New Malware Uses SSD Over-Provisioning to Bypass Security Measures
An almost perfect way to stealthily store malware
Korean researchers have detected a vulnerability in SSDs that allows malware to plant itself directly in an SSD's empty over-provisioning partition. As reported by BleepingComputer, this allows the malware to be nearly invincible to security countermeasures.
Over-provisioning is a feature included in all modern SSDs that improves the lifespan and performance of the SSD's built-in NAND storage. Over-provisioning in essentially just empty storage space. But, it gives the SSD a chance to ensure that data is evenly distributed between all the NAND cells by shuffling data to the over-provisioning pool when needed.
While this space is supposed to be inaccessible by the operating system -- and thus anti-virus tools -- this new malware can infiltrate it and use it as a base of operations.
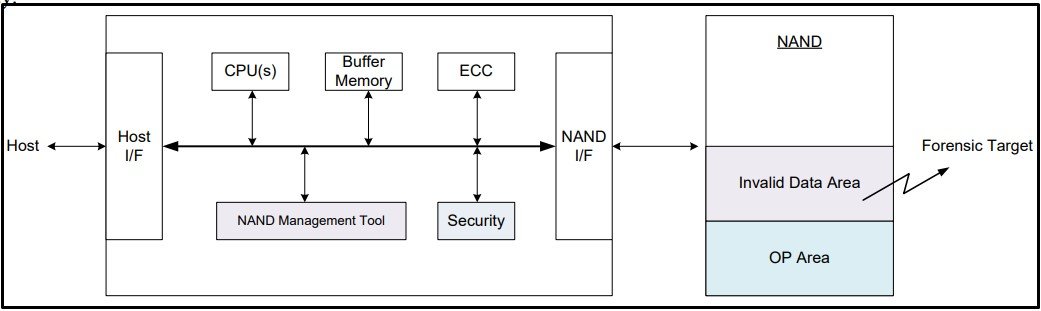
Korean researchers at the Korea University in Seoul modeled two attacks that utilize the over-provisioned space. The first one demonstrates a vulnerability that targets invalid data (data deleted in the OS but not physically wiped) within the SSD. To gain more potentially sensitive data, the attacker can choose to change the size of the over-provisioned data pool to provide additional empty space to the operating system. So when a user goes to delete more data, extra data remains physically intact within the SSD.
SSDs rarely physically delete data, unless it's absolutely necessary, to preserve resources.
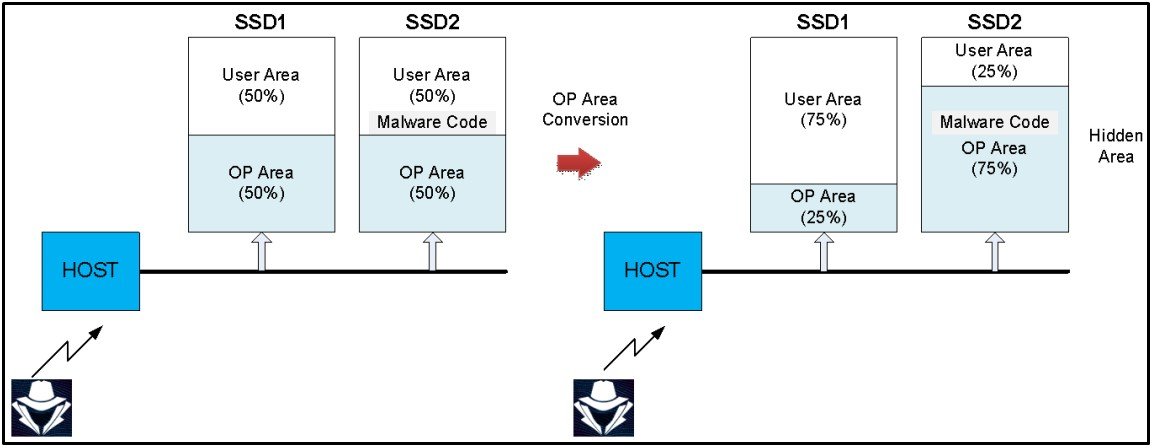
The second one is similar to what was discussed earlier, injecting firmware directly into the over-provisioning pool. In this example, two SSDs are connected as one device, and over-provisioning is set to 50%. When an attacker injects malware into the OP partition of the SSD, they reduce the first SSD's OP range to 25% of the SSD's total size, then increase the OP range of the second SSD to 75%.
This gives the attacker room on the 2nd SSD to inject malware directly into the OP partition while setting the first SSD's OP range to 25%, making it seem like the OP area on both drives has remained unaffected. This is because the OP range for both SSDs combined is still 50%.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The researchers suggest implementing a pseudo-erase algorithm that physically deletes data on an SSD without affecting real-world performance to counter the first attack model.
