Rep. Ted Lieu Blames NSA For Unpatched Carrier Vulnerability That Allowed His Calls To Be Intercepted On '60 Minutes'
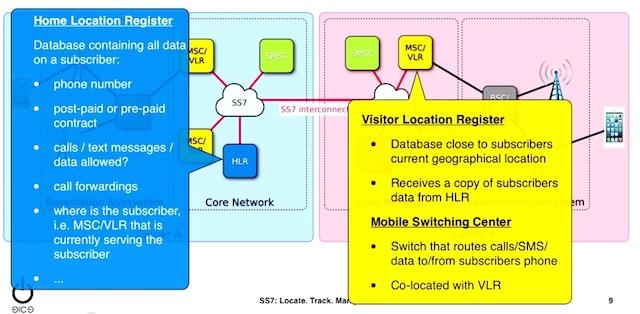
CBS News’ "60 Minutes" ran a story about a phone carrier network vulnerability that has remain unpatched for years, even after being exposed by white hat hackers. The show gave Rep. Ted Lieu of California an iPhone, which was then hacked through a vulnerability in the Signaling System Seven (SS7) system used by carriers around the world to exchange billing information.
Back in December 2014, several white hat hackers, including Karsten Nohl, exposed how the carriers’ weakly protected SS7 system can be hacked by just about anyone, without too much expense. The targets could include even U.S. Congress members, as well as the U.S. President if he uses the regular carrier network for calls--as President Obama did last year when he called Rep. Ted Lieu of California directly, according to Lieu.
Hacking Rep. Ted Lieu's Phone
Karsten Nohl was contacted by the 60 Minutes team to try and hack the phone the team gave to Rep. Ted Lieu for this experiment. When the team later contacted Lieu, Nohl was able to hear their conversation with the Congressman, and he also recorded several subsequent calls Rep. Lieu made.
When the 60 Minutes crew played the recordings back to Lieu, he said it was creepy that hackers could do this to a Congressman, and that it also made him angry that the NSA knew about this but doesn’t want to fix the problem:
“They could hear any call of pretty much anyone who has a smartphone. It could be stock trades you want someone to execute. It could be calls with a bank,” Congressman Ted Lie noted in 60 Minutes segment.“That the people who knew about this flaw and saying that should be fired. You cannot have 300-some million Americans--and really, right, the global citizenry be at risk of having their phone conversations intercepted with a known flaw, simply because some intelligence agencies might get some data. That is not acceptable,” he added.
Intelligence Agencies Must Take Responsibility For Weak Security
The phone networks both in the U.S. and abroad were built on weak security decades ago, in part because they didn’t realize how vulnerable these systems could be in the future, and in part because intelligence agencies wanted their phone calls to be easily intercepted. However, this has now backfired in a significant way, with any hacker from anywhere in the world being able to spy on phone calls or texts from a U.S. Congressman, or a judge, journalist, or anyone who they may deem a target.
This is yet another failure of the intelligence agencies and governments who put spying ahead of actual security. It’s now been proven again and again that when you put holes into a system’s security, those holes can be used by anyone once they're discovered. It’s usually just a matter of time until those holes are discovered, but then it may take many more years to fix, because it’s too hard to get all the global phone carriers to upgrade to a more secure system all at once.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
We’re now about to upgrade to another next-generation network, the 5G network, but yet again it doesn’t seem like security is a primary focus. With 5G supposed to arrive by 2020, and then last for at least another 7-8 years before upgrading to something else, we’re looking at another 10-15 years in which the security of the phone networks would be vulnerable to hackers.
