Google Breaks SHA-1, And Not A Moment Too Soon
Google announced that it achieved the first practical collision attack against the SHA-1 function. SHA-1 support is now mostly dropped from browsers due to Google’s aggressive efforts to deprecate it over the past few years. However, the company has received significant criticism for trying to deprecate SHA-1 too early.
Criticism Against SHA-1 Deprecation
In the fall of 2014, Google announced that it was going to drop support for SHA-1 because collision attacks against it were getting too affordable. The function was actually deprecated back in 2011 by the National Institute of Standards and Technology (NIST), which sets cryptography standards that are to be used in the U.S. government.
A year later, Jesse Walk, who was working for Intel at the time, did the math on how much it would cost to break SHA-1. According to his calculations, at that point in time, it would’ve cost $2.77 million, a sum that would’ve dropped to a mere $173,000 by 2018. This seemed like a sum that would not only be considered quite affordable by multiple intelligence agencies, but also by criminal organizations.
At the time, security expert Bruce Schneier also suggested that it may be time to start moving away from SHA-1. However, when Google announced that, starting January, 2016, it would consider SHA-1 certificates insecure, the certificate authorities weren’t too happy with it. At the time, Windows XP still had quite a few percentage points of market share left, and the operating system didn’t support the next-generation SHA-2 function. That meant that encrypted sites using SHA-2 certificates wouldn’t work at all on Windows XP.
Some certificate authorities even went through the trouble of continuing to serve SHA-1 certificates to web developers in 2016, something most browser vendors do not allow anymore. Eventually, this prompted some penalties from both Google and Mozilla, as the respective CAs didn’t abide by the two browser vendors’ policies.
There was also some pushback from Facebook, Twitter, and Cloudflare, which thought that the timeline for the SHA-1 deprecation was too aggressive, and that it needed to happen more slowly. However, Google showed today that if anything, the timeline was at best right on time, or potentially not aggressive enough.
Only the last versions of Chrome (v56) and Firefox (v51) stopped completely supporting SHA-1. Microsoft has delayed the full deprecation of SHA-1 in Edge and Internet Explorer 11 until mid-2017, but now that an SHA-1 collision attack was shown to be possible, it may drop the support earlier.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Breaking SHA-1
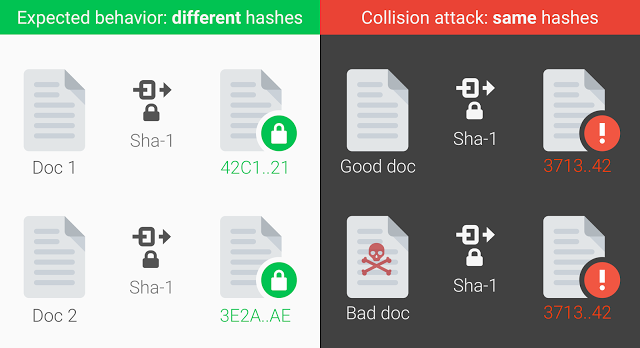
Ten years after the SHA-1 hash function was introduced, Google announced a technique for generating a practical collision. A hash collision occurs when two documents become represented by exactly the same cryptographic number or digest (as shown in the image above).
The collision allows an attack to intercept a connection and replace a good file with a malicious one, even if the hash of the two files is verified (as the verification would show the cryptographic number to be the same).
Google said that normally a collision attack wouldn’t be possible against a secure hash function, but SHA-1 has some flaws that allow an attack to exploit them, given enough computation power. Although the necessary computation power used to cost millions of dollars for a single collision only a few years ago, we’ve gotten to the point where it costs only about $110,000, according to the researchers that created the first practical collision.
The attacks will only continue to become cheaper, which is why it’s good that now most of the popular browsers have stopped supporting SHA-1. The rest will soon follow suit. To speed up the process, 90 days from now Google will also release code that will allow anyone to create such a collision against a pair of PDF files.
The idea is that attackers either already possess such tools or will soon. Google is just going to make it more obvious that browser and software vendors can’t obscure the need to drop SHA-1 support for much longer.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Sakkura Google have almost been too patient about retiring this broken old piece of 90s tech. The article describes SHA-2 as "next-gen," but it was released in 2001. It's ancient, it's unbelievable that anyone was wanting to hold on to something even more ancient in 2016.Reply
SHA-3 is the truly next-gen algorithm, and it was released in 2015. Companies should be actively working on adding support for that, so we don't run into the same issue in 5-10 years when SHA-2 might need to be retired. -
alextheblue There they go with the arbitrary 90 days again. Not 120 days, not 5 months. 90 days and boom, every website better have SHA-1 replaced with SHA-2. Google has spoken!Reply -
derekullo 1. Thou Shall not be EvilReply
2. Thou Shall not use Sha-1
3. Thou Shall not speak of Yahoo