iMessage Crypto Fundamentally Broken, Apple Must Replace It, Say Researchers
After researching the security of Apple’s iMessage service for months, Johns Hopkins cryptography professor Matthew Green and a group of his students discovered that it has a fundamental flaw that can’t be permanently fixed. Green recommended Apple replace the service’s cryptography wholesale if it wants its users to have secure communications.
Security Is Hard - Backdoors Only Make It Harder
Green said that this discovery is all the more important now, at a time when the U.S. government is arguing that technology companies shouldn’t use strong encryption and security for devices, if that means the devices and communications can only be decrypted by the users themselves.
The U.S. government, as well as other governments, have also been asking companies to add backdoors into their encryption over the past year. Any vulnerability that is found but not fixed could also be considered a de facto backdoor for governments. Both end up serving the same result: allowing people access to communications between private parties that shouldn't.
Green also said that even though Apple had proficient cryptography experts design the iMessage protocol, they still couldn’t get it quite right. This shows how hard security is -- even without having to worry about government-mandated backdoors:
“I've always felt that one of the most compelling arguments against this approach -- an argument I've made along with other colleagues -- is that we just don't know how to construct such backdoors securely,” said professor Matthew Green in a recent blog post summarizing the findings of the research paper.“But lately I've come to believe that this position doesn't go far enough -- in the sense that it is woefully optimistic. The fact of the matter is that forget backdoors: we barely know how to make encryption work at all,” he added.
iMessage’s End-To-End Encryption Questioned
The flaws that were found allow more sophisticated attackers to decrypt picture and video attachments from iMessage. Although this attack has been made more difficult on recent iOS devices thanks to certificate pinning, someone with access to Apple’s servers could still intercept and decrypt those attachments. End-to-end encryption is not supposed to be affected by a server hack, which is why at this point iMessage’s “end-to-end encrypted” benefit is put into question.
Green did praise iMessage for being the first widely used messenger to even come close to end-to-end encryption back in 2011, at a time when most people were still using SMS texts and completely unencrypted messengers. However, iMessage has always had a centralized key server, which is a major weakness and a “feature” that’s not common on end-to-end encrypted services.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Green thinks that although this remains a najor weakness for iMessage, attacking the key server would mean having the ability to actively manipulate Apple’s infrastructure without getting caught -- likely not impossible for a major intelligence agency, but still quite difficult. Whoever manages this would also only be able to intercept real-time communications, but not communications that have already been encrypted.
As big as this problem could be (in the context of an end-to-end encrypted messenger that should never even have this issue), an even more significant problem would be if an attacker could also get messages that have already been sent. And that is indeed what Green and his students discovered that is possible.
Why The New Attack Works
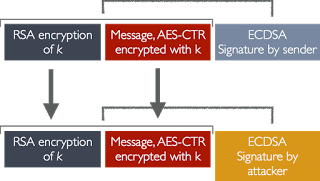
It seems that the attack works is because Apple doesn’t authenticate the messages, which allows for tampering. The company only uses an ECDSA signature, which can be intercepted and replaced by a man-in-the-middle attacker that has access to Apple’s Push Notifications Service server.
Because the encrypted messages aren’t authenticated, the attacker can modify the contents of the encrypted body to change the message, and through those corresponding changes, it can lead to finding out what the original message was.
Although Green’s team discovered that this attack works for attachments, he said there’s no reason it wouldn’t work for regular messages as well, as long as an appropriate side-channel attack is found.
Apple’s Only Real Fix Is A Short-Term One
The iOS 9.0 certificate pinning feature offers a mitigation by making it harder to recover iMessage ciphertexts, but it’s not a true fix. If there’s a Push Notification Service server vulnerability, then all of these messages could be exposed. Worse yet, Apple keeps undelivered messages for up to 30 days, which means there’s a longer window of opportunity for an attacker to get your messages.
Ian Miers, one of Green’s students (who also worked on the anonymous Zerocoin and Zerocash cryptocurrencies), offered a short-term fix for this attack. The one part of the AES ciphertext that isn’t vulnerable to tampering is the RSA-OAEP portion, which can be used to create a cache of recently-received RSA ciphertexts and reject any repeated ciphertexts (such as the ones the attacker would send to figure out what the original message was).
Green said that for now, this fix should be sufficient, but ultimately it’s a rather weak patch for a fundamentally broken cryptosystem. The professor suggested Apple should move away from the current iMessage cryptography as soon as possible, and maybe even adopt the state-of-the-art protocol already used by Signal, Silent Phone, Whatsapp, and ChatSecure.
“In the long term, Apple should drop iMessage like a hot rock and move to Signal/Axolotl,” said Green.
Until that happens, the short-term RSA cache fix is in iOS 9.3 and Mac OS X, and all Apple customers are encouraged to update their devices to those latest operating system versions.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu. Follow us on Facebook, Google+, RSS, Twitter and YouTube.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
hpram99 Or switch to a 3rd party application for secure IM's.Reply
iMessage only works on i-devices and Macs, so there's limited appeal. -
dark_knight33 ReplyTom's, fire your proof-reader. They're doing a terrible job.
Man they fired that guy years ago. Bad spelling, grammatical, errors, and preposition abuse are all common among the THG staff. :P