Android 'Gooligan' Malware Affects 1M Google Accounts; Google Mitigates The Attack
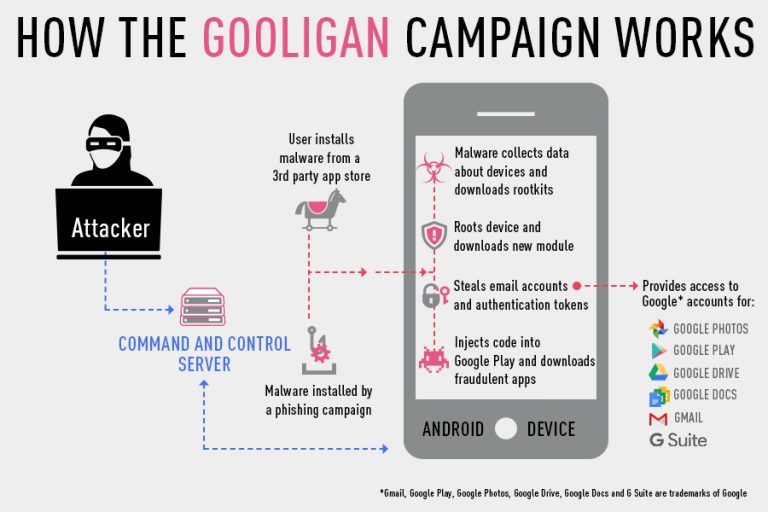
Check Point, a security company, uncovered an Android malware campaign called “Gooligan” that affected one million Google accounts. The malware roots infected devices, which then allows it to steal authentication tokens that could be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, and more.
74% Android Users Vulnerable To Gooligan Malware
Android 4 (Jelly Bean, KitKat) and 5.0 (Lollipop) are vulnerable to the Gooligan malware, so over 74% of Android devices could be affected by it. However, the malware seems to be spread mainly through apps downloaded from third-party app stores.
For the most part, users who only download their apps should be safe, although Google did mention that some apps related to the Gooligan malware were found on the Play Store, too. Most of the users that were infected by Gooligan live in Asia (57%), where installing apps from third-party stores is more common. Only 9% of the infected users are from Europe, while 19% of the infections happened in the Americas and 15% in Africa.
Tens Of Applications Infected With Gooligan
Check Point researchers identified tens of applications that came pre-loaded with the malware. Most were downloaded by unsuspecting users from the third-party stores, but some were also sent via SMS messages in phishing campaigns.
The malware family was first uncovered last year by multiple security companies. That's when the malware creators suspended their campaign--until this summer, when they re-launched the malware with a new architecture that could inject malicious code into Android system processes.
According to Check Point, the change in the architecture may help finance the malware campaign through fraudulent ad activity. The malware could simulate clicks on ads that install applications, and then the authors of the malware would get paid by the ad network for those installs. Check Point said that the Gooligan malware campaign has installed over two million applications since it launched.
Google’s Response
Although Check Point said that over one million Google accounts were affected by the malware, Google claimed that there was no evidence of user data access. Google also said that the motivation for the malware campaign seems to be to promote apps (and thereby make money), not to steal user information. The company also noted that the malware didn’t seem to target specific users, and that only 0.1% of the affected accounts were GSuite enterprise customers.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Google announced that it removed the apps that were installed by Gooligan from users’ devices. A little known power that Google wields is the ability to remove or install applications on users’ devices, regardless of whether it’s a Google Nexus or Pixel phone or an Android phone made by some other manufacturer. This power is granted by the Play services framework.
The Gooligan-associated apps were also removed from the Play Store. The company also said that it worked with multiple ISPs to disrupt the malware’s infrastructure to slow down future efforts of infecting users.
Mitigations, But No Patches
Although Google can employ various anti-malware measures, including its Verify Apps service, these solutions are typically used after the infections have already begun, and not as a way to prevent them. Those infections are possible due to existing and well-known vulnerabilities in older versions of Android running on a large number of devices that were never patched. Therefore, the cause of most Android malware seems to be Android’s lack of a sane updating model.
For the devices that don’t get updated, Google can only try to keep those vulnerabilities in check through new app and process sandboxes that can limit the damage done by future exploits, as well as by identifying existing malware and trying to stop it from installing on other devices through the Verify Apps service. Although these solutions may seem "good enough," the vulnerabilities never get patched, which means Google must play a game of cat and mouse with the malware creators who will keep finding new ways to exploit unpatched vulnerabilities.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
targetdrone If Google can't(or won't) patch year old operation systems, no way IoT device manufactures ever willReply -
LeeRains This type of thing, which doesn't seem to be a rare occurrence anymore, is why I stick with the (also imperfect) iPhone.Reply -
jn77 Last time Apple boasted how secure their systems, OS and data centers were, it was less than 24 hours before 74% of IOS devices were hacked and bricked in one fashion or another so an claim that Iphones and Apple products are even close to perfect means people don't get it.Reply