Plundervolt: New Attack Targets Intel's Overclocking Mechanisms (Updated)
Tweaking the voltage spills the secrets

Update: Intel sent us clarification that the fix for this vulnerability does require locking the voltage in the BIOS. If SGX has not been enabled, or if the CPU voltage is locked at the default values via the mitigation, the system is not vulnerable.
Original Article:
There's no doubt that enthusiasts the world over appreciate the ability to alter Intel's CPU voltages and frequency from within the operating system, allowing them to use software-based utilities for overclocking, but it turns out that nefarious actors may also appreciate the feature.
According to news first outlined by ZDNet today, the new Plundervolt vulnerability targets those same voltage- and frequency-adjusting mechanisms within Intel's chips to enable malicious actors to extract information from what Intel says is one of the safest areas on its chip: The SGX enclave.
Intel uses this protected area of the chip to secure the most valuable information, like AES encryption keys. This enclave is not only physically separate from other memory inside the CPU, it is also protected via software encryption, making it especially difficult to attack, though it certainly isn't without precedent.
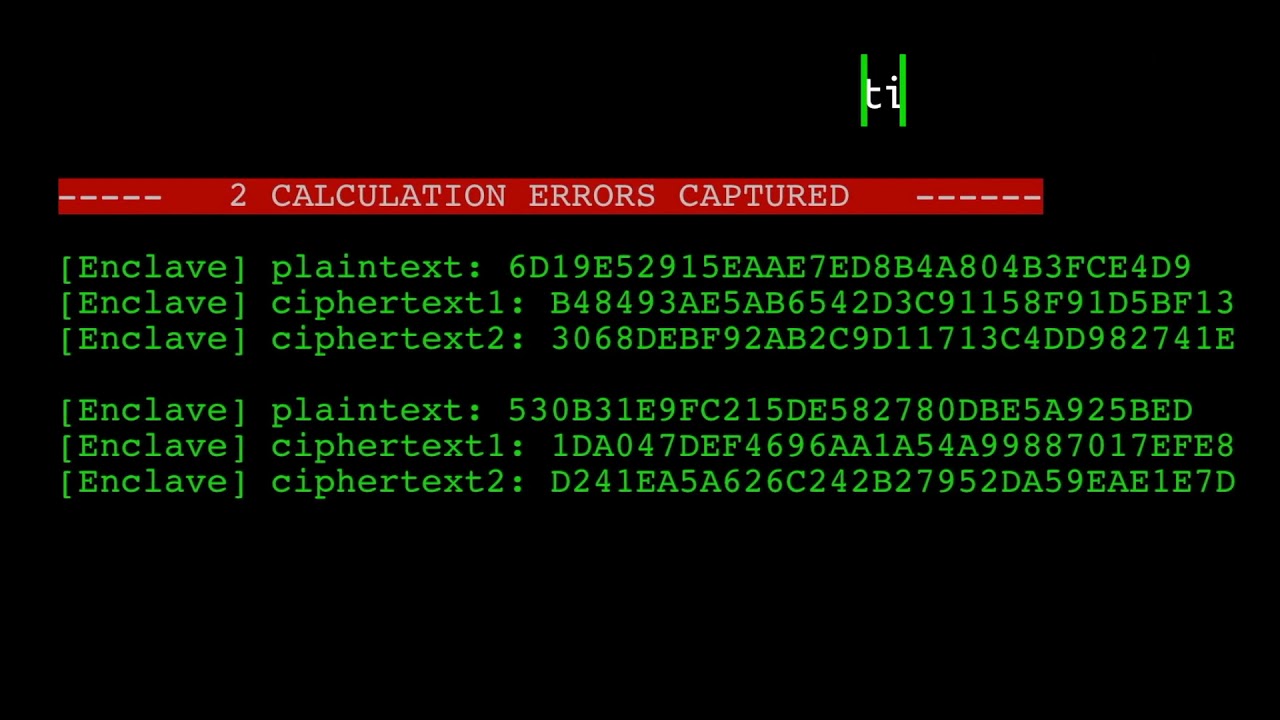
In fact, Plundervolt allows attackers to extract information from the enclave faster than is possible with other attacks, like Meltdown or Spectre, among others.
