Malware found hidden in image files, can dodge antivirus detection entirely — VirusTotal discovers undetected SVG phishing campaign
A new report links over 500 weaponized SVGs to a phishing campaign that spoofed a Colombian government portal.

Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Scalable vector graphics (.svg) files are lightweight, XML-based images that render at any resolution. They’re usually harmless, but they can also contain active code, and hackers appear to be relying on them more often as a means to stealthily deliver malware.
A new report from VirusTotal shows just how far that tactic has evolved, unearthing a campaign that used weaponized SVGs to drop malware, spoof a government agency, and dodge antivirus detection entirely.
44 previously undetected phishing SVGs
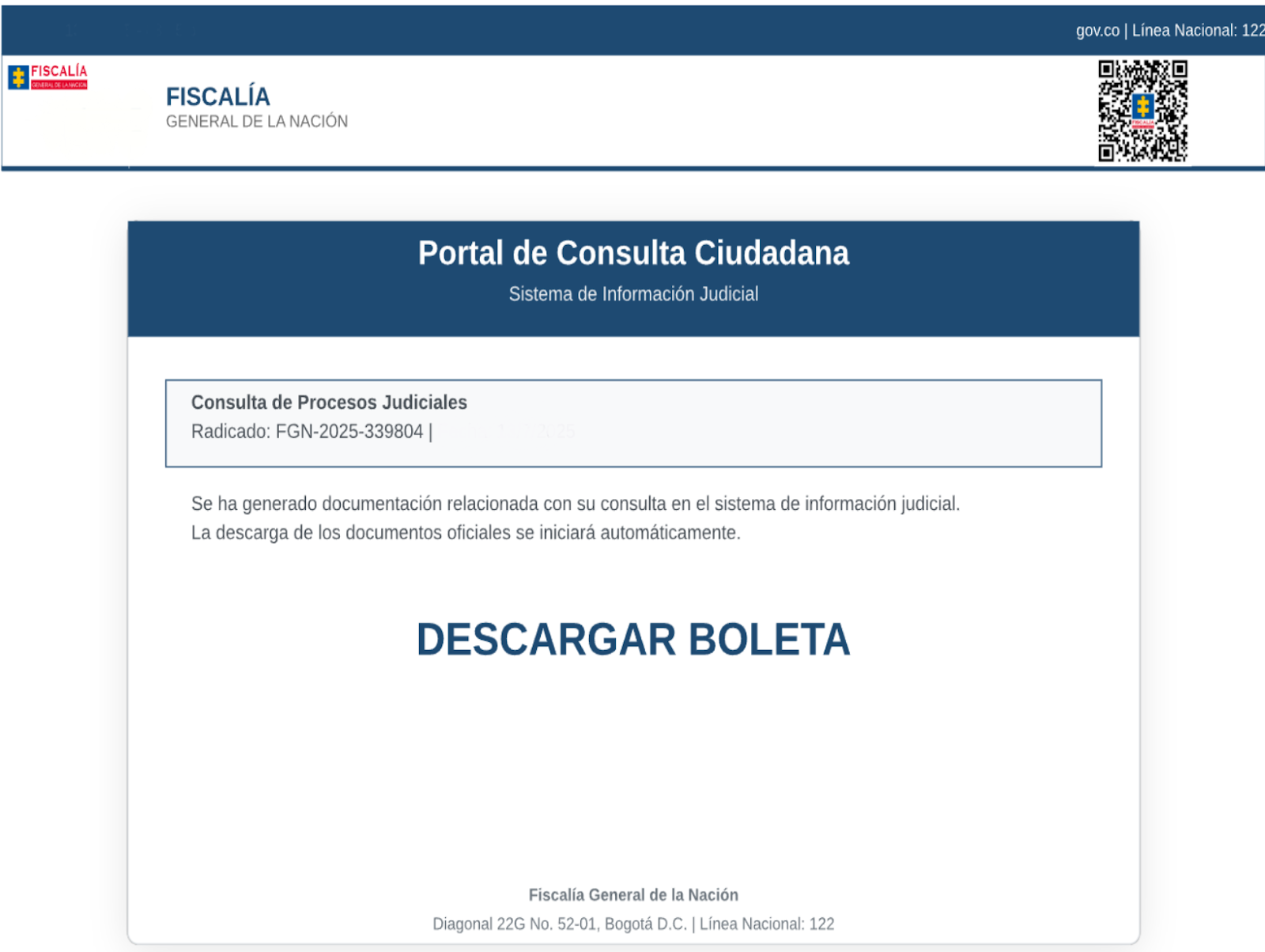
In its report published September 4, the Google-owned scanning platform said its Code Insight system had flagged an SVG file masquerading as a legal notification from Colombia’s judicial system.
