Harden Up: Can We Break Your Password With Our GPUs?
Security: WinZip And WinRAR
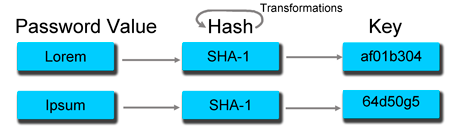
Passwords don’t directly unlock encrypted files. You need to generate a decryption key from the original password, and that's exactly what we've been doing over the past several pages. This is the bottleneck for brute-force attacks. Key derivation accounts for 99% of the recovery process, so throwing the right amount of hardware at that brick wall is really the only way to chisel it down.
While WinZip and WinRAR both use SHA-1 transformations to derive keys, the mechanism is a little different for each program. WinZip is based on PBKDF2 (Password-Based Key Derivation Function 2.0), and it uses 2002 SHA-1 transformation invocations to generate a key. However, this value is constant for any password length (up to 64 characters), which is why a 10-character password is just as easy to defeat with AES-256 as it is with AES-128.
In comparison, WinRAR uses its own key derivation scheme that requires (password length * 2 + 11)*4096 SHA-1 transformations. That’s why it takes longer to brute-force attack encrypted WinRAR archives.
| 2 x GeForce GTX 570 SLI | ||
|---|---|---|
| Brute-Force Attack In Passwords Per Second | Parallel Password Recovery | Accent Password Recovery |
| Compression: Zip Encryption: AES-128 | 495 133 | 513 936 |
| Compression: Zip Encryption: AES-256 | 496 244 | 513 880 |
| Compression: RAR Normal Encryption: AES-128 | 13 904 | 14 605 |
As a practical matter, you’re much more likely to forget your own password than to have your encrypted file fall into the hands of someone with too much time and hardware. Even if that person did have the best desktop hardware available, the maximum crunch time to find a nine-character password for an AES-128-encrypted file in WinZip already exceeds 1000 years. However, your prospects of password recovery are decent if you have a general recollection of what your password might be.
For example if you know the following about a 10-character ASCII password:
- Starts with e
- Ends with a
- Contains no capital letters
- Contains one !
- Contains none of the following letters: B, C, D, Q, T, U, V, W, X, Y, Z
You would only need to search through 1 trillion possible passwords instead of 205 trillion. That’s a realistic task with a pair of GeForce GTX 570s. If you’re using WinRAR, you almost have no hope of password recovery, unless your password is short.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Security: WinZip And WinRAR
Prev Page Nvidia Versus AMD: Brute-Force Attack Performance Next Page Final Words-
jeff77789 "While it would take a longer time to find a password made up of nine or 10 passwords, it's definitely doable between a few gaming buddies. "Reply
9 or 10 characters? -
ryandsouza "Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "Reply
Sudoku puzzles have numbers from 1 through 9! -
rpmrush This reminds me of Bitcoin GPU crunching. 6990s are favored right now. I wonder how many were sold specifically to Bitcoin miners? I tried it with my dual 6850s but the heat was rediculous. I didn't like the stress on my hardware so I gave up mining. I'm sure it's the same with password software. Maxing out your GPUs. Great for Winter, not Summer!Reply -
mediv42 I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?Reply
-
joshyboy82 I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.Reply -
acku Reply9515787 said:"Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "
Sudoku puzzles have numbers from 1 through 9!
Fixed! Sorry. I usually play Sudoku variants. :)
9515790 said:I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.
I could understand that, but I left out that since I was trying to show a simple example of how permutations differ from combinations. As you pointed out, repetitions are allowed in passwords. I actually mention that in the sentence that follows in the next paragraph. -
webdev511 Password Haystacks Yes Steve Gibson has already covered something like this. Passphrases with upper lower number and speical are the way to go. Yes, please avoid shortcuts.Reply -
acku Reply9515789 said:I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?
It wouldn't be easy from a design standpoint, cause now you're talking about fiddling with the design of the program.
The easiest way to slow down the verification portion of the password authentication process is increasing the number of transformation invocations for key generation. The problem is that this slows down the performance of your machine, even if you have the correct password.
jj463rdHow about adding some extended ASCII codes to a password.
That assumes WinZip and WinRAR supports them. To be honest, I haven't looked into that. Though, I'm inclined to believe that neither program supports them. -
shin0bi272 the tables in this review are horrible... they go from lengths of time to number of passwords and theres no discernible notation when they do.Reply