AMD CPUs See Less Than 10% Performance Drop From Revised Spectre-v2 Mitigations
Spectre-v2 isn't going anywhere soon. VUSec, a group of researchers from Vrije Universiteit Amsterdam, recently discovered Branch History Injection (BHI), a byproduct of Spectre-v2 that affects Intel and Arm processors. According to Phoronix's latest report, while Intel has taken a performance hit up to 35%, AMD's processors got off easy.
AMD utilizes a Retpoline (return and trampoline) protection with its Zen-based processors to mitigate the Spectre-v2 vulnerability. Instead of the standard Retpoline implementation, AMD took the LFENCE/JMP approach, which is more forgiving on Ryzen processors. Unfortunately, Intel (yes, Intel) discovered flaws in AMD's mitigation, prompting the chipmaker to shift to a generic Retpoline model, the same one that Intel chips have adopted.
The transition from LFENCE to generic Retpoline will bring performance repercussions for all of AMD's modern chips. Phoronix highlighted that Linux distributions would allow users to defect back to LFENCE if they wish, but doing so will be a liability on security.
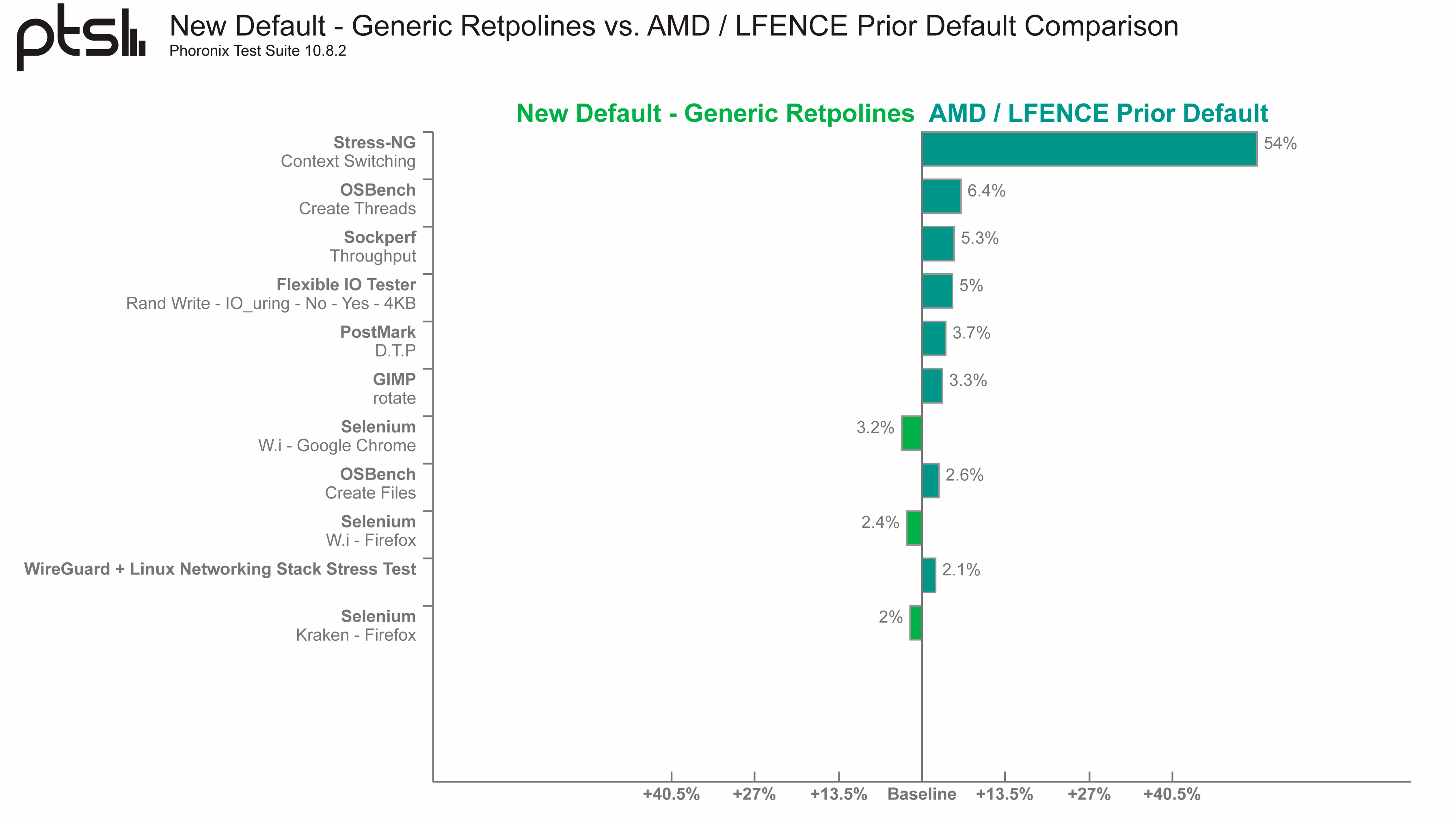
