Harden Up: Can We Break Your Password With Our GPUs?
Password Cracking: GPGPU-Style
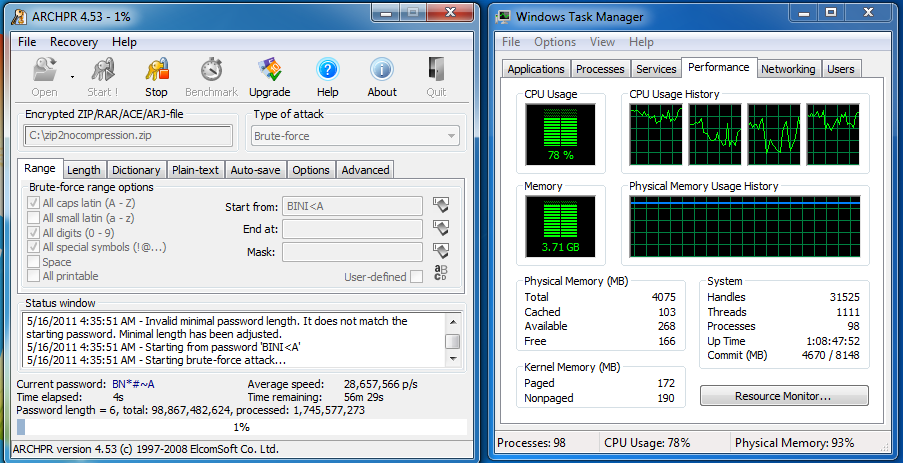
The goal of a brute-force attack is to try multiple passwords in rapid succession. But modern CPUs aren't particularly well-optimized for this. While my Sandy Bridge-based workstation can process about 28 million passwords per second, it still isn't using all of its available CPU cycles. Remember that you're only guessing and checking. The above CPU utilization screenshot shows that, while clock rate is of course going to help, this application is able to take advantage of parallelism, suggesting that even more cores would help accelerate the process.
Well, as we know, when it comes to parallelized tasks, what a CPU can sometimes do well, the ALUs on a graphics card can often do better. AMD and Nvidia had the video transcoding community convinced of this up until Intel proved a little dedicated logic on its Sandy Bridge architecture could vastly outperform a massively parallel graphics processor. But now it looks like we have another potential application for the general-purpose computing capabilities of today's GPUs.
In the past, GPGPU-based password cracking was limited to academia, where graduate students slaved away over custom code that never saw commercial implementation. That's no longer the case. Now there are two GPGPU tools available to anyone with a credit card: Parallel Password Recovery and Accent Password Recovery.
Parallel Password Recovery is solely optimized for Nvidia's CUDA parallel computing architecture. That's not to say CUDA is better than AMD's Stream initiative. However, Nvidia should be given its due credit. Nvidia's foray into general-purpose GPU computing is a much older one, and the company has given developers access to a plethora of the low-level libraries needed to explore the technology. The response from AMD has been much slower. In fact, we still see issues with getting Stream acceleration enabled in popular transcoding apps. This partially explains why the other solution, Accent Password Recovery, still seems to favor Nvidia's design. Though it recognizes CUDA and Stream, only Nvidia hardware is optimized to attack Zip 2.0 encryption.
| Cracking With A GeForce GTX 460 | ||
|---|---|---|
| Brute-Force Attack in Passwords Per Second | Parallel Password Recovery | Accent Password Recovery |
| Compression: Zip Encryption: Zip 2.0 | 24 111 280 | 516 096 000 |
| Compression: Zip Encryption: AES-128 | 185 072 | 166 800 |
| Compression: Zip Encryption: AES-256 | 185 177 | 156 138 |
| Compression: RAR Normal Encryption: AES-128 | 3493 | 4231 |
And boy is there a boost in Zip 2.0 encryption! With a GeForce GTX 460, we're already pushing over 500 million passwords per second. To give you an idea of what that means, we can now crunch every possible combination of ASCII characters from a password length between one and seven characters in less than 48 hours. Moving up to an eight-character password takes about 168 days.
