Memcached Amplification Attack Breaks New DDoS Record At 1.7 Tb/s
Arbor Networks, a distributed denial-of-service (DDoS) protection and network security company, confirmed that malicious actors launched a new record-breaking DDoS attack with a bandwidth of 1.7 Tb/s. The attackers took advantage of the same memcached server vulnerability that they’ve been exploiting since last week.
Setting A New DDoS Record, Again
As Cloudflare revealed last week, malicious actors have started abusing an amplification attack technique against vulnerable memcached servers. This allows them to trick the servers into sending large data packets to the attackers’ intended targets in order to disrupt those companies' services. Cloudflare noticed attacks as large as 260 Gb/s, which it considered to be large for this type of technique.
Soon after, Akamai announced that it has already seen a record-breaking DDoS attack of 1.3 Tb/s against its customer, GitHub. The attack was larger than last year’s record-breaking 1.1 Tb/s DDoS attack against OVH, a web hosting provider.
However, mere days later, Arbor announced that its DDoS threat data system recorded an even larger 1.7 Tb/s attack. The malicious group behind the attack targeted an unnamed U.S.-based service provider, which seems to have been able to fully mitigate it without any interruption to its services.
Welcome To The New Tb/s DDoS Era
Arbor believes that we’ve entered a new era in which Tb/s DDoS attacks will be common, whether it’s through memcached server vulnerabilities or through other vulnerabilities attackers may be able to find later.
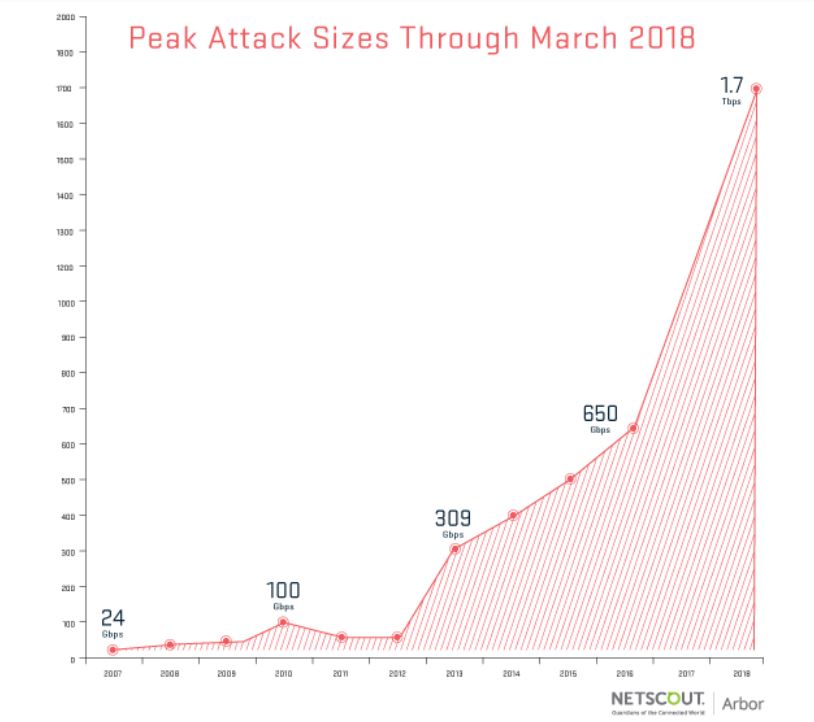
Arbor’s data from the past decade seems to show (in the image above) that the bandwidth of DDoS attacks has been growing exponentially, from around 24 Gb/s in 2007 to 1.7 Tb/s in early 2018. That’s roughly a two orders of magnitude increase in about a decade.
The good news is that DDoS protection firms, as well as larger enterprises that can afford to implement their own DDoS protection, are starting to become better at resisting these increasingly large attacks.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
If companies continue to prepare properly each year, then they may be able to stay one step ahead of the attackers. Plus, if they do that well, then they also won’t need to be afraid of any DDoS extortion from scammers, either.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
kuhndj67 Must really suck when you put together a truly epic attack and your target soaks it up without effect.Reply -
anbello262 Reply20767529 said:Must really suck when you put together a truly epic attack and your target soaks it up without effect.
Unless you work for Cloudfare
*tinfoil hat* -
jaber2 "targeted an unnamed U.S.-based service provider, which seems to have been able to fully mitigate it without any interruption to its services."Reply
I wonder who