3.8 GHz P4-570 and E0 Stepping To End Intel's Performance Crisis
The E0 Stepping Is Available Now
All the Pentium 4 processors designed for Socket 775 will eventually be transitioned to the E0 stepping, though not every version will necessarily incorporate all of the new features.
The first feature is the XD bit (execute disable), which allows memory zones to be flagged as non-executable. The major motivation for this is virus protection, since when flagged as non-executable, program code that has been illegally written by causing a buffer overflow will no longer be able to be executed. XD-enabled processors will be identified by the suffix "J".
The second feature is the upgrading of the processor's halt state mode from C1 to C1E. Windows NT 4.0 provides a so-called idle task that enables HALT whenever there is nothing to do; in this situation, parts of the CPU will be temporarily disabled in order to reduce heat generation. In addition, C1E now is capable of altering the CPU clock speed and the core voltage.
The third feature is extended Thermal Monitoring. The original version, available since the P4 Willamette, is able to stop the clock momentarily to avoid over-limit core temperatures damaging the processor. The drawback, of course, is that program execution is slowed down noticeably, in exchange for preventing the system from crashing. Thermal Monitoring 2 is an enhancement that not only leaves out clock cycles, it actually reduces the processor clock and voltage using the same feature that powers Enhanced Halt State.
Safety By Means Of Execute Disable Bit
Buffer overflows are a common threat on Windows systems. This threat arises due to the fact that there is no perfect software. Consider for example the passing of a variable. If a malicious program gets the opportunity to pass an over-size value to a function, that value may overwrite other memory areas. If that overwritten area already contained executable code, the malicious program can modify that code and wreak havoc.
The normal way to prevent these buffer overflows is for software to check the value of each passed value before working with it. Unfortunately, few software developers have both the time and the vision to think about all the possible exceptions and handle them gracefully.
Thus, hardware solutions can be very valuable. As mentioned above, memory areas on the new 570 containing code that is not meant to be executed can be flagged using the processor's XD bit. Windows XP is aware of this feature if Service Pack 2 is installed; it will prevent the execution of code placed by malicious code designed to cause a buffer overflow.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
All AMD64 processors have come with an equivalent feature since they were launched, but there is no execution prevention for the socket A platform. AMD calls its feature NX or Non-eXecute, while it is called EDB (Execute Disable Bit) under Windows. But be careful: while Service Pack 2 adds this feature to Windows XP, Windows Server 2003 users will have to wait for EDB support until Service Pack 1 is released.
In some situations, Windows needs to be told that certain non-EDB-compatible programs are in use and need to be excepted from the feature so they remain functional. The best solution is to use the following Windows option.
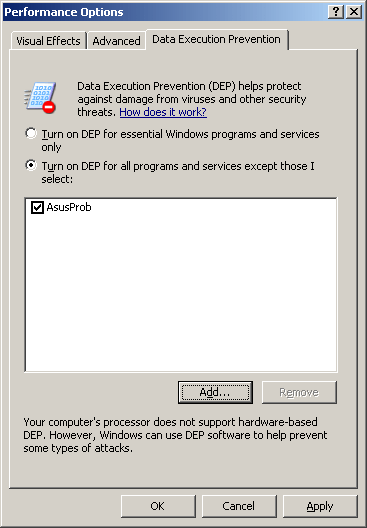
Here, applications that have not been designed for XD and have problems with the feature can be specified. Windows will continue running them as if the XD feature wasn't there.
Current page: The E0 Stepping Is Available Now
Prev Page Pentium 4 Processor 570 Next Page Enhanced Halt State (C1E) Reduces Clock SpeedMost Popular