| GeForce GTX 460 | ||
|---|---|---|
| Brute-Force AttackAll ASCI CharactersTotal Time for Search | Password Length Between 1 and 6 Characters | Password Length Between 1 and 8 Characters |
| If You Push 180 000 Passwords Per Second... | 50 days, 20 hours | 1284 years, 79 days |
| If You Push 24 Million Passwords Per Second... | 9 hours, 9 minutes | 9 years, 230 days |
| If You Push 500 Million Passwords Per Second... | 26 minutes, 21 seconds | 168 days, 17 hours |
Of course, Zip 2.0 is rather outdated. WinZip only maintains this scheme for compatibility reasons. AES is the new "it-girl" everyone is fawning over. This scheme is much harder to parallelize, though software developers are certainly trying.
Performance is absolutely hammered once we start trying to recover a password encrypted using the AES cipher. Literally, the mouse cursor on our test system stutters along. Brute-force attacks on AES are clearly slow. To try every possible combination of ASCII characters from a password length of 1 to 7 would take over 13 years.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
| 2 x GeForce GTX 570 SLI | ||
|---|---|---|
| Brute-Force Attack in Passwords Per Second | Parallel Password Recovery | Accent Password Recovery |
| Compression: Zip Encryption: Zip 2.0 | 45 412 290 | 1 492 279 088 |
| Compression: Zip Encryption: AES-128 | 495 133 | 513 936 |
| Compression: Zip Encryption: AES-256 | 496 244 | 513 880 |
| Compression: RAR Normal Encryption: AES-128 | 13 904 | 14 605 |
General-purpose GPU computing is all about parallelism, so if one card's 480 CUDA cores are good, the combined 960 cores from two cards must be better, right?
When we slap two GeForce GTX 570s together and enable SLI, Zip 2.0 encryption starts to look like Play-Doh. Thanks to optimized code, we can push 1.5 billion passwords per second. This is a bit insane. Now we've cut the search time for a one- to eight-character password using all ASCII characters down to almost two months.
Meanwhile, AES security still looks pretty good. If the password is beyond seven characters long, we'll have to spend nearly five years crunching numbers at 500 000 passwords per second.
Current page: Password Cracking: GPGPU-Style
Prev Page Password Cracking: CPU-Powered Next Page Nvidia Versus AMD: Brute-Force Attack Performance-
jeff77789 "While it would take a longer time to find a password made up of nine or 10 passwords, it's definitely doable between a few gaming buddies. "Reply
9 or 10 characters? -
ryandsouza "Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "Reply
Sudoku puzzles have numbers from 1 through 9! -
rpmrush This reminds me of Bitcoin GPU crunching. 6990s are favored right now. I wonder how many were sold specifically to Bitcoin miners? I tried it with my dual 6850s but the heat was rediculous. I didn't like the stress on my hardware so I gave up mining. I'm sure it's the same with password software. Maxing out your GPUs. Great for Winter, not Summer!Reply -
mediv42 I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?Reply
-
joshyboy82 I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.Reply -
acku Reply9515787 said:"Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "
Sudoku puzzles have numbers from 1 through 9!
Fixed! Sorry. I usually play Sudoku variants. :)
9515790 said:I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.
I could understand that, but I left out that since I was trying to show a simple example of how permutations differ from combinations. As you pointed out, repetitions are allowed in passwords. I actually mention that in the sentence that follows in the next paragraph. -
webdev511 Password Haystacks Yes Steve Gibson has already covered something like this. Passphrases with upper lower number and speical are the way to go. Yes, please avoid shortcuts.Reply -
acku Reply9515789 said:I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?
It wouldn't be easy from a design standpoint, cause now you're talking about fiddling with the design of the program.
The easiest way to slow down the verification portion of the password authentication process is increasing the number of transformation invocations for key generation. The problem is that this slows down the performance of your machine, even if you have the correct password.
jj463rdHow about adding some extended ASCII codes to a password.
That assumes WinZip and WinRAR supports them. To be honest, I haven't looked into that. Though, I'm inclined to believe that neither program supports them. -
shin0bi272 the tables in this review are horrible... they go from lengths of time to number of passwords and theres no discernible notation when they do.Reply