Netflix Adopts Efficient HTTPS Encryption For Its Video Streams
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Netflix announced that it has implemented efficient HTTPS encryption for its video streams. To this point, the company has used only HTTPS to protect user information.
Netflix has been reluctant to adopt HTTPS for its video streams so far because delivering video is already a bandwidth-heavy task, and adding encryption on top of that risked adding too much overhead. To solve this problem, the company searched for the ideal cipher and its fastest implementation.
Cipher Evaluation
Netflix eventually chose the the Advanced Encryption Standard (AES) cipher in Galois/Counter Mode (GCM), which is available only in TLS 1.2 and later. The company chose GCM over the Cipher Block Chaining (CBC) method because it can encrypt and authenticate the message simultaneously, whereas AES-CBC requires an additional pass over the data to generate keyed-hash message authentication code (HMAC). The latter can still be used as fallback for older browsers and client software that don’t support TLS 1.2. However, it shouldn’t be too long until virtually all Netflix users can play video streams over TLS 1.2 or later.
The company also tested which were the fastest implementations of AES-GCM in various TLS libraries such as OpenSSL, Google’s BoringSSL, and Intel’s Intelligent Storage Acceleration Library (ISA-L). The implementations had to work best with AES-NI, the instruction set for Intel and AMD processors that significantly accelerates encryption and decryption.
Other Optimizations
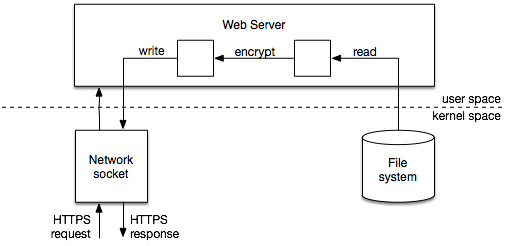
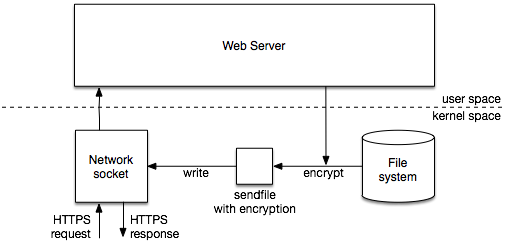
Netflix and the team behind the Nginx server software collaborated to improve how fast the data is sent from the server storage to users’ video players. However, the method Netflix has been using to improve the performance for that task wasn’t compatible with TLS encryption.
The company was able to fix this issue by creating a hybrid TLS scheme where the data is encrypted in kernel space while the session management remains in user space.
Results
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Netflix then tested the BoringSSL and ISA-L AES-GCM implementations and compared them with a baseline OpenSSL implementation. Both managed to increase the performance over the baseline OpenSSL implementation by 30%. Ultimately, Netflix chose the ISA-L library for slightly better performance than BoringSSL. The company is now optimistic that it can add HTTPS encryption to all of its streaming clients without suffering too much of a performance hit compared to the unencrypted versions.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
adgjlsfhk I kind of appreciate it. Tom's has become my default goto for airport public wifi because everywhere else now protects against redirects.Reply -
gggplaya In the end, this only protects Netflix's bottom line, does nothing to help the end consumer. In fact, probably makes performance worse on your machine because your CPU has to decrypt and bandwidth suffers a little more.Reply -
bloodroses Reply18406319 said:They should've switched to Pied Piper.
But then the interface would be confusing to all users but engineers. :) -
targetdrone Why exactly does Netflix or YouTube need to encrypt video streams?Reply
a Star Trek The Next Generation episode and videos of cute kittens isn't exactly top secret emails regarding weapon shipments to groups hostile to the United States. -
spdragoo Because of the customer account information?Reply
You can't access Netflix unless you're logged in...& if you're logged in, then you have access to your billing account information. Encryption is good because it helps protect your information. -
targetdrone Reply18410427 said:Because of the customer account information?
You can't access Netflix unless you're logged in...& if you're logged in, then you have access to your billing account information. Encryption is good because it helps protect your information.
The article states that information is already protected. So again why does the video itself need encryption?
-
spdragoo Probably for DRM-related issues. The BBC just made a big deal about warning everyone in the UK that they were sending "packet-sniffer" vans around to identify those people watching BBC programming over the Internet, instead of watching it on a TV (note that in the UK, everyone who watches the BBC is supposed to pay an annual tax per TV set (145 pounds for color, IIRC) for the "privilege" of watching BBC shows live), & they were claiming that the packet-sniffing tech they were using could identify data indicating that BBC shows were being watched, even if the Wi-Fi signal being used was encrypted. They apparently feel that whatever the cost is for those vans, it'll be worth it to recoup it from the fines (1000 pounds & a criminal record per instance).Reply
If that's 100% true (as opposed to just a scare tactic to get everyone to pay their fees), it's not really a stretch for the tech to exist to use packet-sniffers to strip out streaming video data from the data stream & recombine it into a file on another system.
As another possibility, it could be used to prevent the use of 3rd-party "stripping" software, like the apps that claim they can let you download YouTube videos straight from the website. I would imagine it's much easier to do so through an unencrypted website than one using encryption.