Hobbyist Demonstrates Amazon Key Vulnerability
A new vulnerability in Amazon Key has been discovered. The demonstrator released a video showing how a malicious actor can plant a device near an Amazon Key that prevents it from re-locking after the deliverer has unlocked it.
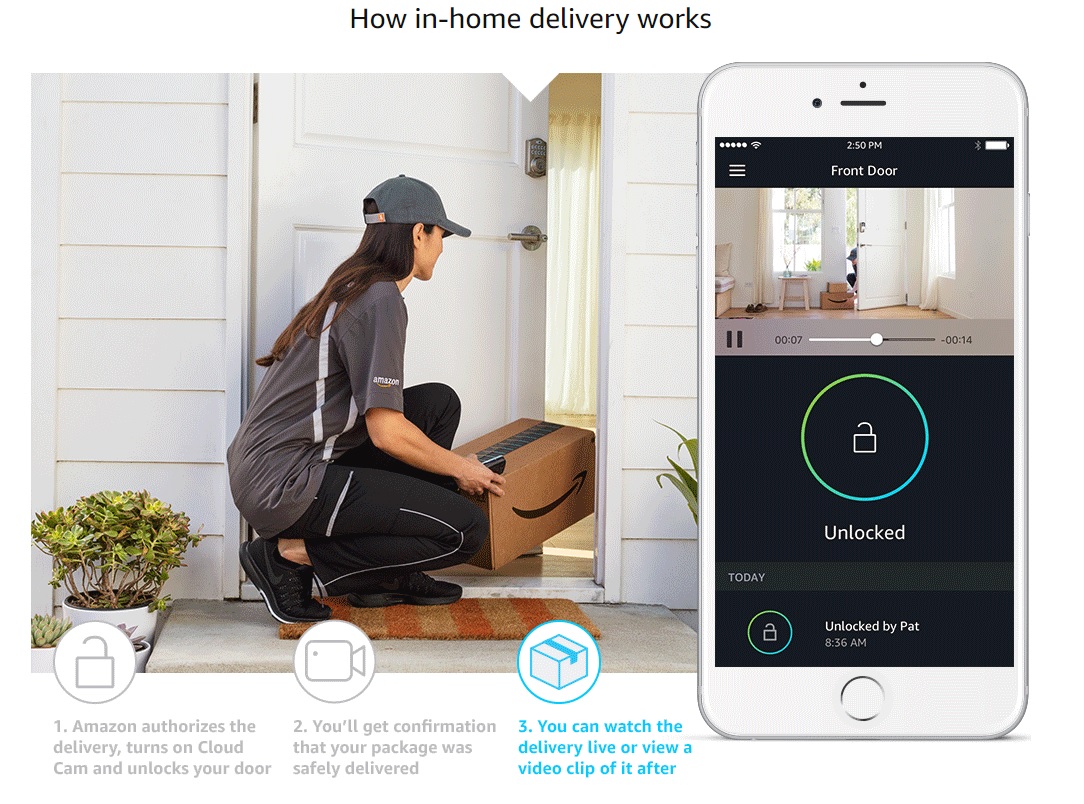
In 2017, Amazon released Amazon Key, a smart-home IOT product that lets Amazon deliverers open your door to drop off your packages. It’s a system that includes a motorized door lock and a camera. The former gets installed on the door that you want to receive deliveries at. The latter is meant to be placed to give you full view of the door and delivery area. The idea is that your Amazon deliverer can unlock your door with their Amazon app, drop off your package, and re-lock your door while you have full view of the process through the camera. As long as you’re not worried about your deliverer intentionally doing something malicious, the idea seems sound. If you’re at all aware of the sorry state of IOT device security, however, Amazon Key should be massive red flag.
Case in point, someone has revealed a new vulnerability in Amazon Key that supposedly allows a third party to enter a house after delivery. A video, released on Twitter, shows a demonstration of it occurring. First, the third party hides a small device in the a lamp near a door. After the deliverer drops off the package and leaves, the third party returns to find the door unlocked. The demonstrator then shows that when the door unlock is triggered in the app, the door physically unlocks while the app loops with its status reading “unlocking...”. After a short while, the door lock makes a sound before the app briefly flashes a status that says the unlocking event timed out. The door remains unlocked, however, and the app does not log any unlocking event.
