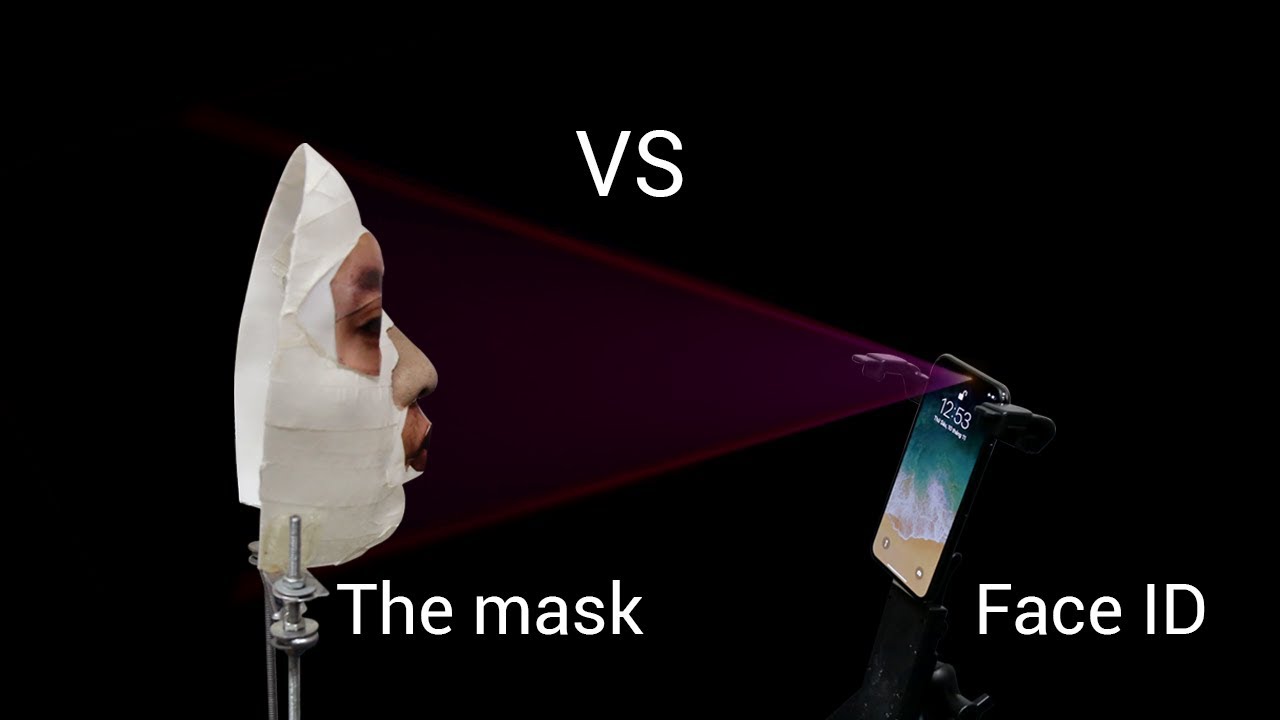
Face ID Spoofed With 3D Printed Mask Sourced From 2D Photos
The iPhone X was released on November 3. By November 9, a Vietnamese security company called Bkav was able to bypass the phone's new Face ID authentication system with a mask created from 2D photos.
Biometric Spoofing, Face Authentication Edition
Biometric security has never been sold as a more secure alternative to passwords. Instead, biometric authentication is supposed to be much more convenient to use, and to in turn convince more people to protect their devices instead of leaving them unprotected. This way, the “average” security of smartphones rises, too. However, as a standalone authentication method, strong and unique passwords will always be more secure, while biometric profiles will be both at risk of being spoofed as well as being stolen from devices.
When Touch ID, Apple’s fingerprint scanning technology, launched with the iPhone 5s, some security researchers from the Chaos Computer Club were able to bypass the system with cloned fingerprints. In this case, the spoofing was “easy” because the researchers already knew exactly what they needed: an exact copy of the iPhone owner’s fingerprint.
