Google Enhances Gmail With New Security Features
Google announced a new collaboration with other major companies, including Microsoft, Yahoo and Comcast, to implement a new protocol that would ensure all email remains encrypted in transit. Google also introduced a new page in its Safe Browsing system that will encourage those under attack by governments to increase their security by using SMS-based two-factor authentication or a physical Security Key.
Earlier this year, Google introduced some notifications in Gmail that would alert users before they would send their email to another address that doesn’t use encryption. According to Google, this has had the effect of increasing the amount of email sent over encrypted connections by 25 percent.
However, Google also found out from the recent research it has done with the Universities of Michigan and Illinois that attackers could still tamper with email encryption. That’s why it collaborated with Microsoft, Yahoo, and Comcast to create the SMTP Strict Transport Security standard to ensure that email travels only through encrypted channels. Any issues with the encryption would also be reported so that the companies can better understand where the attacks are happening.
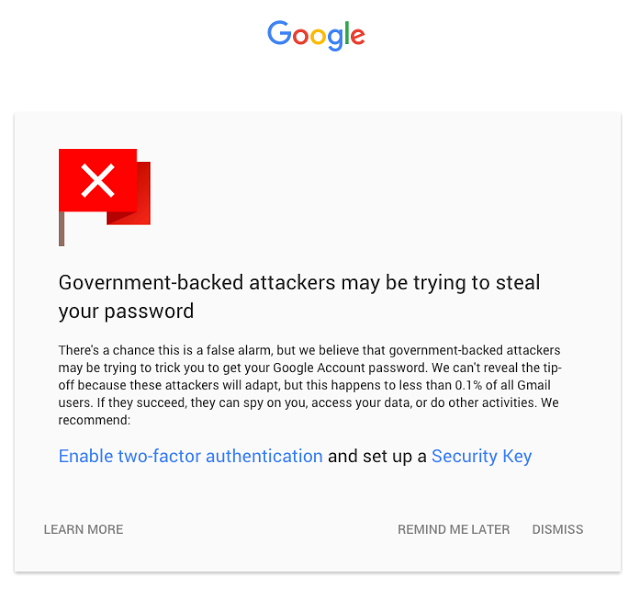
Since 2012, Google has begun warning Gmail users of state-sponsored attacks. According to the company, only 0.1 percent of its users have been the targets of such attacks, although considering Gmail has hundreds of millions of users, that’s still hundreds of thousands of attacked users. The targets typically include activists, journalists and policy-makers.
For those that are targeted by state-sponsored attackers, Google launched a new warning page that also acts as an instructions page for how to increase their own security. The users can enable SMS-based two-factor authentication or a FIDO U2F-enabled Security Key.
Although these new security features should help email encryption become stronger, the state-of-the-art remains end-to-end encryption, such as the one employed by PGP-based tools. Ultimately, most of these companies working on the new email encryption protocol rely on revenue from advertising, which implies data mining their users’ email contents.
That’s why it's in direct conflict with end-to-end encryption, because only the users communicating with each other could see the email contents. Google was supposed to also work on the End-To-End encryption browser plugin, but so far progress has been rather slow on that front. Even if it’s eventually finished, it likely won’t be used or promoted as a default solution for most Gmail users.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
ZeusGamer Wow, the government really won't stop until they have every account that you've got huh?Reply -
dstarr3 If a website or service offers two-factor authentication, I can't fathom why you would not activate it.Reply -
xvegan Is this the same google who was working with government entities to overthrow Assad in Syria? Oh boy do I really trust them.Reply -
DotNetMaster777 HTTPS websites can be open! for instance using DROWN attack .... so if there is used man-in-the-middle + DROWN .... probably, hackers can read everything ???Reply -
Solandri Reply
Because some of them require you to use their own proprietary two-factor app, rather than a generic one like Authy or Google Authenticator.17712012 said:If a website or service offers two-factor authentication, I can't fathom why you would not activate it.
Looking through my password library, I have a dozen financial and government accounts, five credit card accounts, about 20 shopping accounts, and about 40 membership type accounts (Netflix, UPS, my web host, etc). If every single one of them insisted I use their proprietary two-factor app, it would be insane. So I boycott the sites which won't let me use an app like Authy. -
Haravikk Anyone worried about security really needs to get themselves a digital certificate capable of being used for e-mail encrypting and signing, you don't even really need to get one from a certificate authority, self-signed will do. All you need to do is then give the public part of the certificate to everyone you know so they can install it and begin sending encrypted messages to you; get them to create a certificate of their own and do the same and you can send end-to-end encrypted messages in both directions.Reply
All modern mail clients support S/MIME and signing automatically, so once you've installed each other's certificates it's pretty painless, though you may need to renew them every now and then.
What we really need are more tools to make this easier. None of the mail clients bundled with an operating system seem to have tools for generating encryption/signing certificates built in which is a pretty big omission and makes things more difficult. It would even make sense if there were a way to persistently advertise the public key for an address; while this would let anyone send you encrypted messages, it wouldn't be likely to be used by spammers as they would need to individually encrypt every message that they currently indiscriminately send out in bulk. -
newbcakes Keep in mind Google makes money from advertising. 2-factor auth requires you give them more information (which they can sell). While I'll agree that it's more secure, you must also keep in mind that the more information you give them the more it serves their agenda. It also puts your information in the hands of numerous others, from whom you're trying to protect that data, right?Reply -
Haravikk Two-factor authentication on its own doesn't require any sensitive information, as you can use the Google Authenticator app (or load the same key into Authy, which is available for more platforms as a Chrome app). The same seems to be true of these security keys; while you can use SMS if you like, there are other options.Reply -
dstarr3 Reply17713794 said:
Because some of them require you to use their own proprietary two-factor app, rather than a generic one like Authy or Google Authenticator.17712012 said:If a website or service offers two-factor authentication, I can't fathom why you would not activate it.
Looking through my password library, I have a dozen financial and government accounts, five credit card accounts, about 20 shopping accounts, and about 40 membership type accounts (Netflix, UPS, my web host, etc). If every single one of them insisted I use their proprietary two-factor app, it would be insane. So I boycott the sites which won't let me use an app like Authy.
True. Let me add an asterisk to my statement clarifying that it shouldn't require a proprietary app.