CosmicStrand Malware Infects ASUS, Gigabyte Motherboards
A very earthly threat reaches hardened UEFI BIOSes.
CosmicStrand is the latest in a string of sophisticated malware that reaches hardware bits you'd think were much harder to breach than your typical OS installation. But harder to breach doesn't mean unreachable, as any cybersecurity researcher will tell you. Researchers have recently found strands of a particularly nifty piece of malware lurking in both ASUS and Gigabyte motherboards based on Intel's H81 chipset. CosmicStrand has evolved since its first appearance back in 2016, and it's currently unclear if the breakout is confined to both companies' offerings of the larger motherboard market yet holds a darker revelation.
Researchers from Kaspersky labs found the malware stranded in the motherboards' Unified Extensible Firmware Interface (UEFI) - their boot sector, so to speak, which is tasked with identifying, verifying and booting up all the connected hardware bits. From simple fans spinning up all the way to your PC's overclocking capabilities on the latest and greatest gaming CPUs - it all leads to your PC's BIOS. For the sake of clarity, this isn't the first such threat discovered - but one is already too many, and it does add to possible infection vectors.
Being the first thing to run within your system - long before any antivirus solution you might have can even be loaded into memory - BIOS-borne malware can be exceedingly difficult to remove. It can evade most antivirus applications, can't be deleted by a fresh OS install, and it also naturally survives storage wipes, three of the most common ways of getting rid of security threats such as these.
Things get especially tricky when the malware can deploy itself at the kernel level towards your OS - at every boot. As a reminder, the kernel is the heart of your OS and is responsible for interfacing your hardware with the operating system's high-level functions. Of course, all OSes possess safeguards against kernel tampering, but in this case, Microsoft's solution, ThreatGuard, is neutered by the malware before its execution.
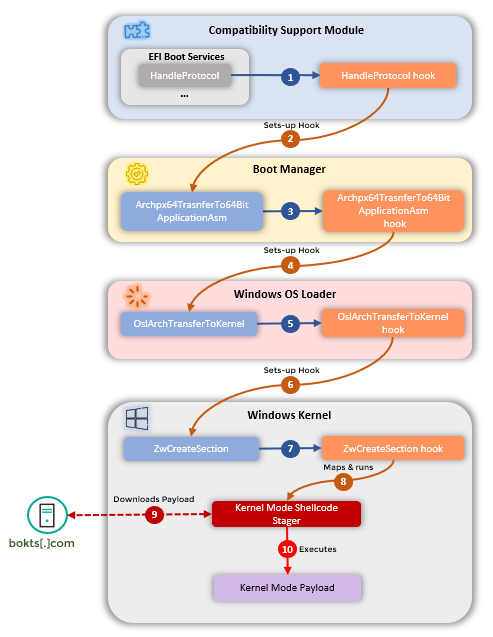
As Kaspersky's analysis of the malware shows, hijacking the kernel allows the malware to control the startup flow of the entire OS, allowing it to prioritize processes that would enable it to reach a command and control server from where it can download the rest of its payload. Kaspersky estimates that this particular malware strand had to be directly written for the motherboards' BIOS - it doesn't seem like it was an internet-borne piece of kit.
For now, the infections seem confined to China, Vietnam, Iran, and Russia. Kaspersky notes that they detected the malware on three of its customers' computers. All of the customers were running different versions of Kaspersky's security software, and none shared any connection via a corporation, employer, or otherwise, adding an air of mystery as to the purpose of the infections in the first place.
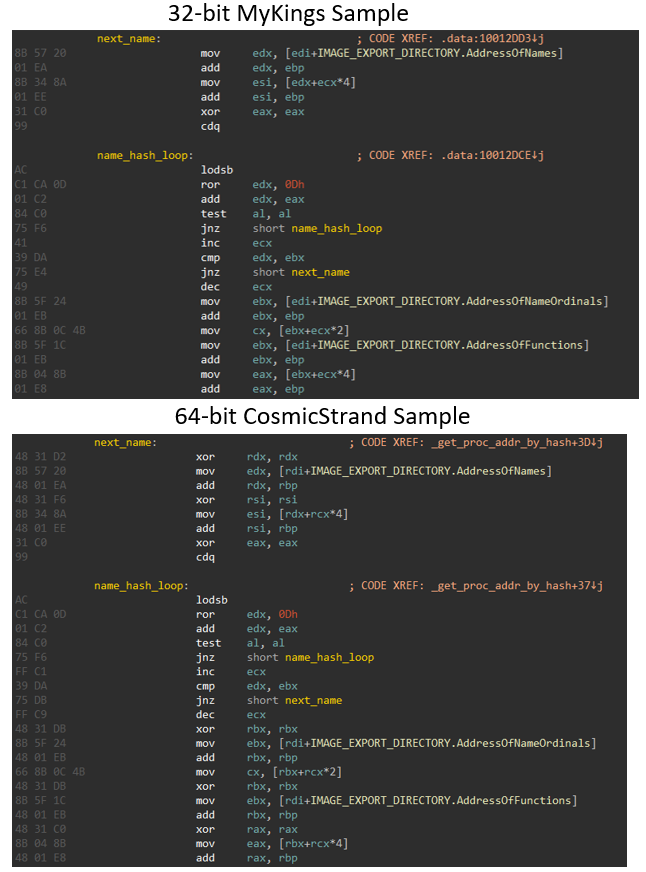
Kasperky's analysis indicates that the adapted CosmicStrand malware was created by Chinese-speaking threat actors due to coding similarities with the payload responsible for the MyKings botnet - which itself included leftover Chinese characters throughout. Of course, this isn't a black and white world: the Chinese snippets could have been placed there to derail investigators. More time - and perhaps more cases - are needed before reaching any definitive answer.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Kaspersky does note that CosmicStrand's characteristics placed its creation back in 2016 - that's how long this infection vector managed to slip by unnoticed. It's currently unclear how many other computers could be infected. We're likely to see infection numbers increase as Kaspersky and other security providers hone in on this threat.
This also raises the question of what BIOS malware might be lurking about today, with years of time to further develop and refine an, until now, unknown threat.
Cybersecurity is - and will never cease to be - a game of cat and mouse between security researchers and threat actors. But considering what we know today about this particular malware infection and how it's achieved, we can only suggest that users be wary of purchasing H81-based motherboards in the second-hand market. If they do, always remember to run an antivirus check, which is a good practice for any PC built around hardware whose parts were in someone else's control.

Francisco Pires is a freelance news writer for Tom's Hardware with a soft side for quantum computing.
-
neojack in the begining of the article, you say that the antivirus can't detect the virus loaded in the biosReply
but in the end you recommend to run an antivirus check when people buy a 2nd hand motherboard ?
Maybe the best suggestion would be to update the bios and reset the setup (factory "optimized defaults")
speaking of it, since a bios update flashes the rom, does a BIOS update deletes the virus too ? is it confirmed ?