Google Security Researcher Finds Serious Vulnerability In Kaspersky's TLS Interception Tool
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
After previously discovering other vulnerabilities in the Kaspersky antivirus program, Google’s Project Zero security researcher, Tavis Ormandy, has found another puzzling one. The issues lies with Kaspersky’s interception of HTTPS traffic with its own certificate in order to scan for web threats.
Antivirus TLS Interception
The Kaspersky antivirus, just like a few other other antivirus tools, offers users the option (sometimes enabled by default) to allow it to scan within TLS/HTTPS connections, too. Before websites started moving to HTTPS encryption, antivirus or other web analysis tools could just look at the traffic as it was coming into the browser. However, that’s not possible anymore with websites that have encrypted their traffic.
To continue to analyze that traffic, these tools would need to install their own certificates on the users’ computers, and then decrypt that traffic. This is similar to how man-in-the-middle attacks happen. However, the difference is that presumably the users are aware this is happening when they enable the web scanning option in their antivirus programs and that they trust the antivirus companies not to do nefarious things with their web activities.
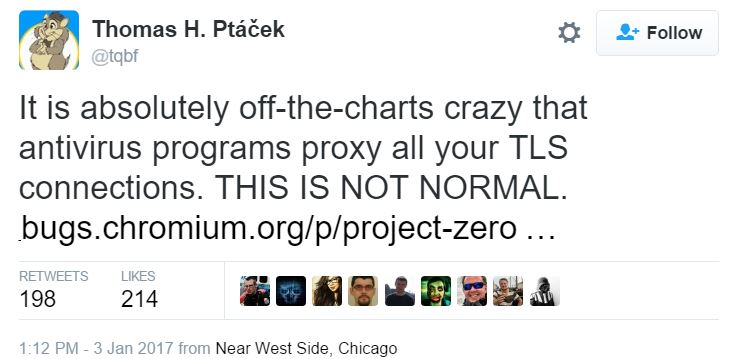
In practice, it’s likely that most users aren’t aware the antivirus software can see their traffic, though, because not everyone is aware of all the intricacies of antivirus and security technologies. Therefore, this “solution” to encrypted web threats may unnecessarily put most users at risk when they don’t know what they’re doing. Some security experts such as Thomas Ptacek believe no antivirus program should be allowed to do TLS interception of all web traffic.
Kaspersky's New Vulnerability
According to Ormandy, the Kaspersky antivirus would install its own root certificate on the user’s computer, and doing it in a way that’s not well protected, either. It would then replace all the visited websites’ certificates with its own generated leaf certificates. So far, this is expected behavior for web scanning tools (although users should still be wary of which tool they allow to do this on their computers).
The problem that Ormandy discovered is that Kaspersky was re-using 32-bit keys for its leaf certificates. This would make it easy for an outside attacker to brute-force a collision and intercept the traffic of multiple sites when Kaspersky users would access them.
The bug would either not allow users to connect to the websites, or the websites would be downgraded to unencrypted HTTP connections, thus allowing attackers to potentially intercept the connections.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to the Google engineer, an attack would go like this:
- Mallory wants to intercept mail.google.com traffic, for which the 32bit key is 0xdeadbeef.- Mallory sends you the real leaf certificate for mail.google.com, which Kasperksy validates and then generates its own certificate and key for.- On the next connection, Mallory sends you a colliding valid certificate with key 0xdeadbeef, for any commonName (lets say attacker.com)- Now mallory redirects DNS for mail.google.com to attacker.com, Kaspersky starts using their cached certificate and the attacker has complete control of mail.google.com.
Ormandy thought it was “incredible” that the Kaspersky team wouldn’t notice that sometimes they would get certificate errors, even if by accident. However, he doesn’t venture to say that Kaspersky may have implemented this vulnerability on purpose.
Ormandy noted that because Google is using its new open source encrypted transport protocol called QUIC for its own services, when accessed from Chrome, Kaspersky is in fact not able to decrypt the Google services connections in Chrome, but it can do it in Firefox or other browsers.
Google's researcher told Kaspersky about the vulnerability on November 1, and the typical 90-day disclosure policy applied. The bug was fixed by the time the 90 days passed. Therefore this particular vulnerability may not put users at risk anymore, but all the issues with antivirus TLS interception remain.
Does Antivirus Software Make You Safer?
The primary reason for using an antivirus tool is to protect yourself against malware that takes advantage of existing and well known vulnerabilities. Some, or perhaps many users don’t update their operating systems or applications on time, which leaves them vulnerable to malware. In such cases, antivirus software could serve a good role of keeping those users safe.
However, for users who always update their operating systems and applications on time, an anti-virus software is much less necessary, because the vulnerabilities that would normally be exploited by malware have been closed.
There are “zero-day” vulnerabilities as well, of course, and by the very definition there's no patch. However, anti-virus software can’t protect you from zero-day vulnerabilities either. Some of them, including the Kaspersky Antivirus, do offer some limited anti-exploit protections, but you may have to balance that with the fact that the antivirus itself may make you less secure.
There likely isn’t a definite answer to whether antivirus software makes you safer. For people who can’t or won’t update their systems, chances are that antivirus software does make them safer. For others, who are always up to date, it may be worth investing more in specialized anti-exploit tools, or even better, sandboxing and other virtualization technologies that wouldn’t allow malware to hurt the main operating system.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
targetdrone The problem these days is malware infected Ads. Use an ad-blocker and avoid any website that asks you to disable the ad-blocker because you might just get infected.Reply
Happened last year when Forbes.com changed it's policies, people disabled their ab-blockers and they were infected from the Ads Forbes used. -
problematiq This was patched on the 28th, As long as your AV is up to date you should be good.Reply -
stranger_3 I personally dont trust any AV software anymore . I think that Governments are forcing them to include backdoors.Reply
I miss the old times of clean internet. -
lun471k You mean the old times when everyone ended up with 15 browser toolbars on their 800x600 resolution screen ? I don't remember a time where the 'modern' Internet with a decent GUI was considered safe.Reply -
targetdrone Reply19109370 said:You mean the old times when everyone ended up with 15 browser toolbars on their 800x600 resolution screen ? I don't remember a time where the 'modern' Internet with a decent GUI was considered safe.
The old days of Acoustic couplers and when 9600 baud was high speed awesomeness. :p -
stranger_3 Reply19109370 said:You mean the old times when everyone ended up with 15 browser toolbars on their 800x600 resolution screen ? I don't remember a time where the 'modern' Internet with a decent GUI was considered safe.
I said "clean" not "safe" , you will never get a complete "safe" communication , but when Governments pushed for backdoors , they opened the worm can ...
Everything changed after 2001 ... when Governments started spying on you with a huge budget , and those backdoors were discovered by smart hackers , The internet lost its coolness .
-
problematiq Reply19111419 said:19109370 said:You mean the old times when everyone ended up with 15 browser toolbars on their 800x600 resolution screen ? I don't remember a time where the 'modern' Internet with a decent GUI was considered safe.
I said "clean" not "safe" , you will never get a complete "safe" communication , but when Governments pushed for backdoors , they opened the worm can ...
Everything changed after 2001 ... when Governments started spying on you with a huge budget , and those backdoors were discovered by smart hackers , The internet lost its coolness .
Didn't really need backdoors in 2001. you be surprised how much traffic even today runs across the wire in clear text.