One runaway prison laptop caused 1,200 incarcerated students to lose their devices — jailbroken laptop spurs prison officials to issue a recall of now-unsecured notebooks
Even one "Securebook 5" being busted open...on Twitter...with access to tools unthinkable to a prisoner causes the most severe alarm.
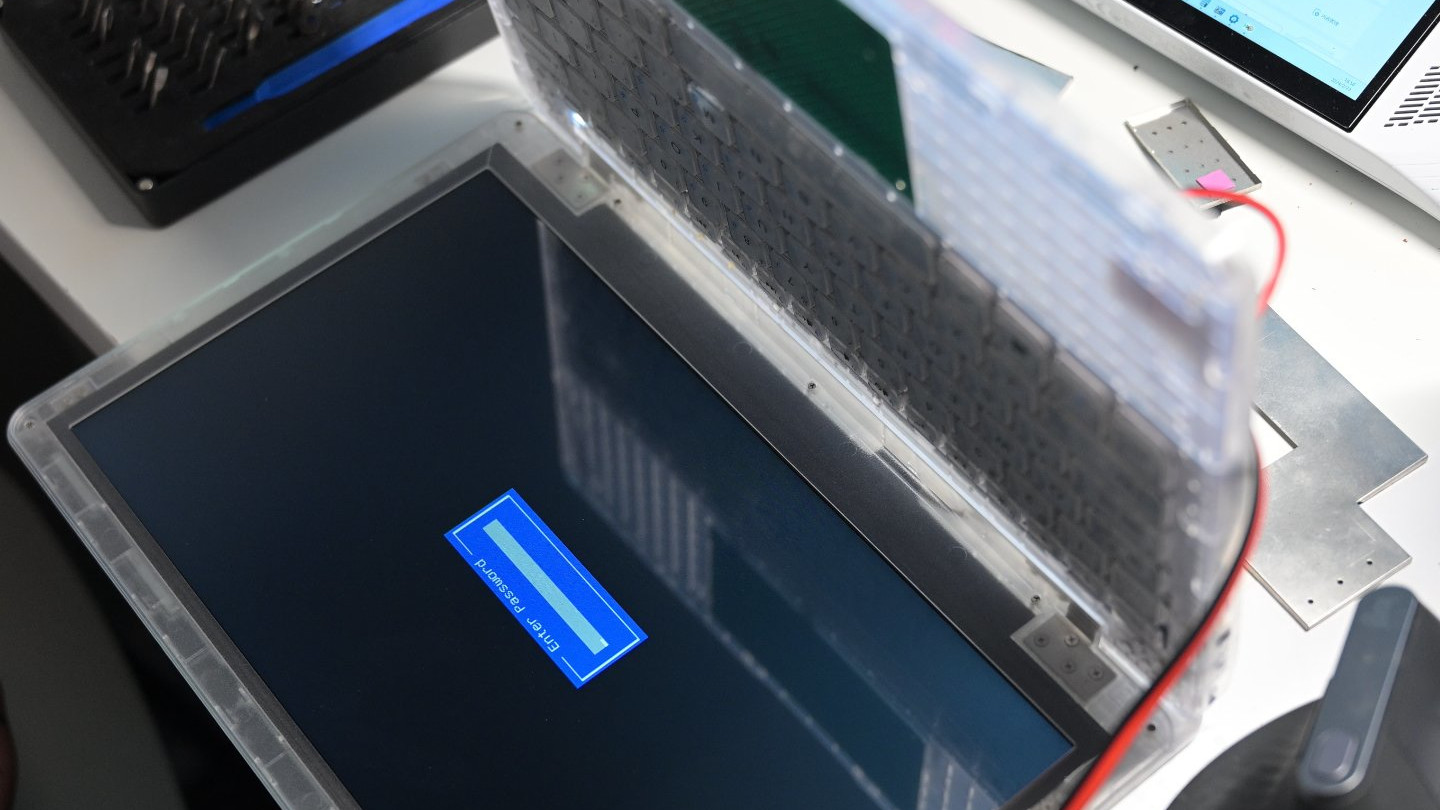
An enthusiast recently "jailbroke" a laptop used by prison inmates for educational courses, ultimately resulting in sensitive passwords being posted online. This has now spurred prison officials to confiscate 1,200 laptops from incarcerated students.
When we reported on the infamous "prison laptop" (or Securebook 5) in February, it was covering Twitter user @zephry_wenting busting open the device by painstakingly replacing the BIOS without removing power to the board and then replacing the default OS by soldering a USB hub onto the laptop. Following the installation of Ubuntu MATE and FreeDoom, one would assume that was the sunsetted end of our pleasant laptop prison break escapade.
Unfortunately, it seems to have collapsed into a series of events, including prisoners having their directly acquired Securebook 5s taken away, around 1,200 units to be exact. According to a piece by Open Campus Media, this happened because Hackaday's coverage included the default password for the OS. The Twitter posts and YouTube videos cited are both now deleted or made private.
Original poster Wenting has already gone on record, saying, "If I knew beforehand, I wouldn't post the original thread." Unfortunately, the government's move to mass-confiscate prisoners' laptops (often locking down the prisoners to do so) still came despite Justice Tech head Jeremy Schwartz's assurance that the work of outside hackers could not be duplicated inside prison walls.
