Let’s Encrypt Has Issued 1 Million Certificates And Counting (Update: Exits Beta)
Update, 4/12/16, 10:15am PT: Let's Encrypt got out of beta after issuing more than 1.7 million certificates that are protecting more than 3.8 million websites. The non-profit group behind the Let's Encrypt Certificate Authority said that it has gained "tremendous operational experience and confidence" in its systems, so the beta label wasn't necessary anymore.
The group, which includes non-profit organizations such as EFF and Mozilla as members, as well as companies such as Cisco, Akamai, and OVH.com, recently added Gemalto as a Gold sponsor and HP Enterprise, Fastly, Duda, and ReliableSite.net as Silver sponsors. Cisco and Akamai also extended their platinum membership to another three years.
Let's Encrypt hopes to play a major role in encrypting 100% of the web, and so far it has received strong support from the industry and from web developers looking to encrypt their websites.
Original article:
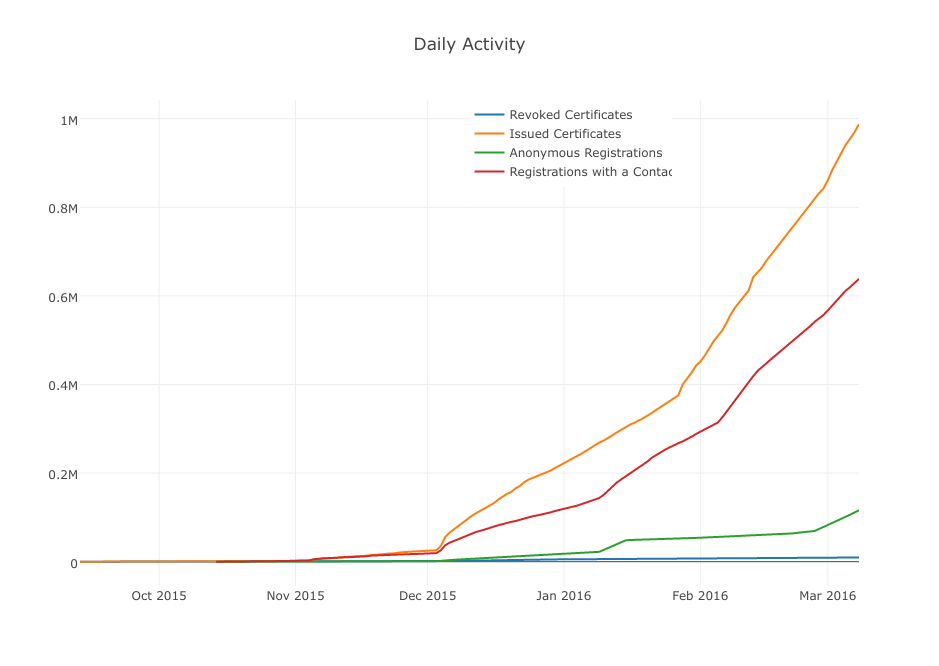
Let’s Encrypt issued certificate number 1 million since it launched as a public beta service about three months ago. Because one certificate can cover multiple domain names, the number of encrypted domains that used Let’s Encrypt certificates is actually 2.5 million.
The EFF, which is one of the founding members of Let’s Encrypt, said that 90 percent of these domains had previously never used HTTPS encryption. That means Let’s Encrypt’s free certificate service has had a major impact in getting web developers to encrypt their websites.
Those developers may have not adopted HTTPS encryption so quickly otherwise, due to the relatively high cost and difficulty of installing the certificate. Let’s Encrypt is completely free, easy to install, and can be auto-renewed every three months.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
“It is clear that the cost and bureaucracy of obtaining certificates was forcing many websites to continue with the insecure HTTP protocol, long after we've known that HTTPS needs to be the default. We're very proud to be seeing that change, and helping to create a future in which newly provisioned websites are automatically secure and encrypted,” said the EFF in a recent announcement.
Although Let’s Encrypt has played a big role in making the transition to HTTPS from the insecure HTTP protocol easy, there have been other factors that made the recent high adoption of HTTPS possible.
The Chrome and Firefox browsers also played their part when their respective teams announced that many features that worked over HTTP would soon be deprecated, pushing developers to adopt HTTPS.
The arrival of the HTTPS/2 standard, thanks to Google and the IETF, and the improvement in hardware and Internet connectivity performance over the past few years also meant that HTTPS encryption didn’t have a prohibitive overhead in terms of CPU and bandwidth usage anymore.
Google was also the first search engine to give a boost to HTTPS websites, encouraging web developers yet again to encrypt their websites. All of these, and more, created some sort of perfect storm that made it so web developers had no excuse not to adopt HTTPS anymore.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
AthanSpod And don't forget that you can use LetsEncrypt certificates for securing SMTP, IMAP and POP3 servers as well, just not as *client* authentication. So in theory it should boost the adoption of email being encrypted end to end on the network.Reply -
AthanSpod To be 100% clear on that, the "not client authentication" means they can't replace client passwords for logins, nor can they be used to directly encrypt/sign emails on a client. But they can be used for securing the client<>server part of IMAP and POP3.Reply -
AthanSpod To be 100% clear on that, the "not client authentication" means they can't replace client passwords for logins, nor can they be used to directly encrypt/sign emails on a client. But they can be used for securing the client<>server part of IMAP and POP3.Reply -
falchard Watchout, you are giving the government ideas. Now that they know certificates has been a roadblock to encryption, they will make a Department of Web certification.Reply -
hellwig Do these certificates require a static IP? If not, when did that change? I might have to talk to my webhost about this.Reply -
Haravikk ReplyTo be 100% clear on that, the "not client authentication" means they can't replace client passwords for logins, nor can they be used to directly encrypt/sign emails on a client. But they can be used for securing the client<>server part of IMAP and POP3.
You don't really need a third-party certificate authority for issuing client certificates anyway; you can create your own certificate authority for this purpose using openssl, which also then allows you to easily automate the process of issuing certificates for new users, all you have to do is bundle your root and intermediate certificates (not keys) along with the user's certificate and key and have them install the whole lot together.
There's not much more a third party certificate can do that that kind of setup won't, as a user having a client certificate is how you validate who they are. That said I personally don't like swapping password for client certificates, I prefer to use both together for the added security, but there are other options such as certificate + multi factor authentication.
Anyway, that's a bit of an aside; I'm using Let's Encrypt for my domains, though I'm currently having to issue some individual certificates for sub-domains due to the way that they're created, which I'll have to try to sort out at some point. It's possible other users are doing the same, and it's unclear if that 1 million metric includes renewals, since the recommendation for Let's Encrypt is to renew every month (well short of the 90 day expiration time). -
sylentz199 I like the anonymous and no contact provided registrations...Reply
About to get lots of really believable Banking Phishing emails -
sam1275tom Now a noob question: can I use it to make a certificate for my openWRT router for free, thus avoid the "self-signed insecure" warning when I visit the router management page?Reply