Let’s Encrypt To Become A Trusted Root Certificate Authority In Firefox 50
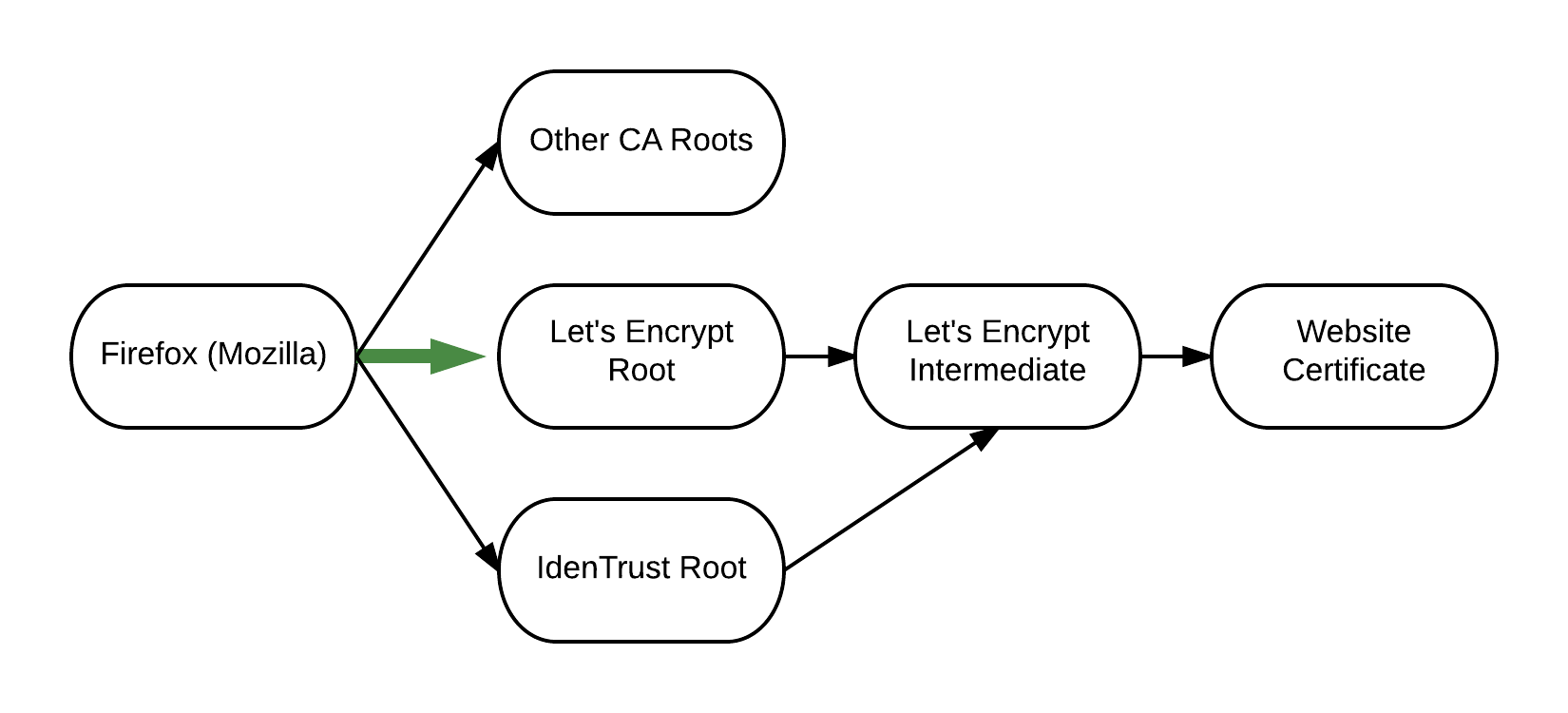
Firefox 50, which Mozilla scheduled to ship by the end of this year, will begin to trust Let’s Encrypt certificates by default. Until now, Let’s Encrypt certificates had to be cross-signed by another certificate authority called IdenTrust in order for browsers to trust them.
Mozilla will accept Let’s Encrypt in its own certificate root store starting with Firefox 50 later this year. Let’s Encrypt wasn’t able to gain the privilege of becoming a trusted root CA by any browser right at the launch of the service because it was new, so many things could’ve gone wrong.
Normally, it takes 3-6 years for a new CA to enter the certificate root stores of various browser and OS vendors. However, IdenTrust helped Let’s Encrypt’s certificates become trusted right away by cross-signing them. In essence, IdenTrust would “vouch” for the trustworthiness of Let’s Encrypt certificates, giving Let’s Encrypt a “shortcut” into the certificate market.
ISRG, the organization that manages the services, has always intended to make Let’s Encrypt an independent certificate authority. Now, thanks to Mozilla (a founding member of Let’s Encrypt), the service can make the first step towards that independence. After being thoroughly tested by millions of developers who are using Let’s Encrypt certificates, Mozilla decided that the Let’s Encrypt automated certificate service works well enough to add to its certificate root store.
Other browsers such as Chrome and Edge rely on the operating system’s root store for the trusted root certificates. Therefore, it’s up to Microsoft, but also Google (Android, Chrome OS), and other OS vendors to allow Let’s Encrypt in their certificate root stores before other browsers can trust it by default. ISRG has already applied for inclusion in the root stores of Microsoft, Google, Apple, Oracle, and BlackBerry.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
problematiq This seems like a very bad idea. As it is a good portion of the certs "Lets Encrypt" hands out are to malicious actors. We have all certs from "Lets Encrypt" set to distrust by default for this reason. It really is a shame because I 100% support what "Lets encrypt" is doing, because of malicious actors, whats the saying? "This is why we can't have nice things."Reply