Cortana Flaw Gave Hackers Web Access on Locked Windows 10 Devices
McAfee researchers announced this week the discovery of a Windows 10 flaw that allowed hackers with physical access to bypass the lock screen and browse the web. The flaw is among several similar Cortana flaws discovered this year.
Cortana's Forced Lock Screen Navigation
According to the researchers, the \flaw they found could allow attackers to do two kinds of unauthorized browsing while bypassing the lock screen. An attacker could force Microsoft’s Edge browser to navigate to a malicious web address. Another method is to use a limited version of Internet Explorer 11 with the user’s saved credentials.
In the first case, the attackers can’t fully bypass the lock screen. However, once they are in possession of the device, they can navigate to a malicious URL, from where they can launch other attacks against the Windows 10 operating system. The attack is done via a simple Cortana voice command.
Israeli researchers demonstrated a similar attack several months ago by exploiting the BadUSB flaw that exists in virtually all USB drives. The attack would inject content into trusted HTTP sites, while using Cortana to force browser navigation. Since then, Microsoft has removed Cortana’s ability to go directly to a web domain; instead Cortana opens an HTTPS Bing web search.
However, McAfee’s researchers found there are still ways to speak to Cortana that resulted in getting sent directly to a web URL. They said if you ask Cortana “Hey Cortana, what is McAfee?,” you would get a Bing search result as a response. But if you say “Hey Cortana, McAfee,” it would send you to a direct link to (usually) a trusted website where you could get a more detailed response. This works with domains such as Twitter, Facebook and Linkedin, but also the “official website” for a company.
The conclusion is attackers can exploit Cortana by asking it to open an “official” malicious website. Hackers could also create “official” entries about a certain company on Wikipedia or other trusted sources, but the researchers didn’t take this path due to ethical issues around manipulating Wikipedia entries. Malicious actors may not be as kind though.
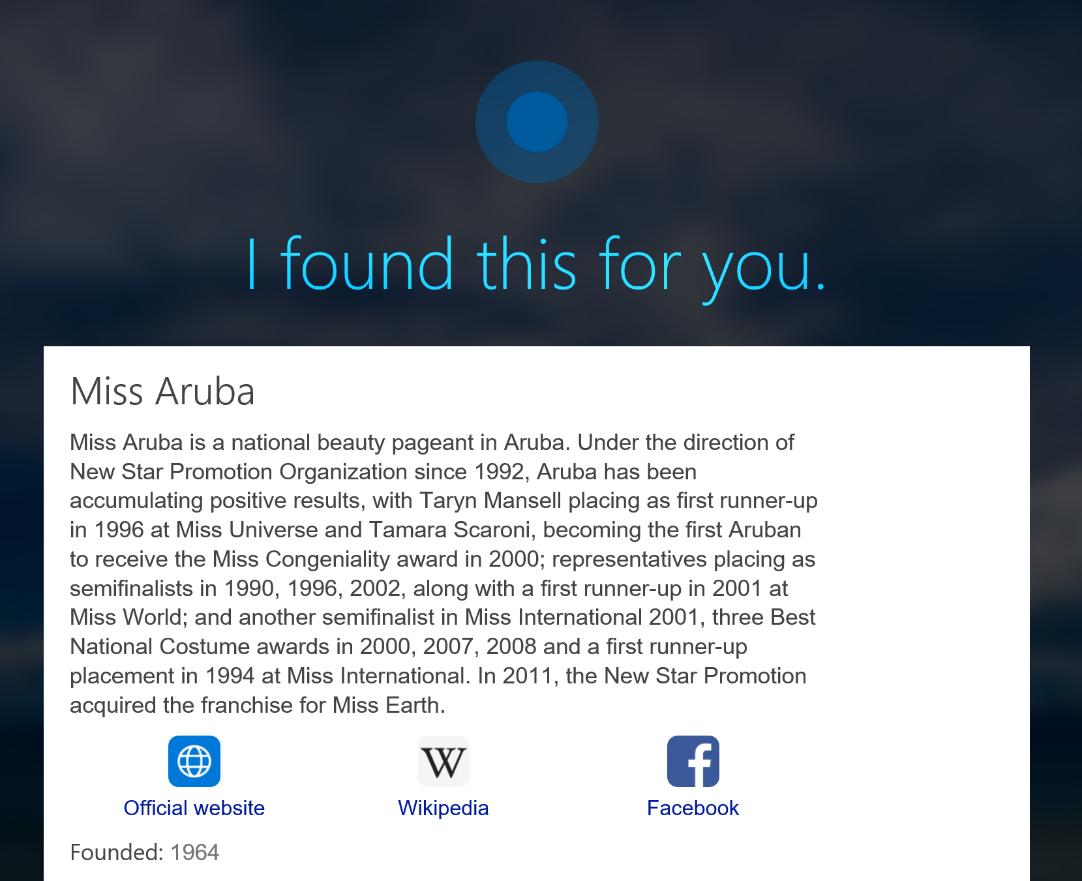
The path the researchers took was to find a Wikipedia entry for which they can purchase a domain, knowing that Cortana would link to that “official” domain. In this case, they bought a domain for the Miss Aruba beauty pageant . They found that the official domain for the contest to which Cortana was pointing was no longer owned by the original owner and could be purchased. This is also how an attacker could abuse certain Cortana queries to send it to malicious URLs and then bypass the lock screen.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Exploiting Cortana’s “Skills”
Cortana offers certain “skills” or applications that can be integrated with it, similar to Amazon Alexa. This expands what the digital assistant can do with the help of third-party developers. However, as McAfee researchers discovered, this also means that Cortana can allow attackers to browse the entire web from the lock screen. In one example, researchers used the “Real estate search” skill to ask Cortana how to sell a house. Cortana would then offer a real estate website login page that also included a link to its privacy policy.