It is recommended to implement a new monitoring system that can closely watch the over-provisioned size of the SSDs in real-time to counter the second attack model. Plus, access to SSD management tools that can change over-provisioned sizes should have more robust security features against unauthorized access.
Thankfully, these attacks were created by researchers and were not discovered by an actual attack. However, an attack like this could very well happen, so hopefully, SSD manufacturers will start patching these security vulnerabilities quickly before someone gets a chance to exploit them.

Aaron Klotz is a contributing writer for Tom’s Hardware, covering news related to computer hardware such as CPUs, and graphics cards.
-
hotaru.hino Reading the original article, it appears this needs to have both an SSD management application installed and a so-called "flex capacity" feature. But I'm confused as to if this is a problem with the management application itself or the SSD firmware. That is, can this attack work with or without the SSD management application.Reply -
Lemming Overlord Both the Bleeping Computer and Tom's Hardware articles don't really seem to understand what over-provisioning is, one calling it "an area of the SSD" and the other "a partition". It's neither. It's simply unused cells in a NAND module that are remapped once good flash cells are showing signs of going bad (taking over from the bad ones). Since there are no seek times to consider in an SSD, once a cell goes bad, it is simply copied/cloned to a good cell from the over-provisioning stock.Reply
They are neither "an area" nor "a partition". They are spare cells in the NAND flash module, and usually equitatively spread out across the NAND flash modules on the PCB of the SSD (of if there were 4 Flash modules on the PCB, the over-provisioning would come equally from all 4).
Also, not all companies over-provision their SSDs. If you see a 500GB implementation of an SSD, it actually contains 500GB of partitionable Flash memory, plus 12GB set aside for over-provisioning. Cheaper brands tend to not over-provision their drives at all.
Typically you'll have:
Announced capacityOver-provisioningTotal capacity240 GB16 GB256 GB250 GB6 GB256 GB256 GB0 GB256 GB480 GB32 GB512 GB500 GB12 GB512 GB512 GB0 GB512 GB960 GB64 GB1024 GB1000 GB24 GB1024 GB1024 GB0 GB1024 GB
So, SSDs that typically display a lower storage capacity in their "band" (i.e. 256, 512, 1024), will be more reliable as they can re-allocate more data from dying NAND cells to fresh NAND cells. No over-provisioning means you might find yourself in trouble faster than you'd hope for.
Coming back to the article: it seems the malware attack targets a tiny section of the over-provisioning cells on an SSD to hide its presence, as these aren't visible to the OS. -
Sluggotg Reply
I thought the over-provisioned cells were rotated in and out with the regular cells to even out the wear and tear. I did not think that they were exclusively held in reserve until needed to replace failed cells.Lemming Overlord said:Both the Bleeping Computer and Tom's Hardware articles don't really seem to understand what over-provisioning is, one calling it "an area of the SSD" and the other "a partition". It's neither. It's simply unused cells in a NAND module that are remapped once good flash cells are showing signs of going bad (taking over from the bad ones). Since there are no seek times to consider in an SSD, once a cell goes bad, it is simply copied/cloned to a good cell from the over-provisioning stock.
They are neither "an area" nor "a partition". They are spare cells in the NAND flash module, and usually equitatively spread out across the NAND flash modules on the PCB of the SSD (of if there were 4 Flash modules on the PCB, the over-provisioning would come equally from all 4).
Also, not all companies over-provision their SSDs. If you see a 500GB implementation of an SSD, it actually contains 500GB of partitionable Flash memory, plus 12GB set aside for over-provisioning. Cheaper brands tend to not over-provision their drives at all.
Typically you'll have:
Announced capacityOver-provisioningTotal capacity240 GB16 GB256 GB250 GB6 GB256 GB256 GB0 GB256 GB480 GB32 GB512 GB500 GB12 GB512 GB512 GB0 GB512 GB960 GB64 GB1024 GB1000 GB24 GB1024 GB1024 GB0 GB1024 GB
So, SSDs that typically display a lower storage capacity in their "band" (i.e. 256, 512, 1024), will be more reliable as they can re-allocate more data from dying NAND cells to fresh NAND cells. No over-provisioning means you might find yourself in trouble faster than you'd hope for.
Coming back to the article: it seems the malware attack targets a tiny section of the over-provisioning cells on an SSD to hide its presence, as these aren't visible to the OS. -
No they are not. Over provisioning are unused cells that the controller uses when it needs to move things around and they are not in a partition it is a unpartitioned spaceReply
-
Dragos Manea Also they do not explain the OP area created manually by software, which you can manage, aka. Samsung Magician manually created OP area.Reply