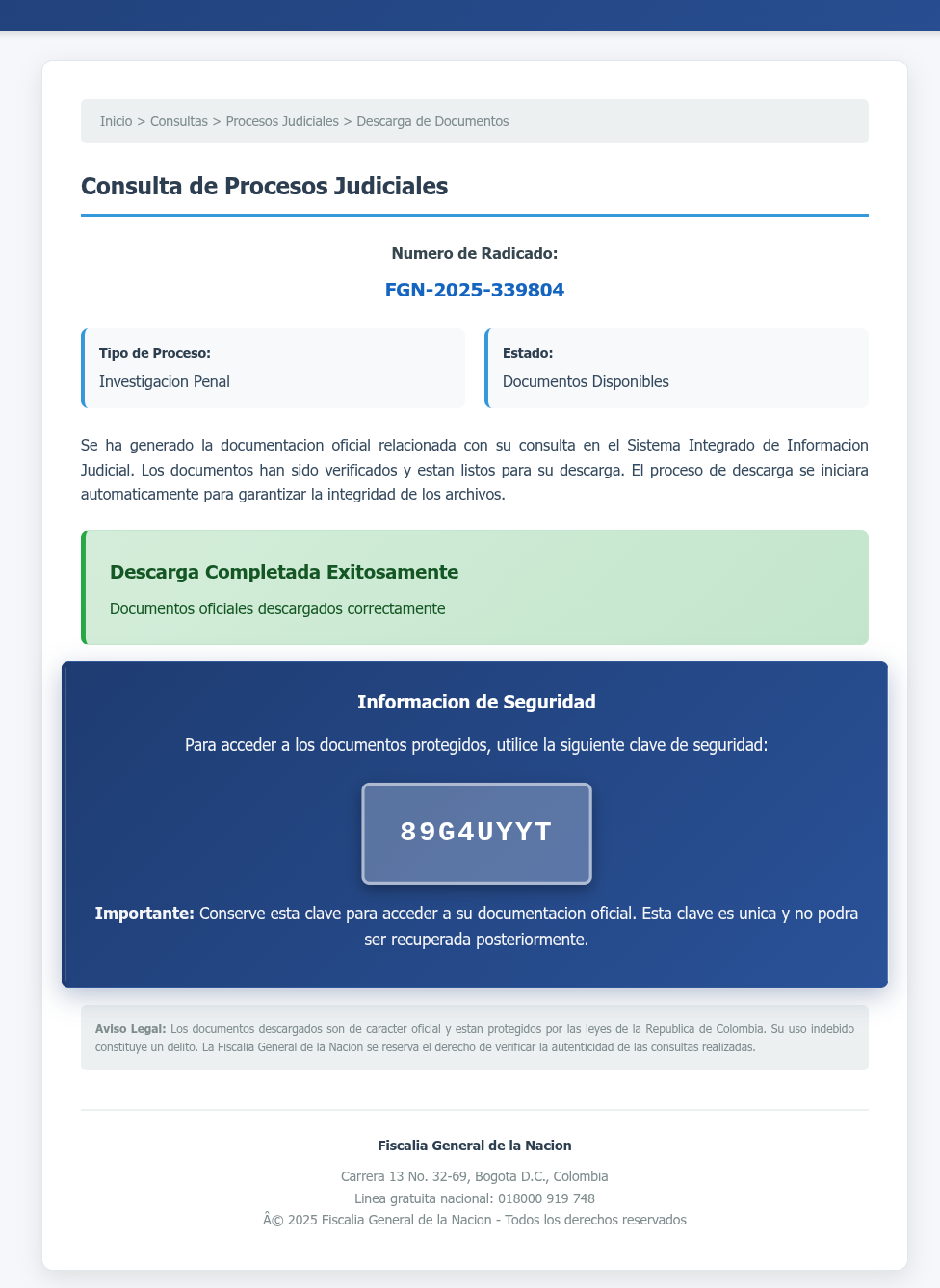
When opened, the file rendered a realistic-looking web portal in-browser, complete with a fake progress bar and download button. That button then delivered a malicious ZIP archive containing a signed Comodo Dragon browser executable, along with a malicious .dll file that would be sideloaded if the .exe was run. This would then install more malware on the system.
The attack relied on a known but often overlooked feature that SVGs support embedded HTML and JavaScript. This means that they can be used like mini web pages — or, as in this case, full phishing kits — even when attached to an email or hosted on cloud storage. VirusTotal’s retrospective scan tied 523 SVG files to the same campaign, with 44 completely undetected by any antivirus engine at the time of submission.
According to VirusTotal’s findings, the source code of these SVGs contained code obfuscation techniques and “large amounts of dummy (garbage) code to increase entropy and evade static detection.”
