Nvidia RTX 5090 can crack an 8-digit passcode in just 3 hours — password cracking benchmarks show tremendous performance
When it comes to password hacking, the RTX 5090 is anywhere between 33% and twice as fast as the RTX 4090.

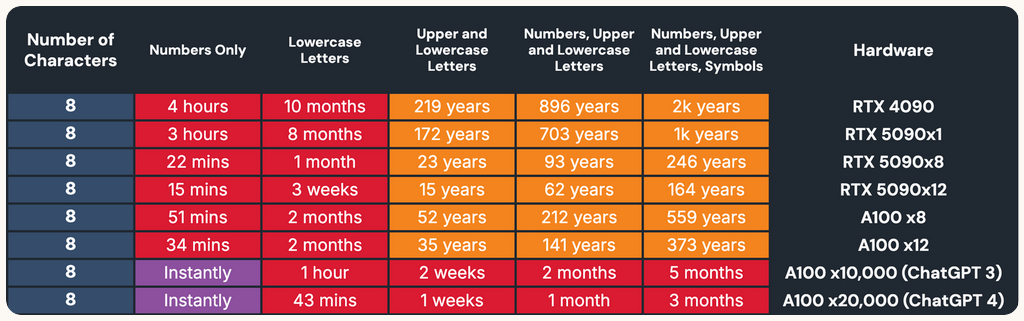
The RTX 5090 is not only good for gaming and AI — it also excels at password cracking. Hive Systems updated its password cracking benchmark suite with 12 RTX 5090 graphics cards — Nvidia's fastest and best graphics card for gaming currently, and found all twelve cards working together can break simple eight-character passwords in under 15 minutes.
Hive Systems is in its 5th year of benchmarking password cracking times on GPUs; the last update they made was in 2024, featuring the RTX 4090. Rather than cracking an actual password itself, the outlet cracks hashes, which are scrambled versions of reproducible text generated by software.
Hashes are a popular method for securing customer passwords against hackers by storing customer passwords as hashes on servers. When hackers go to steal a password database from a company's server that is secured with hashing, all they will see are hashes of the passwords they represent rather than the actual passwords themselves.
Cracking passwords with this method involves making a list of all possible combinations of characters to make a password, then matching them to a stolen database featuring password hashes. Graphics cards are particularly good at this methodology due to highly parallelized computing capabilities.
With 12 RTX 5090s, Hive Systems found Nvidia's latest flagship can crack the hash equivalent of eight-character passwords featuring numbers only in just 15 minutes. Passwords comprised of eight lower-case letters, the dozen RTX 5090s were able to crack in 3 weeks.
On the other end of the spectrum, passwords taking advantage of numbers, upper and lowercase letters would take 12 RTX 5090s 62 years to crack, and 164 years to crack with symbols added into the mix.
For a generation-on-generation perspective, a single RTX 5090 can crack a numerical-only password hash with eight characters in three hours. A single RTX 4090 can accomplish the same task in four hours, representing a 33% performance improvement for the RTX 5090 over the RTX 4090 in this specific scenario.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
However, as the password complexity increases, the RTX 5090 becomes faster and faster in comparison. Moving up to a hash representing an eight-character password made up of numbers, upper and lowercase letters combined with symbols, the RTX 5090 is allegedly twice as fast as the RTX 4090. But cracking a password that complex would take the RTX 5090 a millennium to accomplish.
Hive Systems' research demonstrates the dangers of low complexity passwords and how adding just a bit of complexity in the form of symbols, capitalized letters, and numbers can make a huge difference for security. The good news is that cracking hashes in the way Hive Systems demonstrates requires hackers to have a stolen database of password hashes in the first place. Without this, hackers can't brute-force hack password hashes.

Aaron Klotz is a contributing writer for Tom’s Hardware, covering news related to computer hardware such as CPUs, and graphics cards.
-
Zforgetaboutit I feel the title is missleading/vague/clickbait: it looks like a single GPU can achieve the claimed activity in 3 hours.Reply -
Jame5 It can. A single 5090 can crack an 8 digit passcode (numbers only) in 3 hours. It shows it directly in the chart embedded in the article.Reply -
Alvar "Miles" Udell And this is why most places won't let you make a password that doesn't include a combination of upper case and lower case letters, numbers, and special characters.Reply
But also most places also have at least basic SMS or email 2FA passcodes, and those that don't, like forums and other low security places, have Google or other sign in options which themselves are 2FA'd.
TH should do an article "Why you should have a 'junk' Google account" exactly for situations like that. -
DS426 "The good news is that cracking hashes in the way Hive Systems demonstrates requires hackers to have a stolen database of password hashes in the first place. Without this, hackers can't brute-force hack password hashes." - AuthorReply
To broad. A measly Radeon 7900 XTX ramming thru about 100 million NTLM hashes per second could purely brute force in about 25 days for an 8-character password with letters and numbers. Interestingly, bcrypt with a cost of 10 increases this number to about 17,000 years, demonstrating how much impact the different hashing algorithms have on password anti-cracking security.
Would have been nice to also show their table that shows longer passwords as this really drives the message home on the importance of longer passwords.
Don't want to give a false sense of security when possible. Hackers can and will use even more GPU's to speed up this process, such as distributed clusters of multi-GPU systems, and cracking tools exist that are able to utilize those (>12 GPU's). Yes, it's going to be cost-prohibitive outside of well-resourced attackers, though renting GPU compute is possible and might be done for targetted attacks where continuous or near-continuous 24/7/365 hashing isn't needed. -
LaminarFlow I'm absolutely in favor of enforcing long password with special characters when creating one.Reply
But please for the love of god don't force me to use only specific special characters deemed worthy for whatever reason. -
Eximo Those password limitations actually make them easier to crack, since many people go for the minimum length following the rules. You can eliminate a huge number of potential passwords if you can find out or try the basic password template rules first.Reply
I believe the common wisdom is still to string together long dictionary words (making them easy to remember) and salting in the special characters and numerals required. -
Heiro78 Reply
Not to mention it's brute force. Most accounts requiring passwords lock themselves after a set number of attempts.Zforgetaboutit said:I feel the title is missleading/vague/clickbait: it looks like a single GPU can achieve the claimed activity in 3 hours. -
Heiro78 Reply
CrackhUg3w1sd0m$alT1ngEximo said:Those password limitations actually make them easier to crack, since many people go for the minimum length following the rules. You can eliminate a huge number of potential passwords if you can find out or try the basic password template rules first.
I believe the common wisdom is still to string together long dictionary words (making them easy to remember) and salting in the special characters and numerals required.
Like this? But won't the crackers know to replace letters with their special character equivalent? It surely slows them down, I suppose.