The intelligence agencies always seem to talk about how important cybersecurity and protecting critical infrastructures is (in which phone networks are included), but they never seem to prioritize strong security over the spying capabilities within these systems.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
junkeymonkey well thing is wireless systems are not covered under the fed wiretapping act , but does fall under freedom of the airwaves actReply
sorry ted , maybe stick to land line services -
Chris Droste please; Piss off another 40 or so Senators so we can stop this B.S. with back door security/decryption crap; especially those who were trying to push state and federal anti-encryption legislature.Reply -
nanoflower With the problem being in the SS7 system doesn't that mean that all phone calls are equally vulnerable. Even those on hard lines?Reply -
junkeymonkey if you use a cordless phone even if used with a hard line the wireless transmission between the hand set and the reciver is still freedom of the airwaves and anyone can receive what you transmitReply
so anything at your house you do over wireless and is transmitting I can sit out side and recive and use - that's all there is to it just like a raido broadcast
BUT... I cant use it in any legal sense unless the wiretapping criteria is meet
''The kid next door can probably crack your WEP Wi-Fi encryption if he puts his mind to it. The neighbor across the street can purchase a radio scanner that can monitor your cordless phone transmissions''
http://cellphonetapped.com/wiretapping-laws/
now in my opinion the news guys who did this should be in violation of the law and can be prosecuted if one of the partys in the conversation did not agree to having that done if one party agreed to it then its just too bad so sad for sen. tom ....
and why lawyers get paid the big money to twist all this around . in the end the damage was done and released - no taking that back
http://communications-media.lawyers.com/privacy-law/wiretapping.html -
ddpruitt Jesus, Will Tom's ever stop NSA caused it click-bait articles?Reply
This wasn't the NSA's fault, they didn't build the network. The carriers have been told about all sorts of flaws in their system. It doesn't take a genius to figure out why they don't want to fix it, it costs money. Until people care enough about security to change carriers or you force them through legislation it'll never get fixed.
How about reporting that the senator voted against a bill that would require a warrant to search a cell phone?
Oh wait I know why, because that doesn't fit the "It's all the NSA's fault" company line. -
house70 I hope that more "deciders" get their communications hacked; only then security will be taken seriously.Reply
While NSA didn't build the network, they have not pushed to make communications more secure,either, despite their name (N Security A). As long as it suited their "spy on our own, spy on everyone" agenda, keeping mum about any and all security flaws was/is their de facto m.o. -
poochiepiano Replynow in my opinion the news guys who did this should be in violation of the law and can be prosecuted if one of the partys in the conversation did not agree to having that done if one party agreed to it then its just too bad so sad for sen. tom ....
Uhh, seems to me that 60 Minutes and Sen. Lieu were working together to prove a point (despite how the dramatic title implies otherwise). -
f-14 There's a reason education sucks, it's the same reason that it will never, ever, ever be fixed. It's never going to get any better, don't look for it, be happy with what you got. Because the owners of this country don't want that. I'm talking about the real owners, now. The real owners, the big wealthy business interests that control things and make all the important decisions. Forget the politicians, they're an irrelevancy. The politicians are put there to give you the idea that you have freedom of choice. You don't. You have no choice. You have owners. They own you. They own everything. They own all the important land. They own and control the corporations. They've long since bought and paid for the Senate, the Congress, the statehouses, the city halls. They've got the judges in their back pockets. And they own all the big media companies, so that they control just about all of the news and information you hear. They've got you by the balls. They spend billions of dollars every year lobbying, lobbying to get what they want. Well, we know what they want; they want more for themselves and less for everybody else.Reply
But I'll tell you what they don't want. They don't want a population of citizens capable of critical thinking. They don't want well-informed, well-educated people capable of critical thinking. They're not interested in that. That doesn't help them. That's against their interests. They don't want people who are smart enough to sit around the kitchen table and figure out how badly they're getting fucked by a system that threw them overboard 30 fucking years ago.
You know what they want? Obedient workers, people who are just smart enough to run the machines and do the paperwork but just dumb enough to passively accept all these increasingly shittier jobs with the lower pay, the longer hours, reduced benefits, the end of overtime and the vanishing pension that disappears the minute you go to collect it. And, now, they're coming for your Social Security. They want your fucking retirement money. They want it back, so they can give it to their criminal friends on Wall Street. And you know something? They'll get it. They'll get it all, sooner or later, because they own this fucking place. It's a big club, and you ain't in it. You and I are not in the big club.
This country is finished.
George Carlin 2005
https://www.youtube.com/watch?v=P_Zqbg6QThg