Not an isolated case
Earlier this year, IBM X-Force documented SVG phishing campaigns targeting banks and insurance firms, and Cloudflare’s Cloudforce One threat team has tracked a sharp rise in SVGs acting as redirectors or fully encoded credential harvesters. Meanwhile, security vendors like Sophos have rolled out new detection rules after finding SVG payloads that bypassed filters.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Microsoft, for its part, is now retiring support for inline SVG rendering in Outlook for the web and the new Outlook for Windows. These will no longer be displayed, and instead, users will see empty spaces where they otherwise would have appeared. This closes off a powerful delivery vector for any attacker hoping to sneak active content into a message body.
For now, users should treat unknown SVG files with the same level of scrutiny they would for any other unknown file.
Follow Tom's Hardware on Google News, or add us as a preferred source, to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button!

Luke James is a freelance writer and journalist. Although his background is in legal, he has a personal interest in all things tech, especially hardware and microelectronics, and anything regulatory.
-
bit_user Reply
I always thought it was a bad idea to allow them to embed Javascript. Let the web page host the script and it can animate the SVG externally or generate parts of it on-the-fly.The article said:Scalable vector graphics (.svg) files are lightweight, XML-based images that render at any resolution. They’re usually harmless, but they can also contain active code
Same thing happened with PDF. It started out as a static format (in contrast to Postscript, which it was intended to replace). However, they apparently couldn't resist the urge to add scripting to it. -
snemarch ReplyThe attack relied on a known but often overlooked feature that SVGs support embedded HTML and JavaScript.
What the actual f?
There's no good reason – none, whatsoever – to be able to inline ANYTHING in an SVG 🤦♂️🤦♂️🤦♂️
Is this an actual part of the SVG spec, or abusing XML engines used to parse them? -
bit_user Reply
I think they wanted to make SVG files animated. Perhaps the idea was even to make them them an open standards-based competitor to Macromedia/Adobe's Shockwave/Flash (SWF), which even have interactivity.snemarch said:What the actual f?
There's no good reason – none, whatsoever – to be able to inline ANYTHING in an SVG 🤦♂️🤦♂️🤦♂️
Nah, I think it got weaseled into SVG 2.0 or something. It's standard, though.snemarch said:Is this an actual part of the SVG spec, or abusing XML engines used to parse them?
: ( -
snemarch Reply
Bloody stupid. HTML + JS + SVG, sure. Embedding the other technologies in SVG? 🤦♂️🤦♂️🤦♂️bit_user said:I think they wanted to make SVG files animated. Perhaps the idea was even to make them them an open standards-based competitor to Macromedia/Adobe's Shockwave/Flash (SWF), which even have interactivity.
Web technologies are such a cluster of really, really bad decisions. -
pjmelect As far as I know I have never encoutered an svg image. where would you commonly find them?Reply -
bit_user Reply
They're used on some web pages and supported as a file format by some vector drawing programs.pjmelect said:As far as I know I have never encoutered an svg image. where would you commonly find them?
One example I can give you is the benchmark charts on Phoronix, such as in this article:
https://www.phoronix.com/review/linux-515-617-performance
If you right-click on one of those charts and open it in a new tab, you'll see in the address bar that it ends in a .svgz extension, which means it's a zipped SVG file (e.g. https://www.phoronix.com/benchmark/result/amd-epyc-7773x-linux-kernel-benchmarks/postgresql-100-1000-read-write.svgz).
What's neat about them being SVG files is that you can copy-paste embedded text from them or use your browser's zoom feature to enlarge the graph without it ever becoming blurry. They also might be smaller than the equivalent PNG file.
The drawback is basically that they're often slower to render than a .PNG would be, but modern computers are fast enough that it's basically a non-issue for SVG files of reasonable complexity. -
ravewulf Instead of completely disabling SVG, couldn't they just disable running embedded content in the SVG parser (keep only the basic lines, curves, shapes, text, and styling)?Reply -
ezst036 Reply
I think there are some SVG images on Wikipedia.pjmelect said:As far as I know I have never encoutered an svg image. where would you commonly find them? -
JohnyFin SVG is save but people are carelles...to be infected you must first download exe or zip file and then open it! Most web browsers block exe to download (to allow it you must know where to click ...and most people do not know it how) also exe downloading is blocked by company where people works by secure policy. thats attack happen in bananas countries ...Reply -
jp7189 Reply
Svg would be strongly preferred (if not required) by people that make ads, business cards, hats, shirts, and pretty much anything else that transfers a digital file to a physical "thing".pjmelect said:As far as I know I have never encoutered an svg image. where would you commonly find them?
They are very common in media and marketing because they don't degrade in quality no matter how big you blow them up. The data isn't stored as a fixed array of pixel as in other image formats, but instead as vectors. A logo on a business card and a logo on a billboard will look the same (not pixelated). Ya know how some people have their company logo in their email sig? I'm sure there are folks that would opt to use the svg format for that.