'Walnut' Attack Uses Sound To Trick Sensors In Cars, Phones, And Other Devices
University of Michigan students revealed that MEMS accelerometers used in smartphones, cars, and other devices are vulnerable to sonic attacks. Attackers could exploit this vulnerability to take over systems controlled via accelerometer data--but you don't have to soundproof your phone just yet.
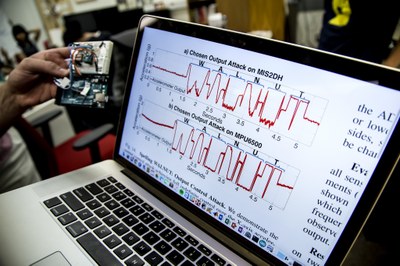
The students demonstrated their findings by modifying a music video with additional tones meant to interfere with a nearby phone's accelerometer. They managed to trick the sensor into outputting data that spelled "WALNUT"--so, naturally, they decided to call their experiment the Walnut Attack. The students also showed how an RC vehicle controlled by a Samsung phone's accelerometer could have its steering disrupted via sonic-based attacks.
The attack is relatively basic. "Capacitive MEMS accelerometers use the deflection of a mass as a proxy for measuring acceleration," the students explained in their write-up. "Acoustic pressure waves exhibit forces on physical objects in their path," they said, which means "subjecting the sensing mass–spring structure to acoustic interference at its resonant frequency can displace the sensing mass enough to spoof false acceleration signals."
In other words, sounds can trick accelerometers into thinking they're accelerating. Got it. Here's why that's a problem:
Attackers that have capabilities to deliver high intensity acoustic interference in close proximity to the target MEMS sensor can spoof the sensor to output arbitrary, attacker–chosen, signals. Our experiments demonstrate the spelling of the word 'WALNUT' over the output signal of a MEMS accelerometer. With proper knowledge of the algorithms that are utilizing the polluted sensor data, adversaries may be able to control the behavior of a system that relies on the sensor data to make automated decisions.
Using a music video in their demonstration also let the students illustrate another point--the sounds don't have to be isolated to affect targeted accelerometers. They noted that the "interference remains effective even when combined with videos and music that could be automatically played from websites, email attachments, Twitter links tapped on a smartphone, etc." That makes it harder for you to defend against these sonic-based attacks.
The good news is that none of this is life-threatening, so even though many different types of device use these vulnerable accelerometers, you shouldn't have to worry too much about trying to protect your phone or car from all outside noises. The students have a few suggestions for manufacturers, such as surrounding accelerometers with acoustic dampening foam and rejecting abnormal signals, but they also said they "have no reason to believe that acoustic sensor spoofing attacks are currently being mounted to disable autonomous cyber-physical systems" or used for other attacks.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Still, much like the revelation that malware could turn headphones into microphones, the Walnut Attack is another sign that cyber attacks don't all come in the same flavor. Sure, many of them use malware to affect a device's software or firmware, but attacks on other components, whether they're headphones or accelerometers, can also make a device vulnerable to attack--even if it's currently limited to spelling "WALNUT" or crashing RC vehicles.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.