit away ago where you send a text with over 5000 emojis and it does the same thing.Reply -
albeit I wonder if this can still happen if you are filtering unknown senders the sender is not a contact.Reply -
Barney_6 Obviously not dummy, the fault is opening the contact card which u would not do if u never saw the message cause it was filtered outReply