Robot Steals RAM Data by Freezing Chips in Chilling Cybersecurity Demo

The field of cryo-mechanics has dipped into cybersecurity, as Ang Cui, a cybersecurity researcher and founder of cybersecurity firm Red Balloon Security, demonstrates in a new demo. The concept of stealing data from chips by freezing them isn’t new, but this cryo-mechanical robot has automated the process, increasing the efficiency and scope of such an attack.
Cui recently corresponded with The Register in an exclusive interview. In the discussion, he explained the process involves freezing the RAM, removing it from the device, and pressing it into a specially designed socket capable of duplicating the physical state at the time of pressing. This process is incredibly time-sensitive, making it difficult to pull off without developing a way to automate the procedure.
The cryo-mechanical robot is essentially a CNC machine. It’s connected to a custom reader designed with a field-programmable gate array (FPGA). It also uses an ESP32-based controller that’s operated using MicroPython. A few components were removed from the CNC machine, including its X-axis actuator and motors.
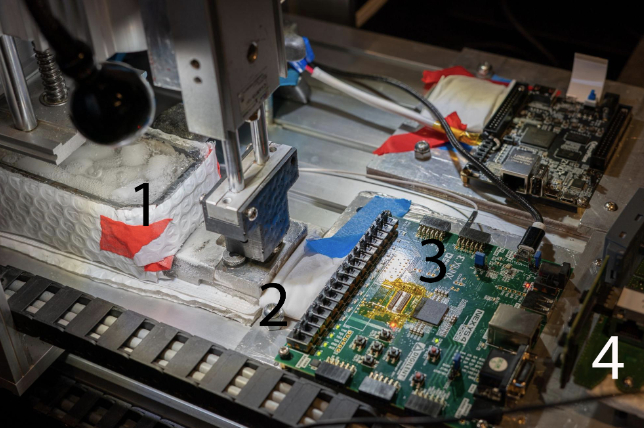
The data reader relies on what’s known as a conductive elastomer IC test socket. This is what the frozen chips are pressed into. Cui likens its consistency to hard gummy bears. A piston pushes the frozen chips into this socket without damaging the chips or the surrounding PCB. Once a copy is made, the data can be evaluated.
The new cryo-mechanical robot was successfully tested on a couple of devices, including a Siemens SIMATIC S7-1500 PLC, which revealed firmware binaries that had been encrypted. They also pulled runtime ARM TrustZone memory from DDR3 DRAM inside an 8800 series Cisco IP Phone.
Cui explains these types of attacks, known as cold boot attacks, can be thwarted using physical encryption—something found in modern gaming consoles like Xbox and PS5. However, most processors in everyday computers are not physically encrypted, making them vulnerable to this type of data extraction. To read more about this cryo-mechanical robot, check out Cui’s interview with The Register.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Ash Hill is a contributing writer for Tom's Hardware with a wealth of experience in the hobby electronics, 3D printing and PCs. She manages the Pi projects of the month and much of our daily Raspberry Pi reporting while also finding the best coupons and deals on all tech.
-
This link in your article I think is not working (page not found). Because it is a Forum link : The RegisterReply
This one is the original:
https://www.theregister.com/2023/06/09/cold_boot_ram_theft/ -
So according to the concept, they are bypassing manufacturer mitigations, by disabling Joint Test Action Group (JTAG) debugging interfaces and Universal Asynchronous Receiver/Transmitter (UART) circuitry, using encrypted firmware, and the use of ball grid array (BGA) packaging.Reply
-
bit_user Reply
Yeah, I think it's like just taking a hot DRAM chip, full of data, and swapping it from one host machine to another.Metal Messiah. said:So according to the concept, they are bypassing manufacturer mitigations, by disabling Joint Test Action Group (JTAG) debugging interfaces and Universal Asynchronous Receiver/Transmitter (UART) circuitry, using encrypted firmware, and the use of ball grid array (BGA) packaging.