Avast, Cisco Confirm: CCleaner Malware Targeted Large Technology Companies
Following the recent CCleaner malware incident, Avast (the new owner of CCleaner) and Cisco’s Talos Intelligence security research group have continued to analyze the attack. The two found that the malware was more sophisticated than originally thought and was targeting large companies to steal their intellectual property.
Advanced Persistent Threat
Avast concluded that the malware was in fact a type of attack called an advanced persistent threat (APT), which is a sophisticated attack usually launched by nation states. The APT that infected CCleaner was supposed to deliver a second-stage payload only to select victims.
Of the 2.27 million users who installed the infected CCleaner version, Avast believes that only a few hundred were also infected by the second-stage payload. Avast had previously said that it believes the second stage payload was never deployed, but the company has now walked back that statement.
Large Companies Targeted
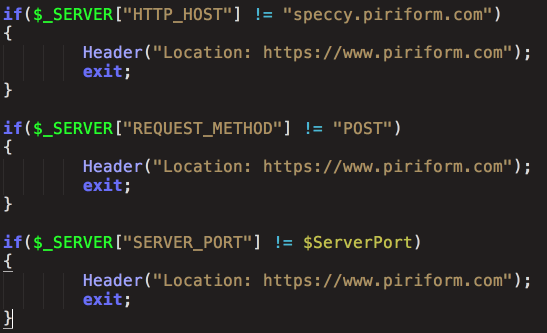
The antivirus maker stated that the APT targeted large technology and telecommunications companies from Japan, Taiwan, UK, Germany, and the U.S. via a watering hole attack, which is an attack that targets popular websites or tools used by millions, only to infect a few targets that may also use those same tools. The name is taken from the real world where some predators wait for an opportunity to pick their prey from the animals that come to drink water at a watering hole.
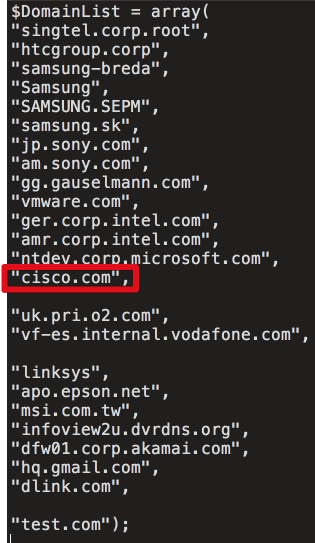
Avast didn’t want to say who were the targets of this attack, but Cisco revealed a list of targets the attackers were attempting to hack. Besides Cisco itself, the list includes Intel, HTC, Samsung, Sony, VMware, Microsoft, Vodafone, Epson, Linksys, MSI, Akamai, and a few others.
Complex Obfuscated Code
According to Avast, the second-stage payload contains complex and obfuscated code and includes two DLL components. The first component comes with anti-debugging and anti-emulation mechanisms, and its purpose seems to be finding another command and control (C2) server.
The C2 server’s address could be modified in the future, which means that it may not be enough that law enforcement shut down the original C2 servers. The attackers may be able to regain control of the infected machines and continue to control them remotely through a new another server.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The second part of the second-stage payload is responsible for persistence on the operating system, and they seem to be piggybacking on other vendors’ applications to avoid detection and maintain persistence. The 32-bit version of the code embeds itself into a Winzip package, whereas the 64-bit one uses a Symantec dll. Most of the malicious code is delivered from the registry. Avast noted that all of these techniques demonstrate a high level of sophistication from the attacker.
Attribution
Attribution is difficult for cyber attacks, as sophisticated attackers can often make it look as if someone else did it by re-using other attackers’ code or hacking styles. They may effectively hide behind reused IP addresses by launching their attacks from computers they hack in a given country. This is also why Avast is reluctant to say for sure who the attackers were right now, but it promised to continue to work with law enforcement to find out who was responsible.
