Hacker Finds Hidden 'God Mode' on Old x86 CPUs
LAS VEGAS — Some x86 CPUs have hidden backdoors that let you seize root by sending a command to an undocumented RISC core that manages the main CPU, security researcher Christopher Domas told the Black Hat conference here Thursday (Aug. 9).
The command — ".byte 0x0f, 0x3f" in Linux — "isn't supposed to exist, doesn't have a name, and gives you root right away," Domas said, adding that he calls it "God Mode."
The backdoor completely breaks the protection-ring model of operating-system security, in which the OS kernel runs in ring 0, device drivers run in rings 1 and 2, and user applications and interfaces ("userland") run in ring 3, furthest from the kernel and with the least privileges. To put it simply, Domas' God Mode takes you from the outermost to the innermost ring in four bytes.
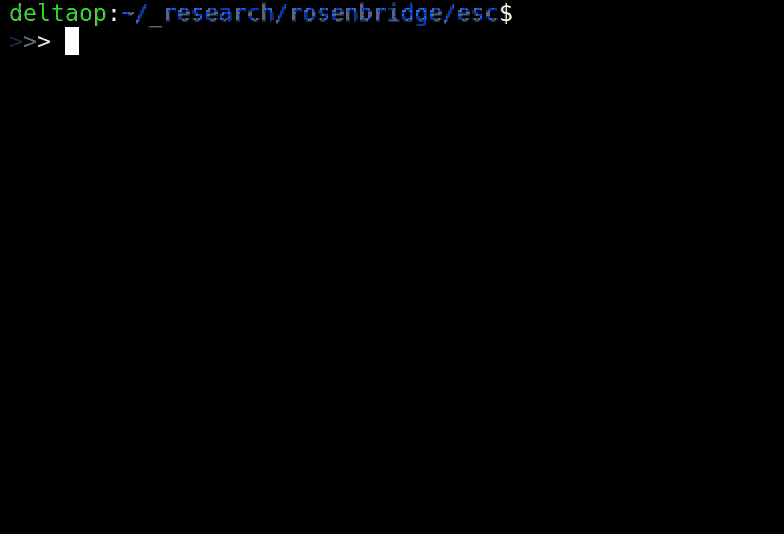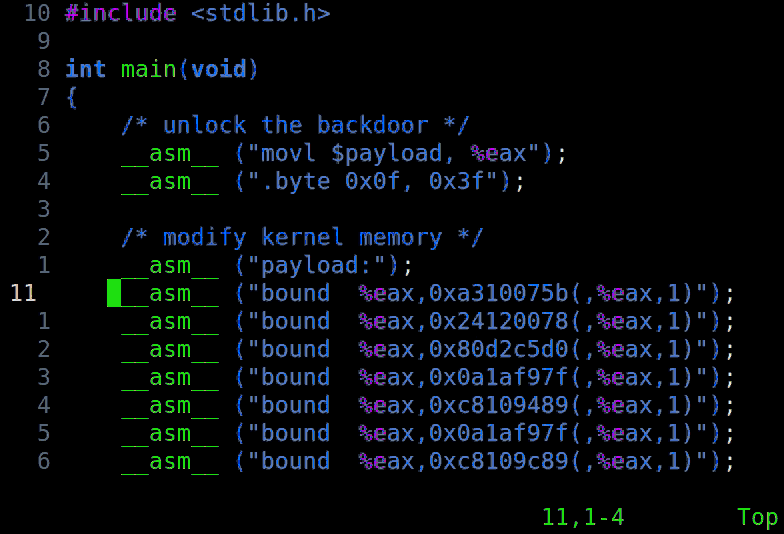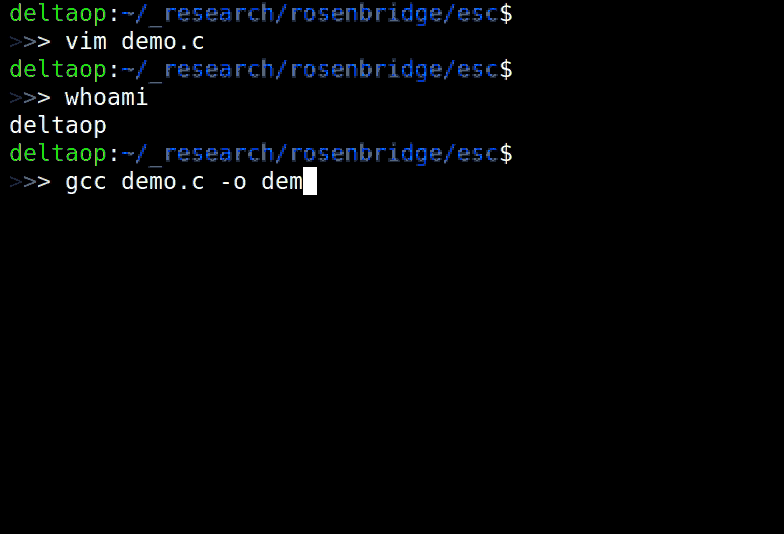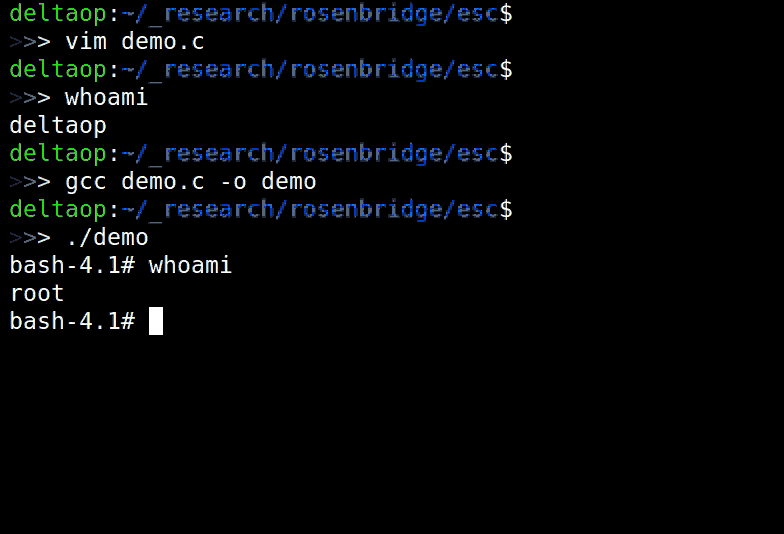
"We have direct ring 3 to ring 0 hardware privilege escalation," Domas said. "This has never been done."
That's because of the hidden RISC chip, which lives so far down on the bare metal that Domas half-joked that it ought to be thought of as a new, deeper ring of privilege, following the theory that hypervisors and chip-management systems can be considered ring -1 or ring -2.
"This is really ring -4," he said. "It's a secret, co-located core buried alongside the x86 chip. It has unrestricted access to the x86."
The good news is that, as far as Domas knows, this backdoor exists only on VIA C3 Nehemiah chips made in 2003 and used in embedded systems and thin clients. The bad news is that it's entirely possible that such hidden backdoors exist on many other chipsets.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
"These black boxes that we're trusting are things that we have no way to look into," he said. "These backdoors probably exist elsewhere."
Domas discovered the backdoor, which exists on VIA C3 Nehemiah chips made in 2003, by combing through filed patents. He found one — US8341419 — that mentioned jumping from ring 3 to ring 0 and protecting the machine from exploits of model-specific registers (MSRs), manufacturer-created commands that are often limited to certain chipsets.
Domas followed the "trail of breadcrumbs," as he put it, from one patent to another and figured out that certain VIA chipsets were covered by the patents. Then he collected many old VIA C3 machines and spent weeks fuzzing code.
He even built a testing rig consisting of seven Nehemiah-based thin clients hooked up to a power relay that would power-cycle the machines every couple of minutes, because his fuzzing attempts would usually crash the systems. After three weeks, he had 15 GB of log data — and the instructions to flip on the backdoor in the hidden RISC chip.
