Spreading Malware Through Dropped USB Sticks Could Be Highly Effective, Research Finds
Elie Bursztein of Google’s anti-abuse research team tested how effective spreading malware would be through “lost” USB sticks on a university’s campus. He found that 98 percent of the 297 dropped usb sticks were picked up by people, and of those who found them almost half (45 percent) of them clicked on the stored files inside the USB sticks.
Most operating systems, with the exception of Qubes OS, don’t isolate the USB drives from the rest of the system by default. Therefore, if there is malware on them, it could infect the systems either through user action (by clicking on the files) or even through inaction through various firmware vulnerabilities.
Testing People’s Behavior Around “Lost” USB Drives
Bursztein, the researcher behind this project, also tested to see if giving the sticks various labels, such as “Confidential,” or “Exams,” would influence the behavior of those who found them. He discovered that when they were labeled, the people finding them were more likely to open the sticks on their PCs compared to when the sticks had no label at all. However, he also found that those drives that had a return address on them, were much less likely to be opened.
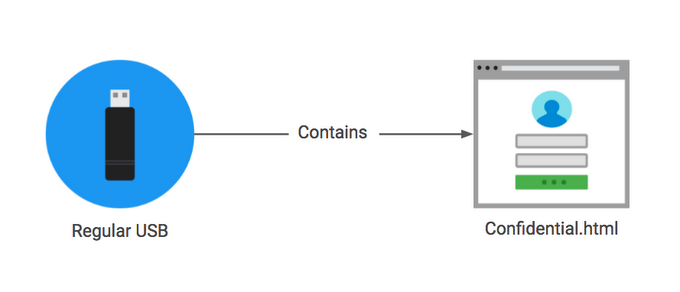
To further test the behavior of those who found the sticks, Bursztein also labeled the files as “private” on sticks that came with physical keys attached, were labelled with a return address, or were unlabelled. The files on the “confidential” sticks were labeled with “business.” None of the files had the expected content on them, though. They were all HTML files with embedded images that were connecting to the researcher’s server, from where he could see which files were opened.
Upon opening the files on the drives, the users were asked if they wanted to participate in a survey, with the possibility of earning a gift card. About 20 percent of them agreed. Over two thirds of those who agreed said that they intended to return the sticks to their owners, 18 percent said they were “curious” about what was in them, and 14 percent gave other explanations.
Potential Attack Vectors
There are multiple ways in which the users could have been infected. The HTML files on which they clicked could have activated malicious code when they were opened, or the users could’ve been redirected to a phishing site that would then try to steal their credentials. There’s also the possibility that an attacker could put malicious executable files on the USB drives. Then, if users clicked on them and allowed the files to run, their systems would’ve become infected.
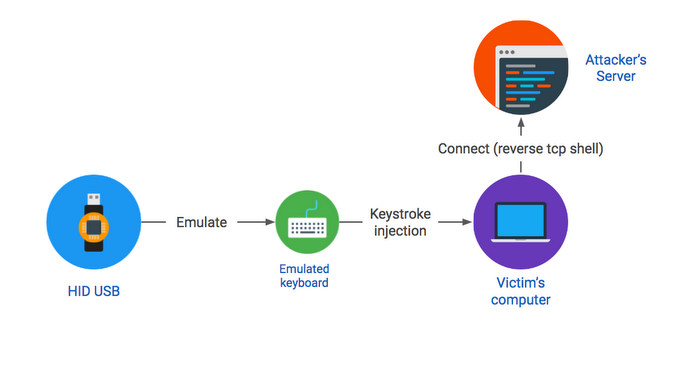
Alternatively, attackers could use devices that physically look like USB sticks but would be recognized by a computer as keyboards. This is a more sophisticated attack done through HID (Human Interface Device) spoofing. It allows attackers to “inject” some keystrokes as a set of commands into the systems, which would then give the attackers remote access to those systems.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
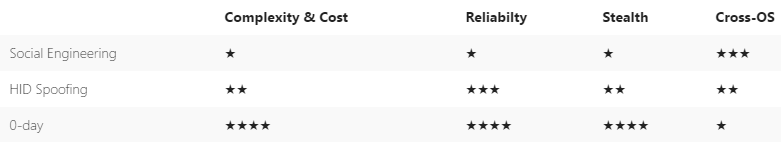
The most sophisticated type of attack done by seeding USB sticks is one that takes advantage of zero-day vulnerabilities in a computer’s USB drivers. This is a method that’s used more often by state-sponsored attackers. One example of such an attack is the infamous Stuxnet malware, which infected Iran’s nuclear facilities.
Because of the complexity and cost, attacks that take advantage of USB firmware zero-days should be more rare. However, large organizations should still be on the lookout for those, as that’s one way large data breaches could happen. Most regular users would be targeted more often with keyboard-spoofing devices that look like USB sticks, or real USB sticks that contain malicious files, which the users may access out of curiosity.
Security researchers recommend that you don't insert random USB sticks into your computer. If you have to open them, at least have your system’s patches up to date. Ideally, one would only open them in a virtual machine, specifically set up for such risky scenarios, or on a system that doesn’t allow writing on its own drive.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
captaincharisma so if you are walking around and find a 250GB USB stick on the ground it's a trap!!! lolReply -
wifiburger I have my doubts how effective it would be, this article assumes 100% of earth population has a computer and knows what a USB stick isReply -
ARCook Actually, I would say a large % of American's would absolutely know exactly what this is for. We are already seeing a large increase in ransomware attacks in Healthcare... Dropping these near a nursing station could easily be successful.Reply
Business are the new targets of cyber criminals, not your home computers. Unsure why you would assume 100% of the earths population would need to be involved for this to have risk... Based on these numbers, 1 in 3 people will cause a failure. So you need 3 people that are computer literate, not 6.5 billion. -
anbello262 I would be one of the people who open the files. Althoug I would most likely do it in a sandboxed environment, though. 90% of the usb sticks you find (completely made up number) will be personal sticks, not malware sticks, I'd guess. Of course, depends on where you live.Reply -
cub_fanatic They did this in Mr. Robot and it didn't work because the prison guard's PC had Avast real-time protection that caught the malware in time.Reply -
targetdrone Reply18386794 said:If you find a USB stick reformat it and you are good to go!
Not necessary. If the firmware of the usb stick is "hacked" merely plugging it into a computer will infect your computer. -
Gunkk0 Well that's how Stuxnet got into the Iran nuclear centrifuges... so of course it'll work. The only thing better would be to print BRAZZERS on them first beforehand...Reply