Netgear Acknowledges Critical Vulnerability In Multiple Routers
Netgear acknowledged a critical vulnerability that allows its routers to be taken over with nothing more than a malicious website or advertisement. Anyone exploiting this security flaw could use affected routers as their own personal botnet, effectively turning Netgear's products into a dormant army that need only be roused and given its marching orders, which could include taking down popular websites and online services with a flood of traffic.
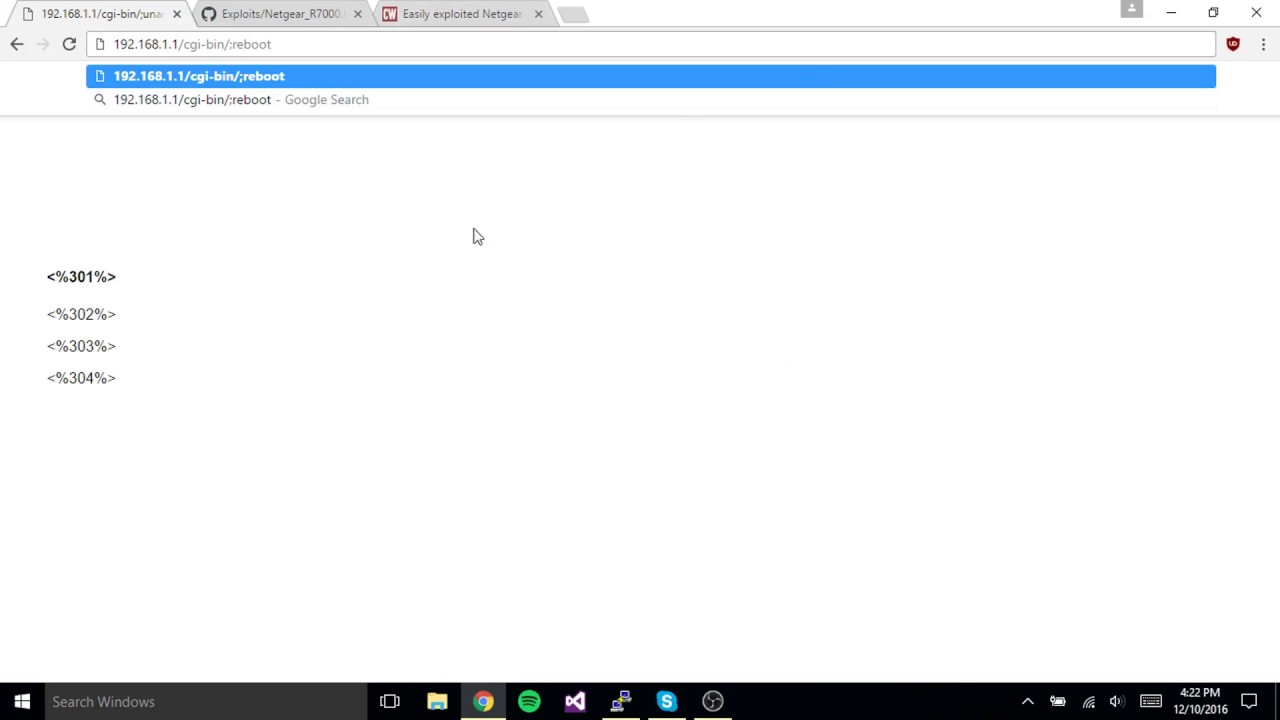
The issue affects Netgear R7000 and R6400 routers. It might also be present in other products--Netgear said the security flaw could affect R8000 and other models, and it plans to investigate the matter to determine the full extent of the vulnerability. CERT, which informed the public about the problem, advised consumers "who have the option of doing so" to "strongly consider discontinuing use of affected devices until a fix is made available."
The vulnerability was discovered by "Acew0rm" on Twitter, who revealed the problem on December 8. Netgear head of digital strategy and innovation Chris Salazar acknowledged the problem on the night of December 11. The support article informing Netgear customers about the issue was published December 12--four days after Acew0rm went public and two days after they published a video about the exploit, which you can watch below:
Netgear said in its support article that it "has recently become aware of the security issue." But according to Acew0rm, the company was informed about the vulnerability on August 25, which means it had almost four months to fix the problem before the exploit was made available to anyone else. Many responsible disclosure policies allow researchers to share information after 30 to 90 days; Acew0rm waited even longer than that before going public.
Routers aren't new to security flaws. D-Link had to fix a backdoor in 2013 to make sure its products' settings couldn't be remotely changed; the F-Secure security company released a free tool in 2015 so people could scan their routers for any problems. Experts have called on the FCC to require manufacturers to make router firmware open source and vow to release patches for known vulnerabilities in a timelier manner.
Yet many of these products still use old firmware and companies rarely update them to improve their security. Routers are much like Internet of Things (IoT) devices in that regard--people only care about them when they're working, and manufacturers only care about them when they need to sell more. As critical as these devices are, and despite the threat they pose if they're used to attack online services, they simply aren't top-of-mind for many people.
These sleeping armies are being awoken, however, so it's time for companies and consumers alike to start taking them seriously. Netgear did not provide a time frame for any firmware updates to address this vulnerability. Here's what the company said in its support article for its customers:
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
NETGEAR is investigating and will update this article once we have more information.We appreciate and value having security concerns brought to our attention. NETGEAR constantly monitors for both known and unknown threats. Being pro-active rather than re-active to emerging security issues is fundamental for product support at NETGEAR.
Waiting four months to acknowledge a security vulnerability is hardly reactive, and it certainly isn't proactive. Let's just hope that Netgear responds faster to the issue now that it's been made public. In the meantime, if you use one of the Netgear models affected by this vulnerability, it's probably time to start looking for a new router. Better to be safe than to risk unwittingly contributing to future attacks on some of your favorite websites.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
Sorbert Got the nighthawk x6 but don't have the cash at moment to get a new Xmas and all hope fixed sooner then laterReply -
BoredSysAdmin Not first time Netgear had a MASSIVE issue with their software, but because in was in their not very popular UTM product, not many noticed.Reply
In short - on each reboot it replaced VPN's IPSEC Shared key with 49 asterisks. -
firefoxx04 Those with Tomato should be fine unless their is a vulnerability in Tomato, but I doubt its the same.Reply -
spidder unless you are running the stock firmware this will not affect you. (tomato, ddwrt and openwrt users don't need to worry)Reply -
gggplaya The factory netgear firmware sucks, it was so unstable. When loaded up with a few streams of netflix and a network backup, the router would freeze and i would have to reboot it manually by unplugging it. Holidays were a nightmare with all the family over. Literally 10 times a day, it would need a reboot.Reply
So i switched to DDWRT last year and it's been very stable. Never crashes and just simply works.