The Ryzen 9 5950X (Vermeer) suffered a 54% performance reduction with the Stress-NG (Context Switching) benchmark. Stress-NG is similar to Prime95 for Windows users, so it isn't the most relevant metric for measuring performance from a consumer workload standpoint. However, the Ryzen 9 5950X held up pretty well besides that specific benchmark. There was only a 5.3% and 5% drop in networking and storage performance, respectively. In comparison, the Core i9-12900K (Alder Lake) experienced performance hits of 26.7% and 14.5% in the networking and storage department.
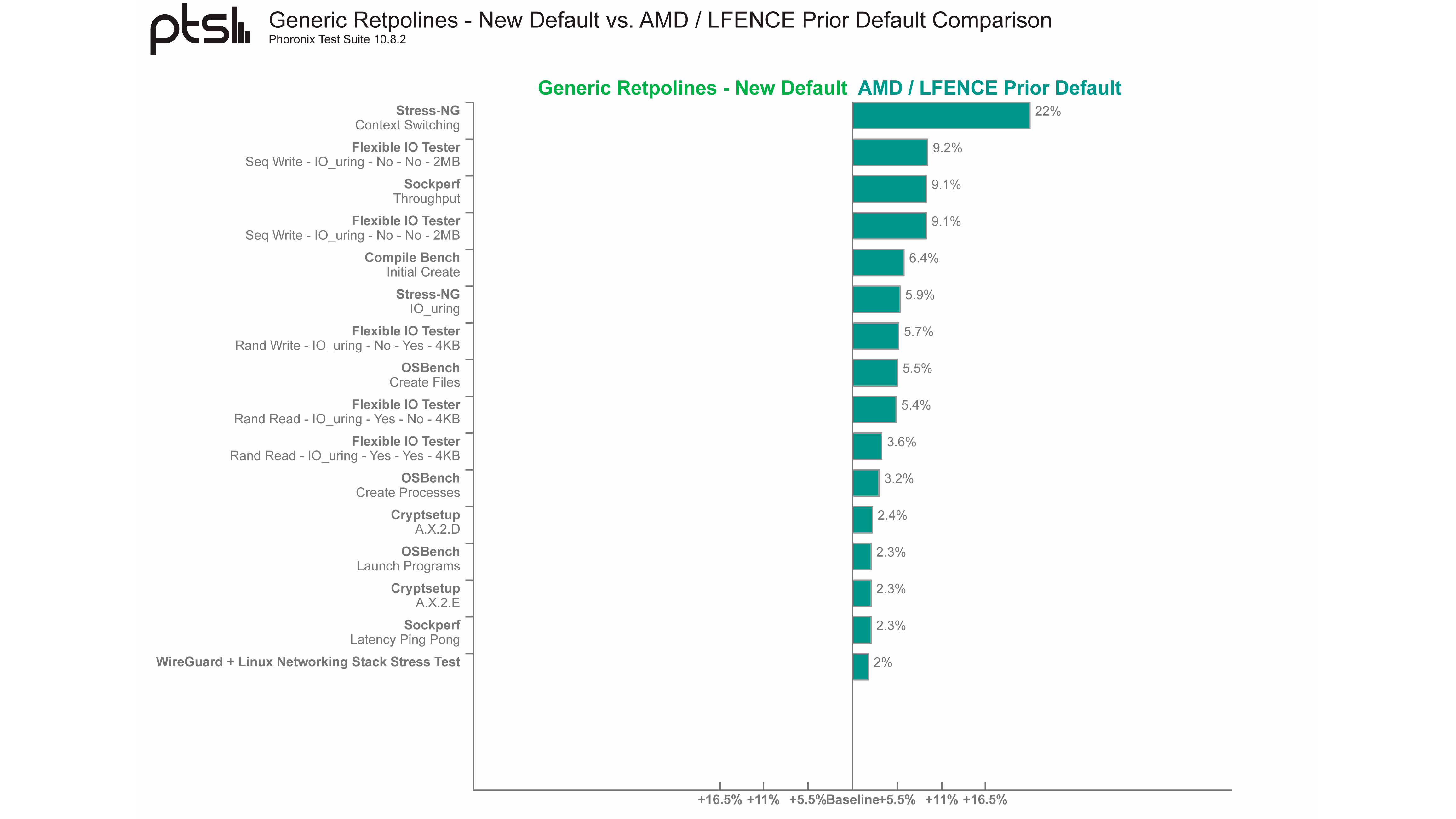
Compared to the Ryzen 9 5950X, the Ryzen 9 5900HX (Cezanne) wasn't affected as much with Stress-NG. The mobile Zen 3 chip only saw 22% lower performance. However, the results revealed a higher toll on networking and storage performance. With the generic Retpoline, the Ryzen 9 5900X took a 9.2% and 9.1% hit in the former and latter, respectively.
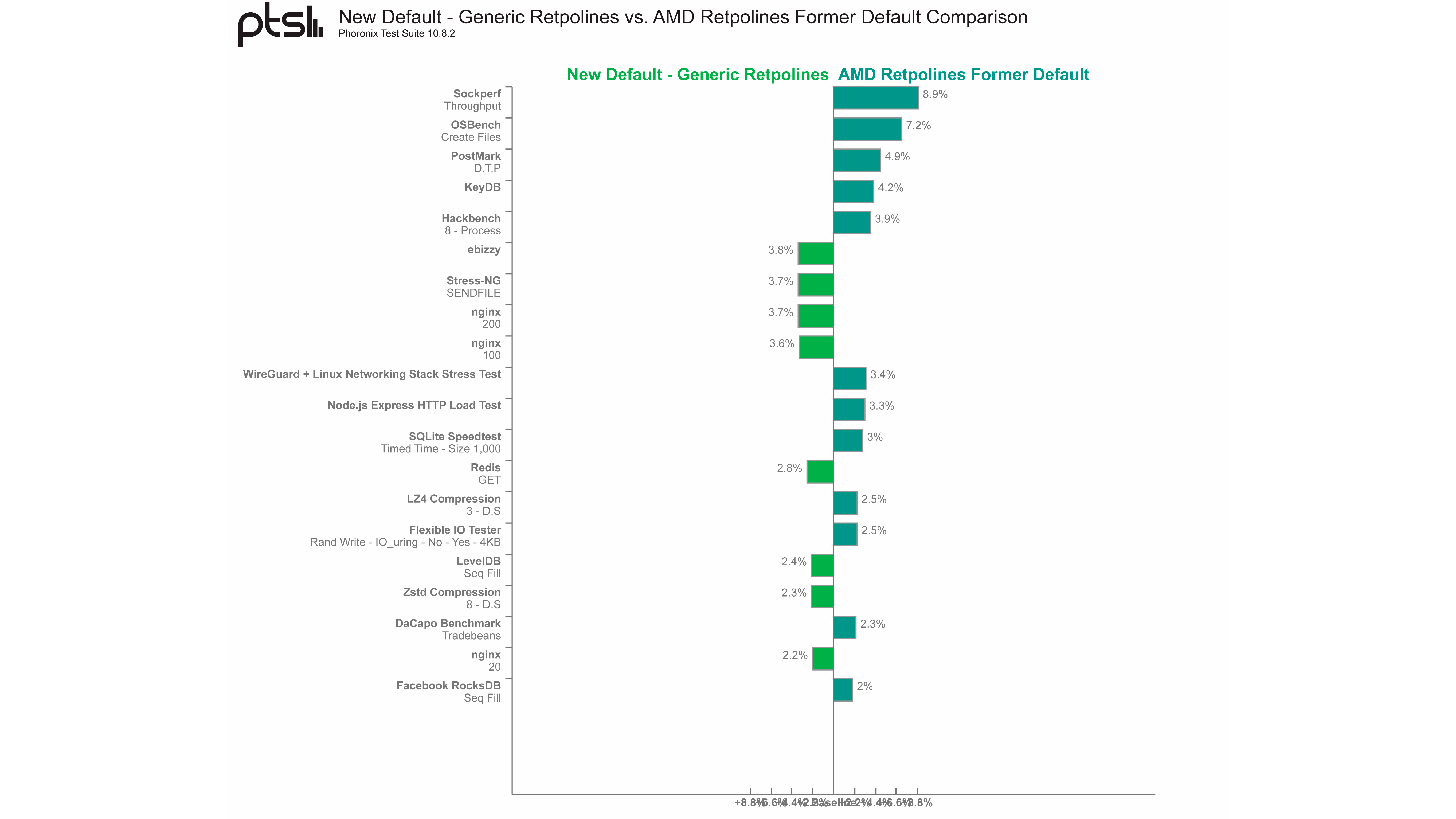
It indeed came as a surprise that generic Retpoline didn't significantly impact AMD's EPYC server processors that handle more intensive I/O workloads. For example, with the EPYC 72F3, Phoronix only logged 8.9% lower networking performance and 7.2% lower storage performance. In addition, some workloads even benefitted from enabling generic Retpoline, showing improvements ranging from 2.2% to 3.8%.