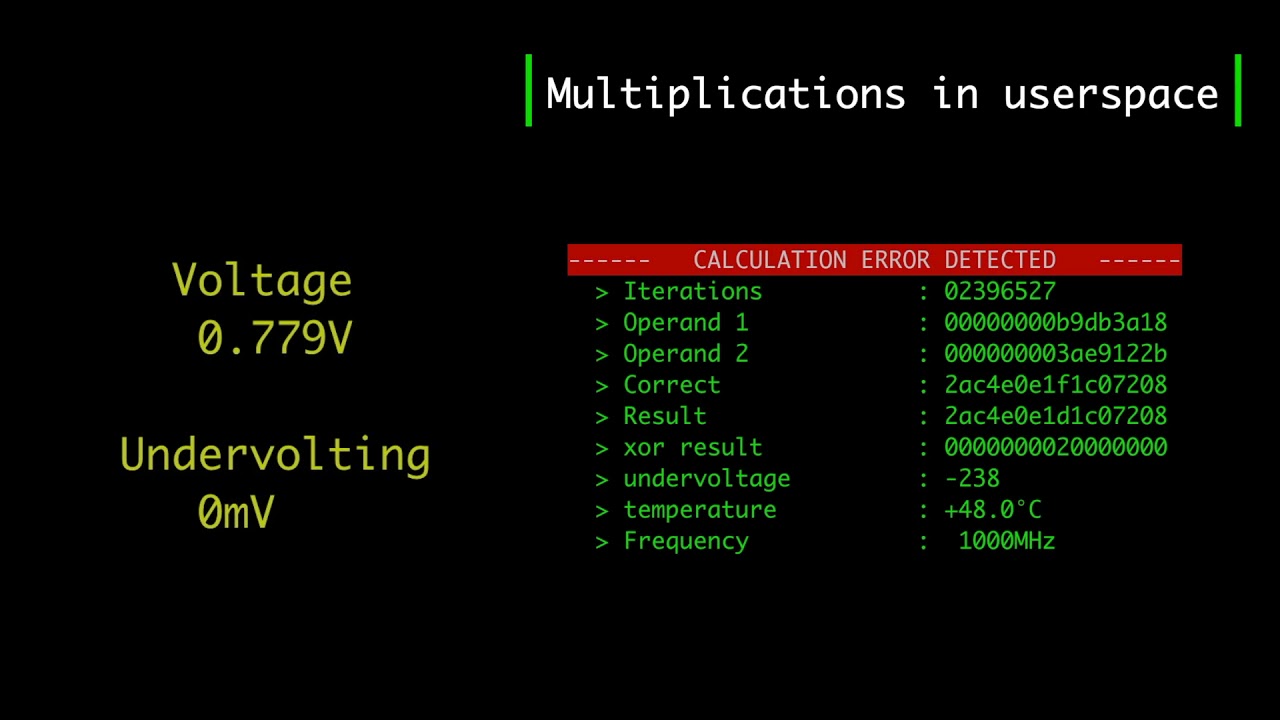
The attack works by altering the voltage and frequency of the chip (undervolting) to alter bits within SGX. That creates errors that can later be used to recreate data by using side-channel observation techniques. The attack uses the fundamental concepts behind both the VoltJockey and CLKscrew attacks.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Intel issued microcode and BIOS updates today to mitigate the vulnerabilities, but we haven't yet learned if Plundervolt mitigations will have an impact on performance like we've seen with other patches. We do know that the mitigation involves deactivating voltage and frequency adjustments from within the operating system, meaning that capability is removed from software-based overclocking utilities. Yes, your software-based overclocking tools will likely not work after the patch. This means that Intel's own XTU software, among many other third-party utilities, will not work, so software-based overclocking, or undervolting for laptops, will no longer work if you intend to use the SGX feature.
As we've seen, microcode updates that are delivered via the Windows 10 operating system are the best option for most users, as motherboard vendors tend to not offer newer BIOS revisions on older Intel motherboards. Intel's advisory states to look for BIOS updates from your motherboard vendor, but you shouldn't hold your breath waiting for one if you have an older motherboard.
Intel's 6th, 7th, 8th, 9th, and 10th-Gen Core processors are all impacted by the vulnerability, along with Xeon E3, v5, v6, E-2100 and E-2200 families. The attack does require host access with root or administrative privileges, so it would be hard, but not impossible, to exploit remotely. Remote injection would require a combination of attacks to deliver the malicious Plundervolt-infused application. The publication also notes that the vulnerability isn't easy to exploit from within typical malware, meaning you would likely have to be specifically targeted.
Luckily for Intel, this time around the attack isn't possible in virtualized environments due to existing protection mechanisms, meaning Intel's data center customers are less likely to be exposed to the attack.
We'll update this post as we learn more. You can also find more information here.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
hotaru251 Replyfrom what Intel says is one of the safest areas on its chip
i mean at this point intel's chips and safe is a joke <_<
microcode and BIOS updates today to mitigate the vulnerabilities, but we haven't yet learned if Plundervolt mitigations will have an impact on performance like we've seen with other patches. We do know that the mitigation involves deactivating voltage and frequency adjustments from within the operating system, meaning that capability is removed from software-based overclocking utilities. Yes, your software-based overclocking tools will likely not work after the patch.
how long until there is no point in gettign a K series chip when its crippled to base speeds?
also how would this effect boost? Doesnt that need to access voltage changing? -
ngneer This is merely a configuration issue. How would a fix preventing undervolting cause performance degradation?Reply -
wexir i wonder if you could do something like that with amd cpus aswell, since ryzen master you can change overclock settings etc from windows too...Reply -
Chung Leong Replywexir said:i wonder if you could do something like that with amd cpus aswell, since ryzen master you can change overclock settings etc from windows too...
I'd imagine, given the vulnerability is due to a physical phenomenon. Hard to image a scenario though where you'd still need to obtain the encryption after gaining control of the hypervisor. The hypervisor could simply start the VM in debug mode then ask the CPU to decrypt any given memory area. -
hannibal These attacks get more clever all the time... soon They will use power cord and electricity usage to spy computers...Reply
All that it start to seem to be. It definitely is not easy to develop cpus these days... -
Pat Flynn Replywexir said:i wonder if you could do something like that with amd cpus aswell, since ryzen master you can change overclock settings etc from windows too...
Likely not at all as this attack goes after the Intel SGX. While AMD has a security 'chip' within its CPU's like the SGX, it's a whole different animal. It'd be like robbing a bank with the wrong blueprints. -
svan71 Replyhannibal said:These attacks get more clever all the time... soon They will use power cord and electricity usage to spy computers...
All that it start to seem to be. It definitely is not easy to develop cpus these days...
These days? the design is 11 years old gen 1 released Nov 2008.