However, Cisco and Kaspersky were both able to confirm that the malware uses code that overlaps with malware code used by “Group 72,” also called “Deep Panda,” “Axiom,” and “Shell Crew.” Group 72 is believed to be a cyber espionage group funded by the Chinese government, and it’s also believed to be responsible for stealing 80 million U.S. social security numbers from health insurance company Anthem.
Avast initially suggested that it should be enough to update to the clean version of CCleaner, but Cisco recommended that it would be safer to restore from backups and reimage the systems. Avast also recommends updating to CCleaner 5.35, as the company has now also revoked the Symantec certificate it was using to sign the infected 5.33 version as well as the cleaned-up 5.34 version.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
berezini "through a new another server" someone needs to go back to kindergarten and learn proper grammar.Reply -
turkey3_scratch Reply20198510 said:"through a new another server" someone needs to go back to kindergarten and learn proper grammar.
That's just a human mistake, no need to be rude. -
the_bears I just have 1 question about all of this malware fiasco.Reply
Are the versions before 5.33 infected from this, because I own x64 bit 5.30 version of CCleaner and am wondering should I remove CCleaner from my PC and reinstall if necessary ? -
nathan336 Avast hacking their own software? read more here: http://www.mad-monkey.co.uk/cgi-bin/default.pl?06,mnews-CCleaner533breachfromReply -
spiketheaardvark ccleaner seems like an odd way to hit a big company. I doubt it's on the standard install list for any of these companies IT departments. It might get in around the edges with some BYOD equipment but that greatly decreases the number of targets. I'm sure ccleaner was an easier target than trying to slip something into Office 365 subscriptions. I'd think an old fashioned phishing attack would have been easier and less time consuming.Reply -
JMLow54 Spike...Reply
Not so unusual, as CCleaner is a relatively robust way to decommission old HDDs (and to some extend SSDs); especially if the business has stored information they wish to remain private. Keep in mind that in a large company (say 100,000 employees) their inventory of deployed systems is fluid and something has to be done to protect their trade secrets.
As directly related to the article, I had 5.33 installed. Since I test various apps on my desktop system, and it varies from client to client, I prefer to do all this from within a VM so my host remains fairly unaffected. Once such test (still underway) required the use of CCleaner, and 5.33 was installed and it was infected.
Fortunately this was an installation in a VM only, and therefore no impact on my host system.
Just thought I'd add my 0.02 worth, to let you know that it does impact individual users as well - though the payload was never triggered. -
spiketheaardvark Reply20215483 said:Spike...
Not so unusual, as CCleaner is a relatively robust way to decommission old HDDs (and to some extend SSDs); especially if the business has stored information they wish to remain private. Keep in mind that in a large company (say 100,000 employees) their inventory of deployed systems is fluid and something has to be done to protect their trade secrets.
As directly related to the article, I had 5.33 installed. Since I test various apps on my desktop system, and it varies from client to client, I prefer to do all this from within a VM so my host remains fairly unaffected. Once such test (still underway) required the use of CCleaner, and 5.33 was installed and it was infected.
Fortunately this was an installation in a VM only, and therefore no impact on my host system.
Just thought I'd add my 0.02 worth, to let you know that it does impact individual users as well - though the payload was never triggered.
I didn't think about the HDD wiper. That actually makes sense then. The drives an IT department is wiping have exactly what the hackers would want.
Most of my experience with IT is at academic institutions. Asking for anything more than a computer with MS office was almost not worth the effort (and they charged the lab to install software). Everything I see in these forums about bad IT practices is the world I live in. The fact you were using a VM puts you head and shoulder above most of what I've had to put up with. During grad school (2007) my computer was an old XP machine with a public unfirewalled IP address. Based on how long it took them to roll out SP3 they delayed most patches at least a full year. The only thing between me and internet was McAfee and a poorly patched windows XP. They also gave me a laptop with whole disk encryption that was incompatible with Vista's hybrid sleep (the default). Everyone that got a laptop ended losing everything at some point all because they never read the release notes for pgp.