Phoronix conducted its tests in Linux 5.17 kernel, so it remains to be seen if Windows users will experience similar margins regarding performance penalties. As per the publication, Microsoft reportedly will or has patched Windows, so it won't take long for us to find out.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Zhiye Liu is a news editor, memory reviewer, and SSD tester at Tom’s Hardware. Although he loves everything that’s hardware, he has a soft spot for CPUs, GPUs, and RAM.
-
hotaru.hino Reply
Intel discovered AMD's fix for mitigating Spectre flaws didn't work, so they provided a fix, AMD shipped it out, and another website, Phoronix, tested to see how much of a performance loss it causes as it's expected these mitigations will cause some performance loss.ThatMouse said:I didn't understand a single word in the article. Did I miss something?
Unless you're running a data center, any performance loss is minimal on typical user use-cases. -
drivinfast247 Reply
Didn't Intel see a 35% performance loss on the same mitigation?hotaru.hino said:Intel discovered AMD's fix for mitigating Spectre flaws didn't work, so they provided a fix, AMD shipped it out, and another website, Phoronix, tested to see how much of a performance loss it causes as it's expected these mitigations will cause some performance loss.
Unless you're running a data center, any performance loss is minimal on typical user use-cases. -
hotaru.hino Reply
Again, these mitigations only matter if you were running something like a data center or whatnot. The areas where there were major performance hits didn't affect the consumer much if at all. https://portswigger.net/daily-swig/meltdown-and-spectre-one-year-on-feared-cpu-slowdown-never-really-materializeddrivinfast247 said:Didn't Intel see a 35% performance loss on the same mitigation? -
TerryLaze Reply
Not on the same test, in stress-ng the 5950 lost 54% performance while the 12900k only lost 5.1% in that specific one.drivinfast247 said:Didn't Intel see a 35% performance loss on the same mitigation?
As is normal some tests will have a higher impact on one or the other architecture.
The 35% reduction was for the Core i7-1185G7 and osbench.
-
Alvar "Miles" Udell The performance difference overall is -1.5%. Nothing that should concern anyone up through the HEDT segment, though it is terrible to lose performance over a security vulnerability that poses no risk. A server setup though where you're talking dozens to hundreds of CPUs, even 1.5% is a problem, even moreso if your system depends on factors which are impacted much more greatly.Reply
-
STbob If you want the best performance turn them off with inspectre. It can cause issues in online FPS games. Risk of getting hacked is super low.Reply