In that privacy policy page, there were links to social media icons, which would lead to their respective social media site. However, once those links were opened in a customized Internet Explorer 11 browser, an attacker could start navigating to other web addresses too. This customized and supposedly limited version of Internet Explorer 11 still gives access to JavaScript, as well as users’ cookies and cached credentials, which means the attacker could also impersonate the owner of the laptop if they gained access to the device.
Digital Assistant Exploitation
These attacks are not the only ones we’ve seen against Cortana lately. In June, McAfee researchers also revealed a full lock screen bypass via Cortana for all Windows 10 devices with Cortana enabled on the lock screen (this is the default for Windows 10 users). Their discovery was part of larger research on what type of access Cortana can provide to a locked Windows 10 device.
Digital assistants like Cortana tend to have more privileges than other operating system applications because normally you want to be able to access them at any time and without too much hassle. However, this is also what makes them exploitable. As the McAfee researchers noted, accessing Cortana from the lock screen doesn’t seem to be worth the trouble. There are too many avenues for attackers to exploit it, plus the researchers may have only scratched the surface.
These two flaws revealed by McAfee researchers have been addressed in the recent Windows 10 August update, but the researchers still recommended users disable Cortana from the lock screen completely to avoid future similar issues.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
kenjitamura Replyhackers with physical access
If a hacker has physical access the person has a whole heck of a lot more to be concerned about than this. -
mikewinddale I can easily imagine a hacker getting physical access: you're a college student who shares a dorm with another student.Reply -
Solandri Reply
You're not thinking big enough. Try a janitor cleaning the room of the CEO of a fortune 500 corporation.21239015 said:I can easily imagine a hacker getting physical access: you're a college student who shares a dorm with another student.
A lot of times, physical access is considered secure if the machine's hardware is locked down (hacker's can't open the case without making it obvious it's been tampered with, hacker can't take the computer without someone noticing it's missing), and the software is blocked with a secure login. Cortana being active when a user is not logged in is a gaping security hole.
The proper fix for this is to neuter Cortana so the only thing it can do if the account is locked or logged out, is to help you login. But that probably gets in the way of Microsoft's data collection. So they force us to live with the gaping security hole. I guess we need to add a locked switch physically disconnecting the microphone cable inside the PC alongside the piece of electrical tape over the webcam.