NSA, Microsoft Issue Critical Cyberthreat Report to US Infrastructures Backed by Chinese State-Sponsored Actor
Exposing the organized cybercriminal group "Volt Typhoon".

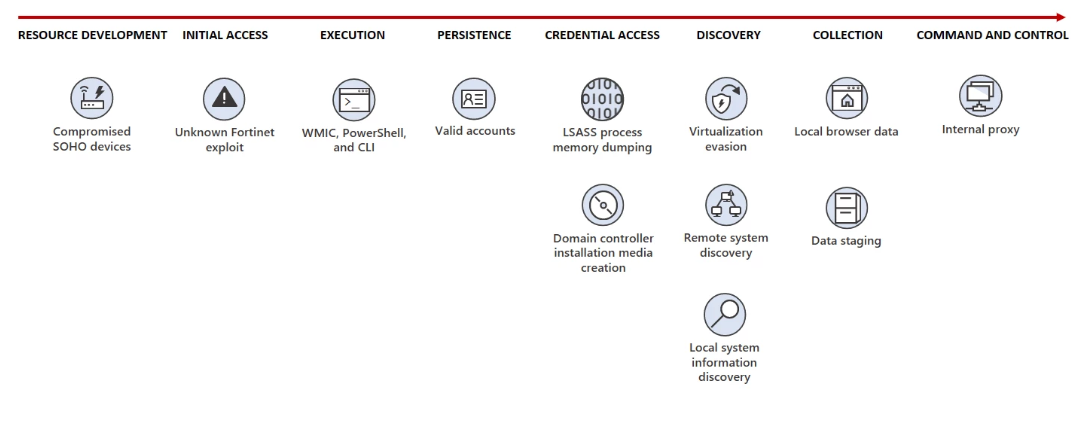
The United States through its National Security Agency (NSA) and Cibersecurity & Infrastructure Security Agency (CISA), Microsoft, and others have issued a joint Cybersecurity Advisory (CSA) intelligence bulletin singling out the US-based activities of Volt Typhoon, an organized, state-sponsored cybercriminal group operating out of China. The report outlines operations conducted on US soil towards infiltrating and compromising critical infrastructure in a number of fields. It further details how individuals tied to this group operated undetected on US soil: by deploying living-off-the-land (meaning isolated and self-sufficient cells) and hands-on-keyboard (operating entirely online) techniques.
According to Microsoft, it can say with moderate confidence that the group's campaign aimed to pursue "the development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises."
Volt Typhoon activities in the US date back to at least mid-2021, targeting multiple organizations spanning a multitude of economic areas. Communications, Manufacturing, Utility, Transportation, Construction, Maritime, Government, Information Technology, and Education sectors.
Digitization (the act of bringing digital capabilities to otherwise analog tasks) is a fact of our lives, as is its galloping increase - every year, new products appear that have added digital functionality. Since this functionality is usually worth the added investment (due to cost reduction, efficiency gains, practicality, or any other metric the market wills), both the analog and disconnected tools are slowly phased out until relegated towards oblivion or a niche. You'd be surprised at how much communications infrastructure is already reliant on digital systems.
Of course, the issue with digital systems is that they can be remotely hacked.
In a more tangible example, we look to when Microsoft helped Ukraine defuse Russian malware installed in the country's tram infrastructure. The system had been infected with Wiper-type malware - able to delete entire systems or the crucial files needed for something such as the train control system inoperable. This happened before the war. After the invasion, that same train system evacuated a number of Ukrainian war refugees.
The issue here is that digitization means increased opportunity for remote access, which in turn increases the likelihood of attack (Russia spends less resources by digitally disabling a Ukrainian drone, for instance, than by firing a rocket at it). Even as our lives become more efficient, technological, and interconnected, more and more of its facets become vulnerable to what's the least costly and most efficient type of attacks: the cyberattack.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Besides wanting to increase insulation from and military effectiveness in the event of conflict with the US, part of the reason for targeting American-Asian communications is called Taiwan. We've seen enough evidence of the tug-of-war between the US and China for the technological crown-jewel that is the Taiwan Semiconductor Manufacturing Company Limited (TSMC). Sometimes, being the most desired "object" in the room is simply not the best place to be.

Francisco Pires is a freelance news writer for Tom's Hardware with a soft side for quantum computing.
-
This group is still active ? I thought they went silent since last year or so. A very clever and dangerous cyber criminal group btw. They might have already compromised few things by now.Reply
They also used custom versions of open-source tools like 'Impacket' and 'Fast Reverse Proxy (FRP)', to establish a command and control (C2) channel over proxy to further stay under the radar for several years.
Who knows that this group still proxies all its network traffic to its targets through compromised SOHO network edge devices (including routers, firewalls, and VPN hardware). Very intelligent indeed. -
TechieTwo As noted in the joint announcement many of the routers are consumer based which makes them easy to hack and use for nefarious operations. The best option for many is a more secure router.Reply
"Volt Typhoon proxies all its network traffic to its targets through compromised SOHO network edge devices (including routers). Microsoft has confirmed that many of the devices, which include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel, allow the owner to expose HTTP or SSH management interfaces to the internet. Owners of network edge devices should ensure that management interfaces are not exposed to the public internet in order to reduce their attack surface. By proxying through these devices, Volt Typhoon enhances the stealth of their operations and lowers overhead costs for acquiring infrastructure." -
Yeah.Reply
Also, Microsoft suggests enforcing strong multi-factor authentication (MFA) policies, hardening LSASS processes, and running endpoint detection and response (EDR) in block mode to protect against such stealthy attacks.
They are one of the most "Stealthy" cyber crime groups operating online, in my opinion, since they also carefully deleted and wiped out the evidence and proof of intrusions from the victim's logs. A lot of human talent is actually being wasted on such clever and nefarious activities.
Some say using Passwordless sign-in, password expiration rules, and deactivating unused accounts can also help mitigate this attack/risk, but I doubt this is also going to work that easily.
Because this hacker group also uses the "Windows Management Instrumentation Command-line" and the ping command to discover other systems on the network, apart from the command-line tool Ntdsutil.exe, and also PowerShell.
MS and CISCO actually gave some code snippets as examples. One of these, show the commands used by Volt Typhoon when setting up and removing a port proxy on an infiltrated system.
-
More proxies were found last week, many unsuccessful to stop this group yet, at least for now. More compromised SOHO network edge devicesReply
-
digitalgriffin Reply
No one patches them that's why.Metal Messiah. said:More proxies were found last week, many unsuccessful to stop tis group yet, at least for now. More compromised SOHO network edge devices -
digitalgriffin Reply
*Hugs his pfSense box and bitdefender 2 box*Metal Messiah. said:This will keep on continuing till the internet is alive, hehe !