Ryzen 3000 fix for 'Sinkclose' vulnerability arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all [Updated]
AMD has changed its mind and will add Sinkclose mitigation for Ryzen 3000 shortly.

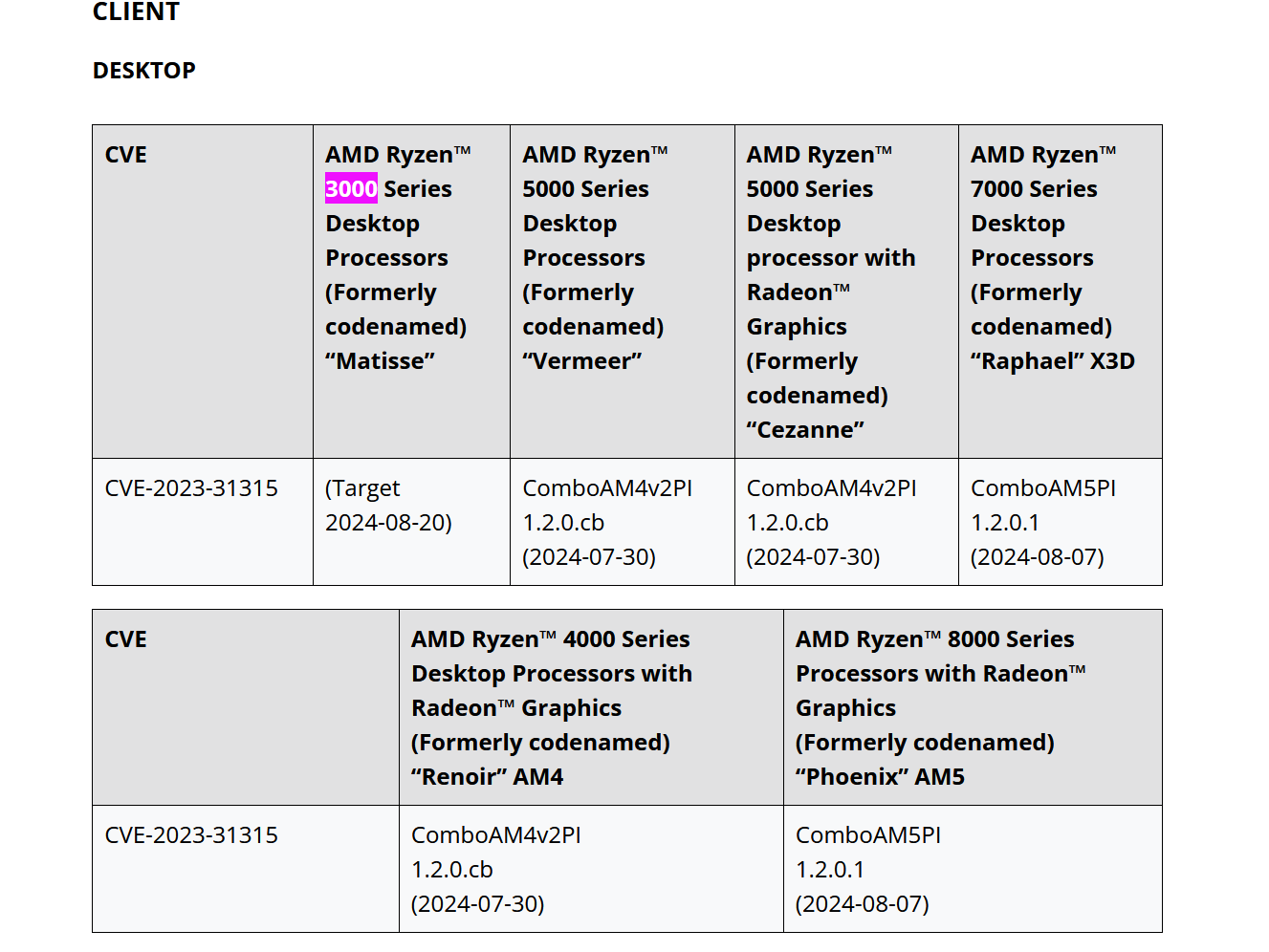
AMD has reversed course and decided to patch the new 'Sinkclose' vulnerability on Ryzen 3000 desktop processors after all. AMD updated its SMM Lock Bypass Security Bulletin, which now includes a fix for Ryzen 3000 desktop CPUs (codenamed Matisse) scheduled for tomorrow, August 20.
Sinkclose is a significant security vulnerability that has affected virtually all AMD processors since 2006. The vulnerability takes advantage of a flaw within the System Management Mode (SMM) in affected chips, allowing hackers to execute code within the SMM. This makes attacks made from the SMM virtually impossible to detect via antivirus software. The vulnerability is difficult to detect and delete and can even persist after an OS reinstall.
Thankfully, this vulnerability is difficult to exploit and requires hackers to use a different exploit to gain access to the computer's kernel before Sinkclose can be used to access the SMM. Regardless, this is a serious vulnerability, no matter how you look at it, and one that AMD is working to patch as soon as possible.
