Leaked Nvidia Code-Signing Certificate Now Being Used by Malware
Two such certificates were part of the Nvidia hack attack haul we reported on last week.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Trouble is brewing in the fallout from the Nvidia hack attack, which we first reported on in late February. Two code-signing certificates were among the purported 1TB of data obtained, which compromised hardware schematics, firmware, drivers, employee information, and more. The significance of the certificates getting into any hackers' grubby hands is that threat actors can repurpose them to sign their (mal)wares, reports Bleeping Computer.
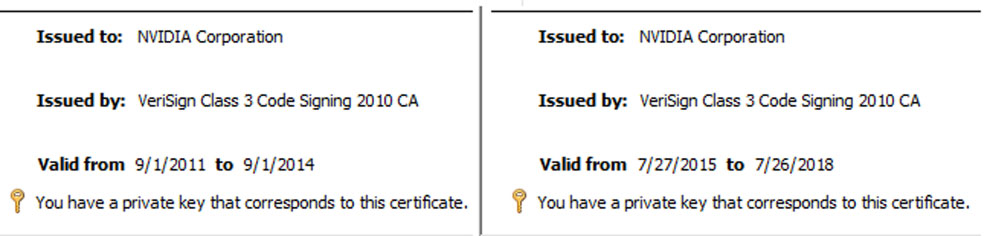
Just ahead of the weekend, computer security specialist Bill Demirkapi highlighted the two leaked Nvidia Corporation certificates, as issued by VeriSign. You can see from the screenshots above that one of them expired in 2014 and the other in 2018. Despite the certificates so clearly being expired, Demirkapi says that " Windows still allows them to be used for driver signing purposes."
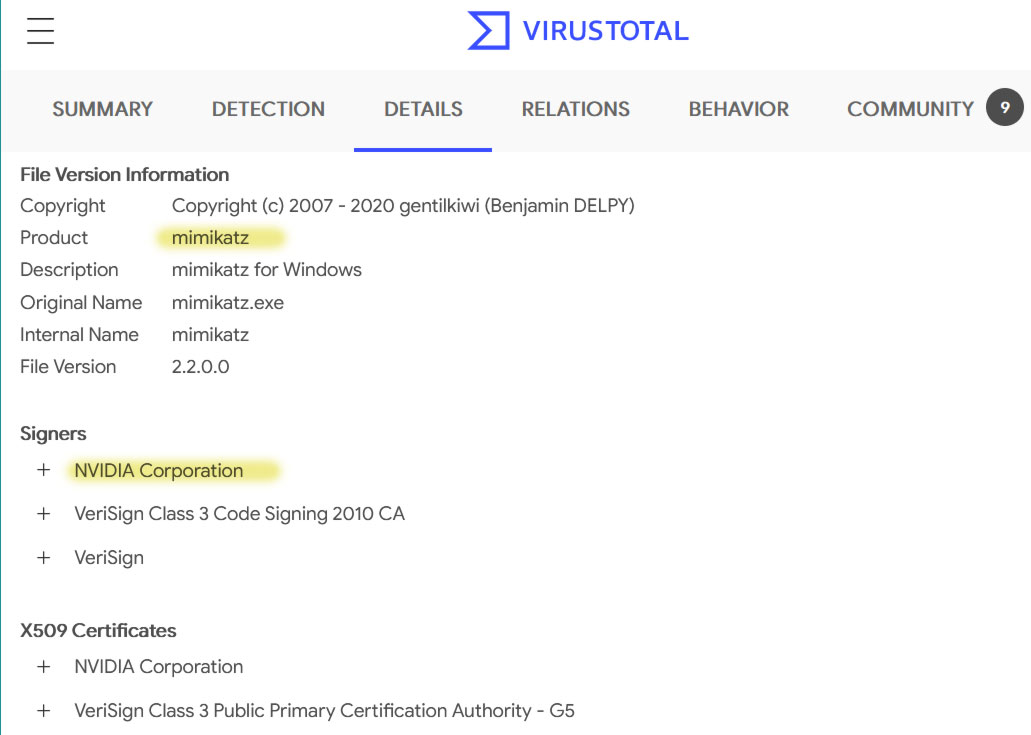
Proof of the danger from these certificates being made public came to light just a few hours later. Security researcher Florian Roth took to Twitter to provide links to malware spotted in the wild, signed as if they were genuine, unaltered Nvidia code. Of course, these weren't links to the malware, but rather to virus scanning databases reporting on their existence.
A long list of malware seems to have been seeded, now certified as genuine Nvidia code. Among the suspicious packages, many seem to be infected with Mimikatz, a program used to extract passwords, PINs, and similar from a computer's memory that falls victim to it.
Other common "Nvidia signed" malware in the online detection database listings were for KDU – a rootkit malware, and for cryptomining malware – software that will try and sneakily eat up your system's computing resources, given a chance.
Why Doesn't Windows Block the Installation of Apps With Expired Certificates?
New malware can now be digitally signed to "verify" that Nvidia was the file's developer and that a third party hasn't modified it. The certificate expiry dates don't particularly impede malware writers' deceit because Windows will accept them on some occasions.
Interestingly, the certificate that expired in 2014 is the most problematic leak of the two. This was the one used by all the malware spotted in the wild, due to a loophole. In 2015, Microsoft purposely allowed pre-July 29, 2015 certificated drivers to run for the sake of backward compatibility with old devices.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Computer administrators can block code signed by the rogue certificates from running on machines using Windows Defender Application Control policies to control what Nvidia drivers can be loaded. However, this is an advanced configuration process, so it is hoped Microsoft will provide user updates to revoke the stolen certificates. However, such a sweeping action by Microsoft might block some older, legitimate Nvidia drivers from working on Windows 10 and 11.

Mark Tyson is a news editor at Tom's Hardware. He enjoys covering the full breadth of PC tech; from business and semiconductor design to products approaching the edge of reason.
-
digitalgriffin I called it.Reply
Time for Microsoft to update revoked certs in their security update. -
InvalidError People should have the ability to install stuff with expired certificates, just have a warning popup informing that the certificate is expired or revoked to let the user know to be extra careful about the stuff's origin and that the certificate makes sense for what they downloaded.Reply -
digitalgriffin ReplyInvalidError said:People should have the ability to install stuff with expired certificates, just have a warning popup informing that the certificate is expired or revoked to let the user know to be extra careful about the stuff's origin and that the certificate makes sense for what they downloaded.
I more than fully agree. But there are few people who are tech savvy as us who are likely looking for an outdated driver on a cheap GPU because they can't afford anything else. So do we protect the non-tech savvy, or provide assistance to outdated hardware? I've seen more than one post here where people ask for support for their old hardware. (Usually India, Far East, or East European) -
InvalidError Reply
Make the "expired certificate" window scary enough to scare most normal people into doing their due diligence before going through with the install and you can accommodate most of both kinds of users. The only ones left are the ones who have no clue what they are doing and will fall for just about anything anyway who are never going to be remotely safe no matter how hard you try.digitalgriffin said:So do we protect the non-tech savvy, or provide assistance to outdated hardware?