Intel’s New Spectre-Like Flaw Affects Chips Made Since 2008
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Update, 5/14/19, 1:47pm PT: Added multiple items, posted underneath update note below:
Intel clarified that it's not recommending everyone to disable Hyper-Threading, but that some of its customers should consider the option depending on their security needs:
"Once these updates are applied, it may be appropriate for some customers to consider additional steps. This includes customers who cannot guarantee that trusted software is running on their system(s) and are using Simultaneous Multi-Threading (SMT). In these cases, customers should consider how they utilize SMT for their particular workload(s), guidance from their OS and VMM software providers, and the security threat model for their particular environment. Because these factors will vary considerably by customer, Intel is not recommending that Intel® HT be disabled, and it’s important to understand that doing so does not alone provide protection against MDS."
Google seems to be one of those select customers which considers the risk of keeping HT enabled just too big. The company has published on the Chromium site that HT will be disabled in Chrome OS version 74:
"To protect users, Chrome OS 74 disables Hyper-Threading by default. For the majority of our users, whose workflows are primarily interactive, this mitigates the security risk of MDS without a noticeable loss of responsiveness. Chrome OS 75 will contain additional mitigations."
Original, 5/14/19, 10:06am PT:
Intel unveiled yet another speculative execution side-channel flaw in its processors. The vulnerability affects most of the company’s processor SKUs, except the 8th and 9th generation chips, which Intel said includes hardware mitigations against this flaw.
Microarchitectural Data Sampling in Intel Chips
The Microarchitectural Data Sampling (MDS) issue is a speculative execution side-channel attack that may allow malicious actors to locally execute code in order to extract sensitive data that would otherwise by protected by Intel processors’ architectural mechanisms.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to Intel, four CVEs were assigned to this flaw in Intel’s processors, including:
- CVE-2018-12126 Microarchitectural Store Buffer Data Sampling (MSBDS)
- CVE-2018-12130 Microarchitectural Fill Buffer Data Sampling (MFBDS)
- CVE-2018-12127 Microarchitectural Load Port Data Sampling (MLPDS)
- CVE-2019-11091 Microarchitectural Data Sampling Uncacheable Memory (MDSUM)
Significant Changes to Operating Systems, Core Software Are Required
Intel believes that in order to protect users against this speculative execution issue, Microsoft and other operating system vendors, hypervisor vendors, as well as Intel itself will need to implement significant changes in their software. The solution will involve clearing microarchitectural buffers when switching to software that is not trusted by the previous software.
For instance, every time a processor would switch from one third-party app to another, from a Windows process to a third-party app, or even from less trusted Windows processes to more trusted ones, the buffers would have to be cleared or overwritten. Adding such a significant step in the processing software will most likely lead to a performance loss. How large or small, it remains to be seen, but chances are it could be on the significant side.
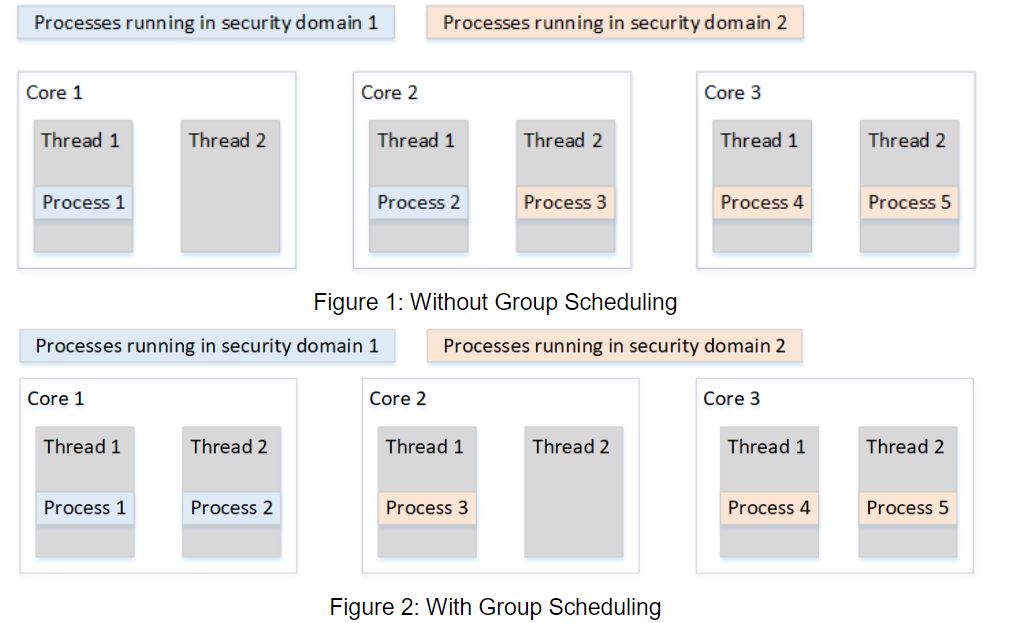
Intel Recommends Disabling Hyper Threading
The company admitted in its white paper that the software mitigations will have a significant effect on how HT works. The threads will need a higher level of isolation between each other, and they will not be able to run processes from different security domains anymore. Threads from different security domains will simply become idle (thus turning into wasted processing power).