It wasn’t quite so easy this time around, because to give the Face ID system a “match” you’d also have to first understand how Apple captures the user’s 3D image. Unlike Samsung’s own face authentication system, which simply uses raw data of person’s face, and can be spoofed by a regular 2D photo, Apple used more advanced algorithms to capture 30,000 data points from a person’s face, in 3D.
According to Bkav, this is why previous attempts to spoof Face ID from Wired had failed. Bkav said that Wired lacked the necessary security knowledge and understanding of Apple’s machine learning algorithms.
This is also likely why it took a little longer to defeat the Face ID system -- the Bkav team needed sometime to reverse-engineer Apple’s algorithms. However, now that they know how to do this, it should take them much less than a week to spoof the next smartphone. Bkav noted that it was also the first company in the world to show in 2008 that laptop face authentication could be bypassed.
How Face ID Was Bypassed
Bkav said that one of its rules for the bypass was that it wouldn’t use the password to unlock the device, as was required in previous attempts to bypass the Face ID system.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
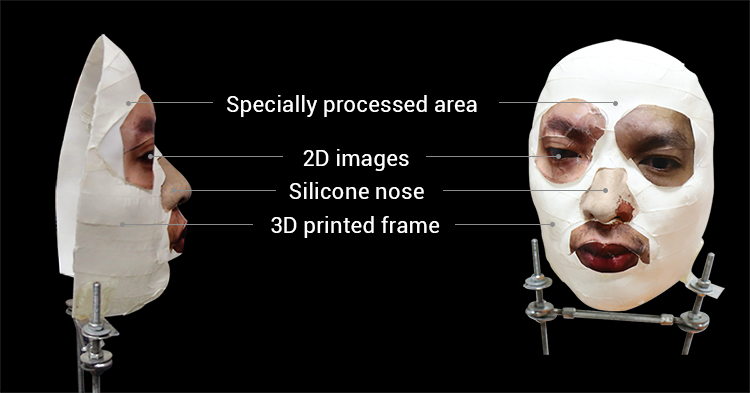
The security company said the bypass required a 3D scanning booth, a silicon nose, and some makeup. In their example, the 3D scanning booth seems to include a room filled with multiple cameras placed at different angles. However, the photos themselves are not “3D” but regular photos, which are then presumably stitched into a 3D image. The company noted that in the future it should be possible to replace the 3D scanning booth with a smartphone that supports 3D scanning, such as the Sony Xperia XZ1.
The cost of the mask was $150 for the proof of concept, but it could be much lower for someone who has set up a whole operation to bypass the iPhone X’s Face ID system.
Fingerprint Readers Still More Secure
The Bkav team seems to have anticipated that people would want their opinion on which system they think is more secure, fingerprint or face scanning. The company said that fingerprint readers should still be considered the most secure biometric authentication method.
As this author warned in a previous post, the danger of face authentication systems, even advanced ones such as Face ID, is that attackers can more easily obtain your face from online photos than they can your fingerprints.
Once they do that, the “1:1,000,000” False Acceptance Rate (FAR) (compared to “only” 1:50,000 for fingerprints) goes out the window, because Apple’s claimed FAR only refers to random images being thrown at the system.
However, no attacker trying to unlock an iPhone X would ever use random images, so this metric shouldn’t give you much comfort. The attackers would use your online photos to create the 3D profile and/or mask. Unless you tend to take many photos of your fingerprints and upload them online, then in practice, fingerprint authentication may should be safer. The attacker would have to actually stalk you in the real world and grab your fingerprint from something you touched to be able to spoof the fingerprint authentication system.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
willgart fingerprint safer than 3d face scanning. but NOT better than Windows Hello systems. funny to see a "new" technology beated by an "old" one ;)Reply -
alextheblue Reply
Yeah that's the first thing that came to mind. It's substantially harder to fool Hello.20375460 said:fingerprint safer than 3d face scanning. but NOT better than Windows Hello systems. funny to see a "new" technology beated by an "old" one ;)