No details on what the hidden box is doing or the nature of the vulnerability were revealed because the demonstrator is withholding the details until Amazon fixes the issue. The demonstrator claims that the Amazon Key this was tested on uses the most current software.
We don’t know exactly what is happening in this exploit, but the unlocking timeout brings to mind an earlier exploit shown off late last year. Rhino Labs, who discovered it, explained that by DDOSing the Amazon Key system after the unlocking event, they could both prevent re-locking and freeze the image transmitted by the camera. Rhino’s scenario showed how the DDOS could be executed right after the door closes but just before the door locks. A third party could then enter, while the camera continues to show a closed door, before ending the DDOS attack and allowing the door to lock. Again, we can’t say these exploits are related, but the hidden device that plays a role in the new exploit certainly suggest some kind of Wi-Fi DDOS is involved.
Those who follow cyber security developments will be aware of the growing concern in the industry over the poor state of security in a huge amount of IOT devices. The market for connected devices is growing because consumers desire the convenience they afford, but they aren’t necessarily willing to pay a huge premium for it. The fast growing and competitive nature of the IOT market encourages companies to quickly release cheap, disposable products, and that will incentivizes corner-cutting. So long as cyber threats continue to be viewed as isolated cases of targeted attacks with low probability, manufacturers won’t have an incentive to invest in security. Ironically, the more ubiquitous any particular IOT product becomes, the more likely it is to become a ticking time bomb for its manufacturer. This is something we’ve already witnessed with the Mirai botnet.
More recently, the building narrative of IOT security worries have led to some positive advancements. ARM announced the development of its Platform Security Architecture, with the hopes of lowering development costs for securing future IOT devices, and several IOT security-focused industry collaborations have been formed. Ultimately, the companies that will dominate this market will be the ones that view security as an asset, rather than a cost. If vulnerabilities are being discovered so quickly in an IOT product from a company with as much development assets as Amazon, then the prospects will certainly not be good for those from companies with but a fraction of the resources. For now, consumers need to be aware of what they’re buying into with IOT devices. They may advertise clever ways of improving our lives, but they ignore the risks they introduce.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
-
dextermat It feels like they do it on purpose. We know that everything connected to internet is vulnerable one way or another, yet they continue to develop devices and software that makes things even worse.Reply -
tamalero I cant wait for the NSA and similar agencies using these tools to open doors to any house just because..Reply -
DavidC1 I am not sure what's worse.Reply
The fact that some stranger getting paid minimum wage quite likely has not much to lose opening the door to your home for a delivery,
or
Trusting the security of your home to an Internet-connected lock.
I guess they are both stupid. And with Amazon key, you get 2 stupid ideas for the price of one.
Heck, people seem to be less trustworthy than ever! You want to trust your home key to a delivery person?!? -
captaincharisma you really have to wonder about the intelligence of people who put these smart locks on their doors just to have the convenience of opening your house or car door with a smartphone.Reply -
lsatenstein What would be better than the door lock is the door latch. The door latch is a device that many who live on the second of a two story dwelling. They press a button to release the spring latch. Once the button is released, the latch is reset. This could be done with the Amazon product if the latch had a 5 second timeout. The deliverer could push open the door, put the package inside and exit.Reply
For the single family dwelling, an automatic timeout feature to activate the lock could be put in place. In Delivery mode, no lock could remain unlocked for 7 seconds. -
alextheblue Reply
Man that is the least of your worries if you've got one of the alphabet agencies breathing down your neck. LMAO...20675014 said:I cant wait for the NSA and similar agencies using these tools to open doors to any house just because..
While you're at it just get a Mr. Handy, he can receive your packages and zap unauthorized personnel!20677276 said:What would be better than the door lock is the door latch.
<snip>
For the single family dwelling, an automatic timeout feature to activate the lock could be put in place. In Delivery mode, no lock could remain unlocked for 7 seconds. -
Godloki It's not like it's super hard to pick a physical lock either... If an expert wants to break in to your house they're going to.Reply -
Lostinlodos Godloki has it.Reply
Locking your door is the home equivalent of TSA, minus the groping.
It will stop a petty crook but any well informed individual including bad doers can bypass the security in seconds.
I still lock my door though.