It seems that with every other speculative execution attack, Intel’s Hyper Threading becomes either less secure or slower. Intel itself seems to be moving away from Hyper Threading lately on some of its best CPUs, even in the face of AMD competition with both higher number of cores and simultaneous multithreading (SMT) support at similar price points.
Intel has also been publicly reluctant to agree with the disabling of HT when others have called for it with the discovery of some previous CPU flaws, but in its paper, the company stated that disabling HT altogether may be warranted as protection against MDS attacks.
Despite all of these drawbacks, Intel did mention in the white paper that these software mitigations are highly recommended, despite the vulnerabilities being classified only low to medium severity.
Intel noted that future processors will have data sampling methods mitigated in hardware. Some of the company’s current chips could also enable similar mitigations, but only after a microcode update has been loaded. In other words, you’ll rely on your motherboard maker or laptop maker to deliver that update to you, before you can benefit from this mitigation.
Affected Processors
Virtually all of Intel’s chips starting with the Nehalem architecture (launched in 2008, 11 years ago) and newer, with the exception of the Whiskey Lake (ULT refresh), Whiskey Lake (desktop), as well as the Atom and Knights architectures, are affected by the MDS vulnerabilities.
What this tell us is not only that there are now multiple speculative execution attacks against Intel’s processors, or that there will be more to come until a Intel applies a more significant overhaul to its architecture, but that most of these chips will likely never be patched against this flaw and others like it. Motherboard and laptop OEMs tend to update only their most recent products, so the majority of systems sold in the past 11 years will likely remain vulnerable.
Those that do get the patches shouldn’t necessarily consider themselves that much luckier either, as the performance loss after the patches are applied could be significant. Those who buy the new Intel chips starting with Whiskey Lake refresh and later should see a much lower performance loss as well as the security protection from the built-in hardware mitigations, at least until a new speculative execution attack appears that can bypass the new mitigation appears.
Intel has provided more information about the MDS flaws, including about how to get the software patches, on its website.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
jeremyj_83 Another day another Intel security flaw in Hyper Threading. It is really amazing how insecure HT is.Reply -
jeremyj_83 Reply
Not unless you have a Whiskey Lake CPU, which is only on laptops, Atom, or Knights Landing based CPUs.jankerson said:So those with 8th and 9th Generation CPU's are fine. -
jankerson Replyjeremyj_83 said:Not unless you have a Whiskey Lake CPU, which is only on laptops, Atom, or Knights Landing based CPUs.
Intel unveiled yet another speculative execution side-channel flaw in its processors. The vulnerability affects most of the company’s processor SKUs, except the 8th and 9th generation chips, which Intel said includes hardware mitigations against this flaw. -
jeremyj_83 Reply
Affected Processorsjankerson said:Intel unveiled yet another speculative execution side-channel flaw in its processors. The vulnerability affects most of the company’s processor SKUs, except the 8th and 9th generation chips, which Intel said includes hardware mitigations against this flaw.
Virtually all of Intel’s chips starting with the Nehalem architecture (launched in 2008, 11 years ago) and newer, with the exception of the Whiskey Lake (ULT refresh), Whiskey Lake (desktop), as well as the Atom and Knights architectures, are affected by the MDS vulnerabilities.
Coffee Lake and Coffee Lake R are NOT in those lines. Whiskey Lake is an 8th & 9th gen CPU same as Coffee Lake and Coffee Lake R. This is where things are confusing as Intel decided to have things based on different cores all in the same generation line. -
jeremyj_83 Replylogainofhades said:Coffee lake is 8th gen.
Yes it is, but at the end of the article it explicitly states which CPUs are unaffected and Coffee Lake wasn't one of those. Remember Whiskey Lake is also 8th Gen. -
JimJamJamie There's an error in the article:Reply
The vulnerability affects most of the company’s processor SKUs, except the 8th and 9th generation chips, which Intel said includes hardware mitigations against this flaw.
From https://mdsattacks.com/Am I affected?
Very likely. Our attacks affect all modern Intel CPUs in servers, desktops and laptops. This includes the latest 9th-generation processors, despite their in-silicon mitigations for Meltdown. Ironically, 9th-generation CPUs are more vulnerable to some of our attacks compared to older generation hardware.
Processors from other vendors (AMD and ARM) do not appear to be affected. Official statements from these vendors can be found in the RIDL and Fallout papers. -
gggplaya Wow, core i7 people will now have core i5's and core i5's on older laptops will now have dual core i3 computers since they were dual core hyperthreaded parts. OUCH!!!!! However, most people aren't going to care, and just keep on keepin on without worrying about security.Reply