Intel HDCP Cracked Using $350 Hardware Kit
An FPGA development board was used in a man-in-the-middle attack in obtaining and transmitting an encrypted signal from an HDMI port.
Researchers from the Ruhr University of Bochum's Secure Hardware Group in Germany have cracked the copy protection system used by HDMI ports: Intel's HDCP, or High-bandwidth Digital Content Protection. In addition to HDMI, HDCP is used to encrypt video signals transferred via DVI, DisplayPort and other connectors.
"In 2010, an HDCP master key, which is intended to form the secret core element of the encryption system, appeared briefly on a website," reads the official press release. "In response, the manufacturer Intel announced that HDCP still represented an effective protection component for digital entertainment, as the production of an HDCP-compatible chip using this master key would be highly complex and expensive."
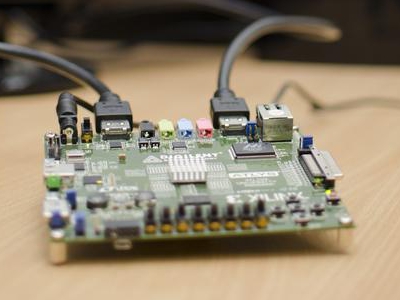
Seemingly taking that as a challenge, the team accomplished the "inexpensive" man-in-the-middle attack by using Digilent's Atlys Spartan-6 FPGA development board. It features a Xilinx Spartan-6 LX45 FPGA (field programmable gate array) in a 324-pin BGA package, two HDMI video input ports, two HDMI video output ports, a 10/100/1000 Ethernet jack, a RS232 serial port and more.
"Our intention was rather to investigate the fundamental security of HDCP systems and to measure the actual financial outlay for a complete knockout," said team leader Prof. Dr.-Ing Tim Güneysu. "The fact that we were able to achieve this in the context of a PhD thesis and using materials costing just €200 is not a ringing endorsement of the security of the current HDCP system."
The $349 USD ($199 Academic price) board serves as the "middleman" by modifying all communications between a Blu-ray player and a flat-screen HDTV without being detected. The team was able to tap the HDCP encrypted data streams, decipher them and send the digital content to an unprotected screen via a corresponding HDMI 1.3-compatible receiver.
Yet as the team points out, this man-in-the-middle attack could allow the end-user to burn films from Blu-ray discs, but recording directly from an HDMI port results in a large amount of data. That said, this method is "of no great practical use for pirates." But Güneysu envisions a real threat to security-critical systems used by law enforcement agencies and the military.
"Although Intel is already offering a new security system, HDCP 2.0, due to the backward compatibility, the weak point will also remain a problem in coming years," he concluded.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Intel and Digilent have yet to comment on the report.

Kevin Parrish has over a decade of experience as a writer, editor, and product tester. His work focused on computer hardware, networking equipment, smartphones, tablets, gaming consoles, and other internet-connected devices. His work has appeared in Tom's Hardware, Tom's Guide, Maximum PC, Digital Trends, Android Authority, How-To Geek, Lifewire, and others.
-
amk-aka-Phantom Good, good. The whole marketing of this HDCP feature as profitable for the user (see image below) sickens me, as does the feature itself. I don't agree with implementing copy protection on hardware level. This might not be fully usable yet, but the effort is already there. I love seeing expensive copy protection systems meant to limit the users go to waste.Reply
-
de5_Roy lawl serves intel right. they're inflating this thing by adding 'security-critical systems used by law enforcement agencies and the military' into hdcp. are the military and law enforcement agencies part of riaa and mpaa who bribed financially endorsed this tech for intel to implement this tech in the first place? nope.Reply -
doorspawn The graphics card: 1) decodes the HDCP data, 2) decompresses it, 3) re-encodes it.Reply
Then it's captured by this MitM attack and decoded.
It seems to me there's a far superior workaround between 1 & 2 waiting to be developed.
-
custodian-1 this goes to a core belief if you try to lock it and no matter how. Soneone will take the time to unlock itReply -
keyanf If Patton lived today, he'd likely add "copy protection" to his "Fixed fortifications are a monument to the stupidity of man" quote.Reply -
icepick314 still funny to see millions of research and development in DRM cracked by mere few dollars...Reply
remember the Sony's music CD protection defeated by just a piece of tape or even a sharpie marker? -
@doorspawnReply
actually if i recall correctly and i maybe wrong, HDMI has a hardware layer, all devices that connect via HDMI is required to implement hardware layer, if i recall the HDCP data never gets trans-coded but rather transmitted as is along with the copy protected material over the HDMI protocol, the receiving device not the transmitting device will then authenticate the HDCP data, what this device does is intercepts the copy protected material and using the master key strips out the copy protection resulting in a stream that is completely copy protected free
it should also be noted that the hardened pirates will have access to TBs of hard disk space as well as machine with hardware accelerated video capture and trans coding devices, large amount of data was rarely ever a deterrent -
kinggremlin doorspawnThe graphics card: 1) decodes the HDCP data, 2) decompresses it, 3) re-encodes it.Then it's captured by this MitM attack and decoded.It seems to me there's a far superior workaround between 1 & 2 waiting to be developed.Reply
Of course there is. As was noted in the article by the developers of this, it has no practical use for pirates. Despite all the ROFLCOPTER $ony OWNED idiocy in the comments, this has nothing to do with copying Bluray movies. No one would use a method like this for copying movies. If you can't afford $10 movies, you can find all the movie rips you want for free at your local torrent site.
This crack has real security implications. Being able to tap secure corporate and military data transmissions creates a legitimate security concern. Gloating over something like this is plainly stupid. This hack serves no practical benefit to the consumer. Granted, since this is a physical hack the person would have to have direct access to the cable carrying the signal, but a real working example is cause for concern.