Elcomsoft Uses GPGPU for Fast WPA/WPA2 Crack
How secure do you think YOUR wireless network is? That's a question that many people might want to revisit later on thanks to GPU-powered general-purpose computing (GPGPU).
Elcomsoft, a privately-owned company based out of Moscow, Russia specializes in Windows Productivity software and utility applications for business and end users. Recently the company released its Wireless Security Auditor suite, capable of cracking WPA/WPA2-PSK passwords in record breaking time by making use of your graphics card processor.
The said software suite makes use of a new technique called General Purpose GPU Computing(GPGPU). GPGPU is a method whereby applications make use of the processor on a high-end graphics adapter to complete standard and complex calculations. Since today’s high-end graphics boards from AMD/ATI and Nvidia are natively capable of processing large amounts of data / calculations per second, they make for prime candidates in mathematical processing outside of the gaming realm – hence the coming of age, GPGPU.
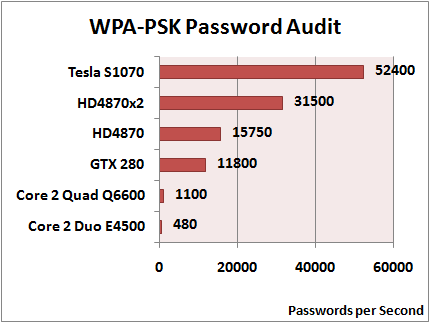
GPGPU - when used for the purpose of cracking WPA/WPA2 wifi passwords - decreases the time it takes to effectively decode the password by hundreds of times. See the chart below for a quick example, provided by Elcomsoft.
Wireless Security Auditor performs advanced dictionary search attacks with mutation to expose weak passwords consisting of words and phrases in spoken languages. The software also allows highly customized mutations of ordinary words to perform hundreds of mutations on each word in order to ensure the most attack coverage possible. Standard alpha-numeric incremental attacks are also supported, but naturally take a long time, even for supercomputers.
As of this writing, it is unknown if users of Multi-GPU systems would gain more performance over those utilizing single GPU solutions. If the use of Nvidia SLI or Triple-SLI could be used, you could drastically decrease the time even more.
Elcomsoft’s Wireless Security Auditor is listed at US$1199.00, but can be obtained for US$599.00 until the end of April of this year.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
-
alvine cool beans! It's just I'm afraid now people will be hacking each other wireless networks and taking personal data like credit cards and such...Reply -
ThePatriot That is why I use a 62 character key (AES) and it is not in any dictionary.Reply
TACACS+ server for SOHO networks? I guess we will have to really soon. -
daft looks like crossfire works at least, considering that the 4870x2 got twice the performance of the 4870. (according to their chart) though, this program isn't new, i read about it back in october if im not mistaken.Reply
http://www.elcomsoft.com/ewsa.html -
Tindytim You can already crack WPA/WPA2 extremely easily. This just cuts down on the time needed to do so.Reply -
Don´t worry, be happy.Reply
You can use a random password and store it in a pendrive, is very easy.
You can use this page to generate it:
http://www.kurtm.net/wpa-pskgen/
With a random pass nobody can crack you Wifi.
Use de calculator 105^63/pass per sec. There are a lot of years. -
Micyia001, the basic answer is yes, it would be more secure. It would be like giving a folder the hidden attribute. Normally people wouldn't see it, but if they turned on "view hidden files" then they could. Likewise, if someone was looking around with a spectrum analyzer (which aren't terribly expensive if you're into war-driving) and launch kismet, etc. then it didn't matter if you turned off broadcasting.Reply
In the real world, war-drivers or even people trying to cause trouble would just move on to easier targets. If it's a neighbor with some time, or someone specifically targeting a person, then turning off broadcasting wouldn't matter. -
Elcomsoft Wireless Auditor is great software. Well for Dictionary Brute Forcing. I could seem to setup a true Brute Force trying every combination. eg aaa, aab, aac. I know this takes alot longer but alot more people are learning no to use dictionary words. Any ideas how to achieve this???Reply