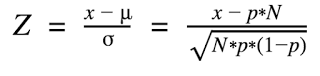Google Explains How It Can Catch Malware Even When ‘Verify Apps’ Is Turned Off
Google’s anti-malware solution, “Verify apps,” works much like a cloud-based antivirus tool. The company uses Verify apps to block infected software from being installed on Android devices, even when users sideload apps from marketplaces besides Google Play, and warns users who already have the software installed on their devices about the security risk. That's if they have Verify apps enabled, that is--if they don't, Google has to get creative.
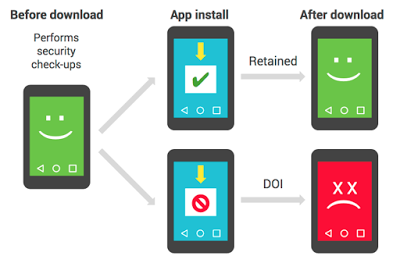
Dead or Insecure (DOI) Apps
Because some users do turn off Verify apps, or because some malware can disable the Verify apps functionality through root access, Google was forced to find alternative solutions to stop certain malware from spreading to other devices.
The company considers the devices that have Verify apps disabled Dead or Insecure (DOI). If certain apps appear to be on enough DOI devices, they are also considered DOI. Google said it uses this DOI metric along with other security measures to determine whether certain apps may be “Potentially Harmful Apps” (PHAs) that need to be blocked.
How The DOI Metric works
A device is retained if it continues to use the Verify apps service to check apps for malicious activity regularly. If an app’s retention rate deviates too much from the average retention rate of the other apps, that specific app would be flagged as a DOI app.
Google even showed the formula that it uses to check when an application may be a DOI app. The formula is based on the following factors:
- N = Number of devices that downloaded the app.
- x = Number of retained devices that downloaded the app.
- p = Probability of a device downloading any app will be retained.
The above formula, which shows a final Z-score (the DOI score) is used to rank apps based on their low retention rate and number of downloads. If an app has a low retention rate and a high downloading rate, it shoots to the top of the DOI list.
From there, Google combines the DOI score with other security factors to determine whether the app should be classified as a PHA. Verify apps is then used to prevent new installations of the app and to uninstall the PHA from devices where it’s already been installed.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to Google, this formula has already helped it identify and stop a few malware families such as Hummingbad, Ghost Push, and Gooligan.
The approach allows the company to stop malware-infected applications from gaining popularity, but to even get on Google’s radar, they have to infect a non-negligible number of devices first. That means Google’s Verify apps is not sufficient, or may be quite ineffective in stopping more targeted attacks. That’s where improved sandboxing and anti-exploit features can help, as well as a more robust updating system, the latter of which has been quite an issue for the Android ecosystem.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
drajitsh My Samsung galaxy note 3 doesn't have the verify apps options. Am I missing it or it is really absent. I went into the security settings and it is simply not there. I'm running android 5 with security patch version 2016-08-01Reply -
lun471k @Drajitsh this must be a feature in the latest version, which is 7+ (7.1.1 on my Nexus 5X).Reply -
MrMojoRisin @Drajitsh - the verify apps feature has been around for a while. I'm still running version 4.4, and the verify apps option is there, under settings - security.Reply