How to Disable the Annoying SSH Password Warning on Raspberry Pi
Raspberry Pi OS nags you if you don't change from the default password.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
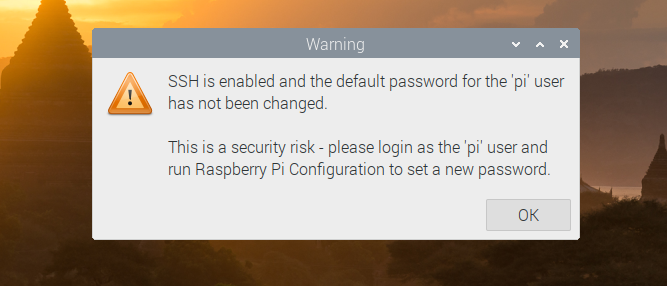
When you set up a Raspberry Pi, assuming you're using Raspberry Pi OS, your system will have a default username of "pi" and password of "raspberry." If you enable SSH for remote access, which is necessary if you're doing a headless Raspberry Pi install, the system gives you a nagging warning message if you haven't changed that password. You get a dialog box on the desktop that you have to click to dismiss and a small text notice in the terminal upon login.
Obviously, changing your password is good security hygiene on any computer, but if you have a lot of different Pis with different cards in your house and you're not allowing SSH access from outside your local network, maybe you'd prefer the convenience of sticking with the default password so you won't forget what to enter as you move from card to card and Pi to Pi.
Fortunately, there's an easy way to disable the SSH password warning dialog box that appears in Raspberry Pi's GUI and the more-subtle warning in the terminal. Here's how.
Disable the SSH Password Warning in Raspberry Pi GUI
To get rid of the dialog box and the need to click "OK" every time you boot up or log in via VNC, just delete the file sshpwd.sh from the /etc/xdg/lxsession/LXDE-pi directory.
sudo rm /etc/xdg/lxsession/LXDE-pi/sshpwd.shAlternatively you can rename the file, just in case you want to bring it back some day. Or, if for some reason, you want to have fun by changing the error message, you can edit the file and change what the dialog box says.
Disable the SSH Password Warning in Terminal
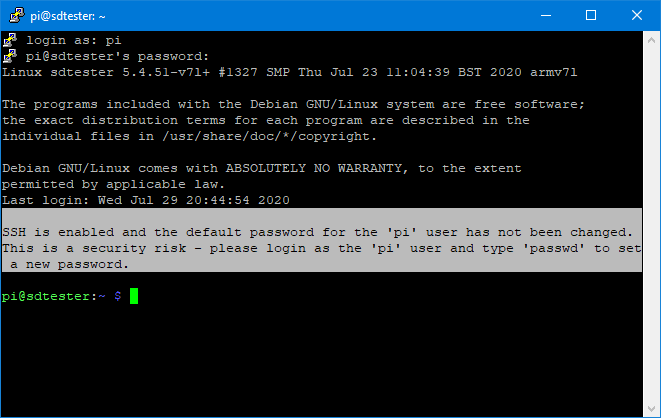
The Raspberry Pi SSH password warning you get when you log into terminal is far less obtrusive. You don't have to click anything to make it go away. However, if you want to get rid of it just delete the file sshpwd.sh from the /etc/profile.d folder.
sudo rm /etc/profile.d/sshpwd.shAnd that's all you need to do. However, if you don't find it too annoying, it might be just as easy to change your password.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Avram Piltch is Managing Editor: Special Projects. When he's not playing with the latest gadgets at work or putting on VR helmets at trade shows, you'll find him rooting his phone, taking apart his PC, or coding plugins. With his technical knowledge and passion for testing, Avram developed many real-world benchmarks, including our laptop battery test.
-
bit_user Replyif ... you're not allowing SSH access from outside your local network, maybe you'd prefer the convenience of sticking with the default password so you won't forget what to enter as you move from card to card and Pi to Pi.
That's a false sense of security. There have been Wi Fi router hacks, infecting them with malware that tries access other devices on the network. Alternatively, some other device or computer on your LAN could get infected with malware, that could also try to access devices on your LAN.
If you want to use the same password on all your local machines, that's potentially okay. Just don't use the default one, and better to make it reasonably strong.
@apiltch , this is really a bad article. A better one would be "Why You Should Change the Default Password on your Devices". -
BertalanD To add to @bit_user's remarks, if an attacker manages to get into your pi and run arbitrary code, with the default password, they now have root access. They can run echo 'raspberry' | sudo -S sh that launches a root shell, which they can use to do all the nasty things they can imagine.Reply
Setting all of the devices to the same password is still more secure than not setting a password at all.
@apiltch: the point about the inconvenience of SSH passwords is valid. You should look up SSH keys and write an article about them. They are more secure than passwords, since they can have 512 bytes of entropy instead of the typical password length of 12-20 characters. The amount of variations in a RSA-4096 key is way more than the number of atoms in the entire universe; not to mention the post-quantum level ECC keys. Please don't teach users how to be lazy and shoot themselves in the foot. -
XaveT I have to disagree in this case. It is NOT our job as power users to withhold information because it might hurt people who use it wrong, especially when it's their stuff and they (at least pretend) to understand the risks. It's our job to share what we know and trust people not to be idiots. The majority will be, but that's not your/our call.Reply
Easiest way to do this is to actually remove the package that does the check.
sudo apt remove libpam-chksshpwd
does it correctly, and without editing stuff manually. -
bit_user Reply
What's this about withholding information? This is not some non-public information the author was privy to, that the public wouldn't otherwise have access to. Your suggestion of withholding is either misguided or misdirection.XaveT said:I have to disagree in this case. It is NOT our job as power users to withhold information because it might hurt people who use it wrong,
The issue is about multiple approaches to solving a problem. The advice given in the article, and the logic upon which it rests, is quite simply flawed.
It's like an automobile publication running an article about how to shut off your "fasten seatbelt warning". There is some information that is quite simply negligent to publish, because the logical consequence of doing so is that readers will be exposing themselves to harm.
You have to think about the audience and understand the difference between ignorance and idiocy. There's an aspect of recklessness in idiocy, whereas an ignorant person simply doesn't know any better. An article like this will have readership with a significant number of noobs, and if the article claims that what it's prescribing is safe to do, many of them will believe it.XaveT said:It's our job to share what we know and trust people not to be idiots.
Just to be clear, on whose behalf are you speaking?XaveT said:The majority will be, but that's not your/our call.
And as surely as it's the site's right to publish, it's my right to call editorial judgement into question. Not necessarily in their forums... but I could certainly take my criticism onto to other social media platforms. -
picaxe For the GUI at least...Reply
How about just modify the sshpwd.sh.sh script to auto close after x seconds ?
(Editing the txt to something subtle is fun too...)
~ Andrew