"Fortunately, we still need ring 0 access to start the launch process, right?" Domas asked. "No. Some of the VIA C3 x86 processors have God Mode enabled by default. You can reach it from userland. Antivirus software, ASLR and all the other security mitigations are useless."
Domas has put all his research, plus tools to check whether your VIA C3 CPU might have an undocumented coprocessor and to disable the coprocessor by default, up on his GitHub page at https://github.com/xoreaxeaxeax/rosenbridge.
-
bit_user Reply
Gee, kinda important detail to bury half-way down the article, eh?21218956 said:he good news is that, as far as Domas knows, this backdoor exists only on VIA C3 Nehemiah chips made in 2003 and used in embedded systems and thin clients. -
dudmont Reply21219169 said:
Gee, kinda important detail to bury half-way down the article, eh?21218956 said:he good news is that, as far as Domas knows, this backdoor exists only on VIA C3 Nehemiah chips made in 2003 and used in embedded systems and thin clients.
If he had mentioned it in the 2nd paragraph, would you have stayed for the rest? ;) -
bit_user Reply
Yes. I read the whole thing. It's not exactly War & Peace.21219269 said:21219169 said:
Gee, kinda important detail to bury half-way down the article, eh?21218956 said:he good news is that, as far as Domas knows, this backdoor exists only on VIA C3 Nehemiah chips made in 2003 and used in embedded systems and thin clients.
If he had mentioned it in the 2nd paragraph, would you have stayed for the rest? ;)
Now, had it been in the headline (where it belongs, IMO), I can believe the article would've gotten fewer clicks.
I definitely respect the amount of effort that went into finding this. That part was definitely worth the read. -
Karadjgne There's ppl who most definitely know where the back doors are, and how to access them, exploit them etc. They know, because they put them there in the first place. Some engineer who designed the 2003 Via C3 chips is cussing up a storm right about now. It's one secret that should have been buried and gone to the grave. And up til now, it did. But now some genius has advertised how to get at it, quite simply, so all those hackers worldwide, who tried and failed to find one, now have a serious clue as to how to get in. On other chips. Meltdown and Spectre are bad enough, but when is 'backdoor fever' gonna be allowed to die out. Stuff like this is just adding fuel to the fire.Reply -
mapesdhs Karadjgne, that reads way too much like, there's a problem but we shouldn't talk about it. Better to expose and deal with loopholes now, then let one's enemies exploit them later.Reply -
Karadjgne Whereas I see it as more like a bank robber posting for the world to see just what tools are needed and directions on just how to rob a bank and get away with it. There's multiple ppl who wouldn't know all that normally who'd go ahead and try/do it anyways. It's a Pandoras Box.Reply -
shrapnel_indie Reply21220088 said:Whereas I see it as more like a bank robber posting for the world to see just what tools are needed and directions on just how to rob a bank and get away with it. There's multiple ppl who wouldn't know all that normally who'd go ahead and try/do it anyways. It's a Pandora's Box.
Indeed, it is a Pandora's Box Yes, more people know how to access and exploit now... but that doesn't mean those who you really wish to never know didn't already know and were already taking advantage of it. Espionage, or plain spying on us by those in high levels know more than we'll ever know or want to know. -
jimmysmitty Reply21219269 said:21219169 said:
Gee, kinda important detail to bury half-way down the article, eh?21218956 said:he good news is that, as far as Domas knows, this backdoor exists only on VIA C3 Nehemiah chips made in 2003 and used in embedded systems and thin clients.
If he had mentioned it in the 2nd paragraph, would you have stayed for the rest? ;)
No but it can push this article into the realm of "clickbait". It makes it seem like a CPU you or I might use or have used has it. No consumer used a VIA x86 CPU. The headline should mention that it is a Via CPU. -
matt91.mek Ah, VIA, the consumer tower chipset guys of 00's. It's a good thing Chen Ing-hau never found out about this. :PReply