AMD had previously confirmed that it would patch the Sinkclose vulnerability on some of its impacted chips, which include various Zen parts, including server, mobile, and desktop. However, AMD listed Ryzen 3000 as not being planned for a patch, and all of its predecessors were not listed in the advisory at all.
Ryzen Threadripper 3000, Threadripper Pro 3000WX, Zen 2 EPYC (7002), Ryzen 3000 mobile, and Ryzen 3000/4000 APUs all were in AMD's original plans to be patched (and still are).
Thankfully, AMD has officially confirmed a Sinkclose patch for the Ryzen 3000 chips, but it still hasn't listed previous Zen processors. The update for Ryzen 3000 will come out tomorrow. Strangely, AMD did not disclose what microcode update will feature this fix for Matisse processors, even though AMD lists a microcode version for every other CPU lineup getting the fix.
EDIT 8/20/2024: Clarified the processors that aren't listed for a patch.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Aaron Klotz is a contributing writer for Tom’s Hardware, covering news related to computer hardware such as CPUs, and graphics cards.
-
slightnitpick ReplyAMD had previously confirmed that it would patch the Sinkclose vulnerability on all its outgoing Ryzen CPUs, including the Zen 1 architecture chips.
The link you give doesn't support this statement:
https://www.tomshardware.com/pc-components/cpus/amd-wont-patch-all-chips-affected-by-severe-data-theft-vulnerability-ryzen-1000-2000-and-3000-will-not-get-patched-among-othersAccording to a statement given to Tom's Hardware, AMD said, "There are some older products that are outside our software support window."
-
Amdlova If they fix this will be good :) have tons of these machines worldwide less e-waste :)Reply -
toaste Reply
The article doesn't mention a performance hit.Bikki said:Performance hit? Count me out!
Sinkclose affects System Management Mode entry/exit. SMM exists from the time of the Intel 386SL, when there was no deletating things like timer interrupts or fan control to a microcontroller. Unfortunately modern UEFI vendors will still use it to implements things like power button presses, rtc interrupts, legacy usb keyboard interrupts and a few other things.
Any performant UEFI implementation will spend as few cycles in SMM as possible. Every clock cycle you spend in SMM is a direct reduction to performance of the OS/software.
If there even is a performance impact, it would be on the order of a few extra clock cycles to an already rare SMM exit. I expect it would be so small as to be impossible to even measure, though I look forward to anyone who benchmarks the before/after to try to quantify it. -
bobalazs Title is bad. Having english as a secondary language i can sayReply
'Sinkclose' vulnerability arrives tomorrowshould be fixed to
'Sinkclose' vulnerability fix arrives tomorrow -
mitch074 Reply
actually not, because it's the fix for the vulnerability that arrives - you'd repeat "fix", and that's a no-no.bobalazs said:Title is bad. Having english as a secondary language i can say
'Sinkclose' vulnerability arrives tomorrowshould be fixed to
'Sinkclose' vulnerability fix arrives tomorrow -
bobalazs WDYM? The Vulnerability is already there. The topic is about offering a fix for the vulnerability.Reply
Sinkclose does not arrive tomorrow it's an active vulnerability already.
Sinkclose vulnerability fix arrives tomorrow is what makes sense. -
slightnitpick Reply
The full title is: Ryzen 3000 fix for 'Sinkclose' vulnerability arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after allbobalazs said:WDYM? The Vulnerability is already there. The topic is about offering a fix for the vulnerability.
Sinkclose does not arrive tomorrow it's an active vulnerability already.
Sinkclose vulnerability fix arrives tomorrow is what makes sense.
Your correction would turn this into: Ryzen 3000 fix for 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
Which implies that the fix itself needed a fix.
or at best: Ryzen 3000 for 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
which is grammatically incorrect.
Though: Ryzen 3000 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
No "for", would be a fine title as well.
My knowledge of grammatical structure isn't the best, but what I think is happening is that grammatically the original title makes "Ryzen 3000 fix" the object of the sentence and "Sinkclose vulnerability" the subject. While the last option, with fix after vulnerability, makes "Ryzen 3000" an adjective of "Sinkclose vulnerability". -
bobalazs Reply
Sinkclose vulnerability fix arrives tomorrow is what i saidslightnitpick said:The full title is: Ryzen 3000 fix for 'Sinkclose' vulnerability arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
Your correction would turn this into: Ryzen 3000 fix for 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
Which implies that the fix itself needed a fix.
or at best: Ryzen 3000 for 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
which is grammatically incorrect.
Though: Ryzen 3000 'Sinkclose' vulnerability fix arrives tomorrow — AMD reverses course and will patch Ryzen 3000 after all
No "for", would be a fine title as well.
My knowledge of grammatical structure isn't the best, but what I think is happening is that grammatically the original title makes "Ryzen 3000 fix" the object of the sentence and "Sinkclose vulnerability" the subject. While the last option, with fix after vulnerability, makes "Ryzen 3000" an adjective of "Sinkclose vulnerability".
not
Ryzen 3000 for 'Sinkclose' vulnerability fix arrives tomorrow
you are grammatically incorrect sir.
'Sinkclose' vulnerability arrives tomorrow was the original title, that was bad.
P.S. the title had been fixed, so i was right all along...