The timing of this move is regrettable because these aren't purely leisure devices by any measure. The laptops were taken immediately before the Winter Quarter Finals of community college classes, which is a pretty pivotal deadline to have your most efficient writing and research consumption tool taken from you. These laptops could run outside of a dock. Still, they could reportedly only upload or download information while connected to one, meaning a lot of existing classwork may already be permanently lost.
Say what you like about the prison-industrial complex. Still, it's at least a little unreasonable to jeopardize the education of people attempting to better themselves in a highly controlled environment. We hope the students have their laptops returned or replaced with their original files intact soon. There was no evidence before this pre-emptive move that anyone inside prison walls was aware of the exploit, could even be made aware of it, or would even be capable of utilizing it to any meaningful extent.
Realistically, those who can secure their tools for adding a USB hub to a laptop that doesn't have it inside prison walls can almost certainly secure a regular PC or phone in the same scenario. People already operating within the boundaries shouldn't be punished for doing so.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Christopher Harper has been a successful freelance tech writer specializing in PC hardware and gaming since 2015, and ghostwrote for various B2B clients in High School before that. Outside of work, Christopher is best known to friends and rivals as an active competitive player in various eSports (particularly fighting games and arena shooters) and a purveyor of music ranging from Jimi Hendrix to Killer Mike to the Sonic Adventure 2 soundtrack.
-
Geef Inmate 124: "It had to be Bruno! He's the only one with a rear able to fit an entire laptop!"Reply -
bit_user 100% agree with the author. This was an unfortunate turn of events.Reply
I'm a little unclear on what was the pivotal issue, though. Was it the posting of the default password for the OS? Was that determined by running a cracking tool, or is that a more serious flaw in its security design? Would that password have any value, absent the various hardware mods he made? -
USAFRet Reply
I would imagine it is the password.bit_user said:100% agree with the author. This was an unfortunate turn of events.
I'm a little unclear on what was the pivotal issue, though. Was it the posting of the default password for the OS? Was that determined by running a cracking tool, or is that a more serious flaw in its security design? Would that password have any value, absent the various hardware mods he made?
No matter how that was obtained. -
bit_user Reply
The reason I was asking how it was obtained is whether his ability to extract it revealed a design flaw in the system, in which case any password could probably be extracted in the same way, or whether it revealed a weak (i.e. easy-to-crack) password. If the former, then the laptops might not get returned for a while, if ever. If the latter, then maybe they could just change the password and return the laptops.USAFRet said:No matter how that was obtained.
Obviously, if the password is usable to compromise the device, absent any hardware mods, then they had to get recalled. Even if the inmates had no direct access to anywhere the password was published, the password could have gotten communicated to them from the outside. -
Alvar "Miles" Udell While unlikely to be able to be taken advantage of, even if they had inside help from a guard, it's still a bad thing if everyone knows the root password to your device, and it's standard procedure for any breached password to be changed, which appears to be what is happening, based on the article posted on Monday about this issue. Personally I wouldn't be surprised if he faces lawsuits over it.Reply
https://www.opencampusmedia.org/2024/03/04/an-engineer-bought-a-prison-laptop-on-ebay-then-1200-incarcerated-students-lost-their-devices/ -
digitalgriffin This is the danger whenever exploits are covered. And why when I talk about them I'm vague. (Ie: it's a physics based attack). You really want to avoid such possibility of giving script kiddies the tools to create chaos.Reply
That said the disposal company is likely to be sued for being non conformant. The laptops should have been torn apart and pieces separated to the appropriate disposal facility. -
GLT1963 the nature of the hack implies a degree in electrical engineering or a good deal of practical experience. this article goes to further highlight the vast chasm between intelligence and smarts. the likelihood of some form of repercussion on the prison usership was very highly predictable even though the nature of the repercussion wasn't. similar things have happened before with several classes of devices. rather than chase fame, i wish people would spend a few days considering the possible negative ramifications of their exploitsReply -
gschoen The fault is really that of the Securebook supplier for not instructing the facility admins that the default password needed to be changed with perhaps a second level of certificate authentication. It is a "Securebook" after all, sold by by "Justice Tech Solutions." The pricing for Securebook 6 is $550 with a 12" screen (resolution unspecified), Celeron processor, 8GB RAM, and 256GB SSD. No OS included, and WiFi is available as an option for some unknown reason. No ports except to connect to a docking station. Needless to say, the company makes a hefty profit on these very basic devices, likely with a kickback to the prison operator, which could be a private for profit corporation. Nothing better than profiting off poor people trying to get an education so they don't come back to prison!Reply
I'd hope they resolve the issue and return the devices. The company should reimburse the students for the semester if they have to repeat due to JTS's error. No chance of that happening, I'd reckon. -
Alvar "Miles" Udell Imagine if passwords were replaced by physical security keys...Isn't that a novel idea in 2024?Reply -
USAFRet Reply
And there would still be a backdoor admin pwd.Alvar Miles Udell said:Imagine if passwords were replaced by physical security keys...Isn't that a novel idea in 2024?
Plus, the admins would not be able to remote in....they'd need to actually touch.